
Who?
Donato Ferrante
@dntbug
Luigi Auriemma
@luigi_auriemma
2
ReVuln?
Consulting
Penetration Testing
Vulnerability Research
revuln.com
info@revuln.com
@revuln 3

What’s a SmartTV? (1)
4
0Describes a trend of integration of the Internet and
Web 2.0 features into television
0Technological convergence between computers and
television sets and set-top boxes
0SmartTV =a television with integrated Internet
capabilities that offers more advanced computing
ability and connectivity than a contemporary TV
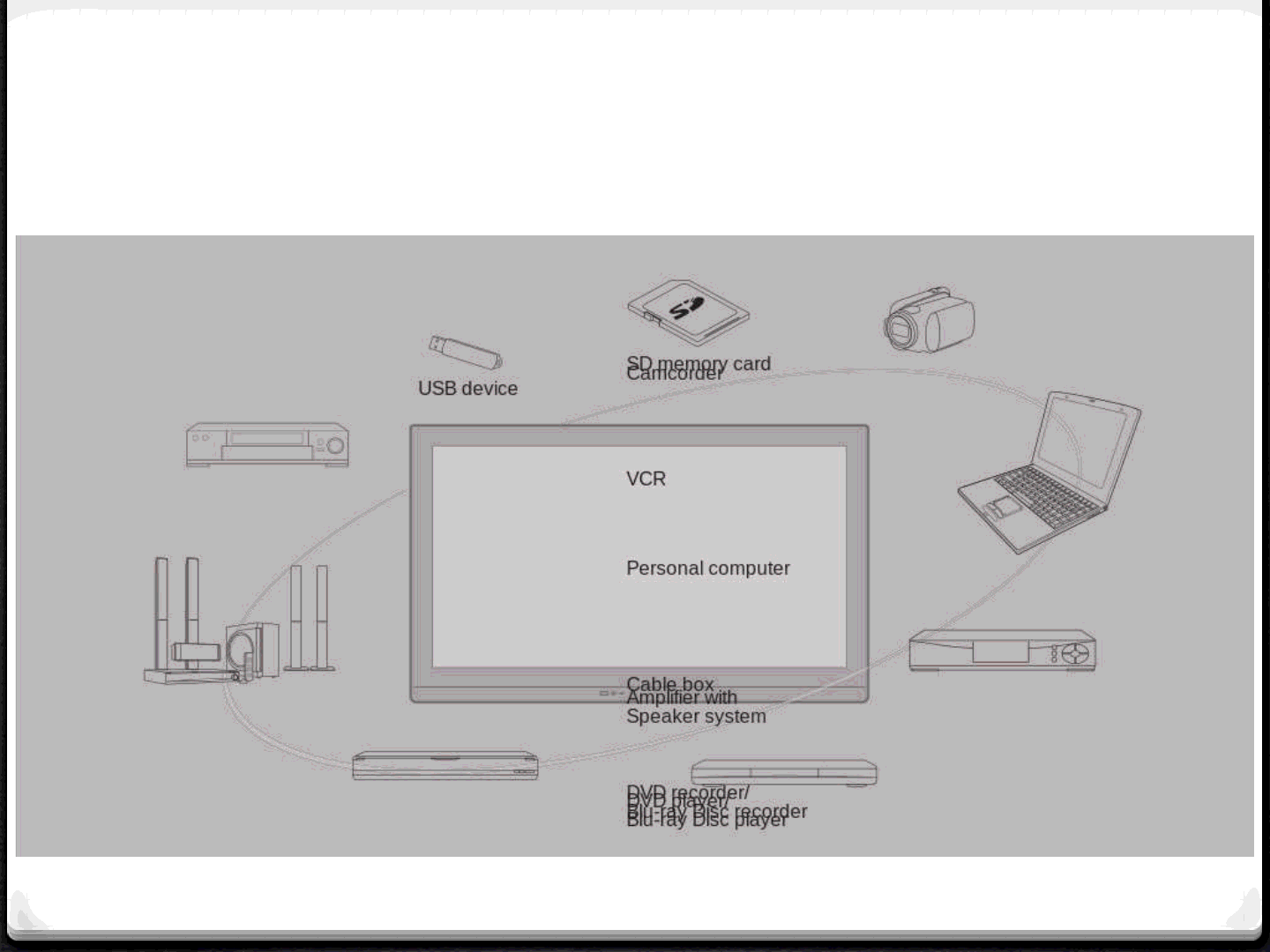
What’s a SmartTV? (2)
5

6
Not all the TVs are SmartTVs…

7
but a lot of TVs are actually SmartTVs

8
SmartTVs at the Airport..

9
And in our hotel room..
SmartTV or not SmartTV, that is the problem..

10
We checked the back
of the TV and it was dark..
So we turned on a flashlight
and..
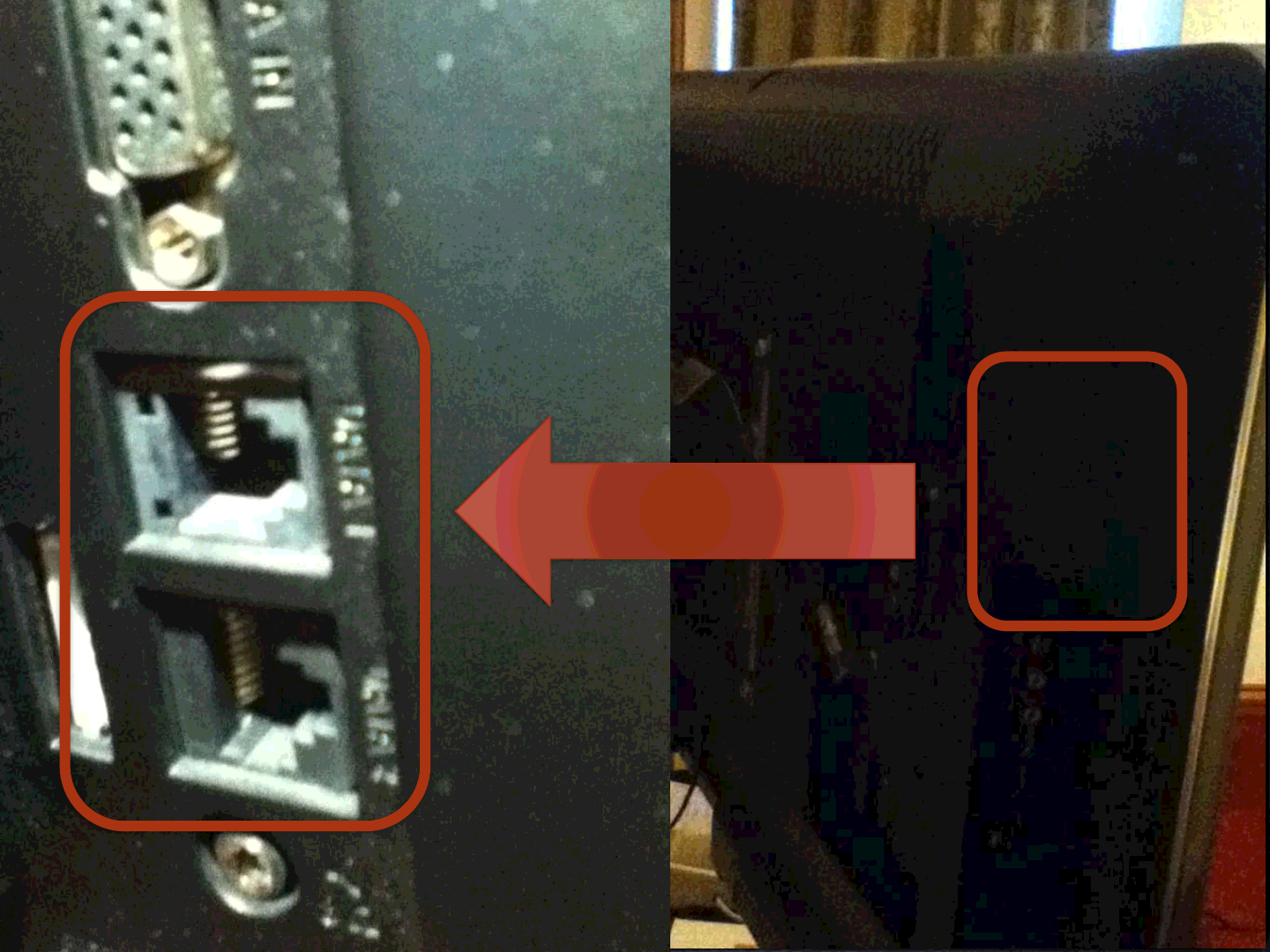
11

Before and After
12
TV SmartTV
Get input signal then output Fully-featured PC
Why are SmartTV so popular?
13

1st Commercial
•If you have to choose between a simple TV and a TV with a
lot of features, even features that you don’t know (but
they sound cool), you will go for the second one
14

2nd Advertising
0Advertising =Money for Vendors/Ads Providers
0Targeted advertising and other advanced advertising
features such as ad telescoping using VOD and PVR,
enhanced TV for consumer call-to-action and
audience measurement solutions for ad campaign
effectiveness
0Bidirectional flow between TV and Ads providers
15

Advertising and Security
16
0This bidirectional flow between TV and Ads provider,
has 2 main consequences:
0Privacy, the viewer is disclosing personal habits
0Security, a man-in-the-middle attack can be pretty
effective to achieve one of the following goals:
0Ads-Hijacking => To influence the viewer
0Vulnerability Exploitation => To get access to the TV

Why SmartTV as Target?
0Used worldwide
0Huge attack surface
0And..
17
TV can see you..
18

TV can hear you..
19

1984
20
0An attacker able to gain access to your
SmartTV can:
0Get access to your Home privacy
0Get access to your Company meeting room
0And more..

The Problem (1): Insecurity
0SmartTV are insecure!
21
The Problem (2): Bad & Obscure
0They rely on bad coding practice and..
0They usually rely on security by obscurity (sigh)
22

The Problem (3): Server & Client
0Affected both by Server-side issues..
0There are several services running and listening for incoming
connections (by default)
0And Client-side issues
0Any of the Apps installed by default can represent a possible attack
vector against the device itself
23
The Problem (4): Updates
0A lot of software installed on the TV..
0Have you ever updated your TV?
0How security fix are pushed on your TV by the Vendor?
0Are you running the latest release of the web browser?24

Nice..
But now tell us how to get a $hell!
25

Things to know.. (1)
0A SmartTV is an expensive hardware device
0Usually > 1000 Euro (47.000 RUB)
0You might “brick” the TV (no longer works)
0Big hardware and software differences between the
TV models, even those of the same vendor
0Multiple names for the same features (i.e. HDMI-CEC*)
26
*http://en.wikipedia.org/wiki/HDMI#CEC

Things to know.. (2)
0SmartTV are usually based on Linux
0Using MIPS and ARM CPU
0Having a number of different embedded stuff including: WiFi,
USB, Camera, Microphone, sensors, etc
0Running a wide range of proprietary and customized software,
with crazy configurations
0Black-box testing means wasting lot of time to get information,
having few control over the TV and limited debugging
27

How to get the Software? (1)
0SmartTV vendors (like Samsung and LG) usually release emulators
and/or SDK for developers willing to create new Apps for the TV
0The idea of using the emulators on the PC to find issues affecting the
TV might sound interesting
0The problem is that the emulator doesn’t usually match the software
running on the real TV
0For example if you find 10 issues in the emulator, probably only 1 or
2 will work on the TV and bugs affecting the TV may not work on the
emulators
0But emulators are good to have an idea of some protocols and how
the code works
28

How to get the Software? (2)
0Via firmware updates
0Don’t need to access the TV
0Thousands of updates available for free on the Vendors
websites
0Usually encrypted with an encryption key defined on a
TV/model base. i.e.: 2 different models of the same vendor
will have 2 different keys
0Require some reverse engineering work to extract the content
29

How to get the Software? (3)
0Via directory traversal
0Needs a vulnerability
0If you can access /proc you have lot of information
0If you can access /dev you can download all the filesystems
0Otherwise you have to guess file/directory names by using some
techniques
30

How to get the Software? (4)
0Via code execution
0Needs a vulnerability
0Full access to files, directory and attached devices!
0Execute whatever commands you want :]
0Bye Bye TV Caveat: You might brick the TV!!!
31

How to get the Software? (5)
0Via JTAG or NAND/SD physical reading
0Hardware solution, you must open the TV and playing with its
content… bye bye warranty
0Not always available or easy to access
0It might cause some trouble to the device
0A lot of effort and only for skilled people
32
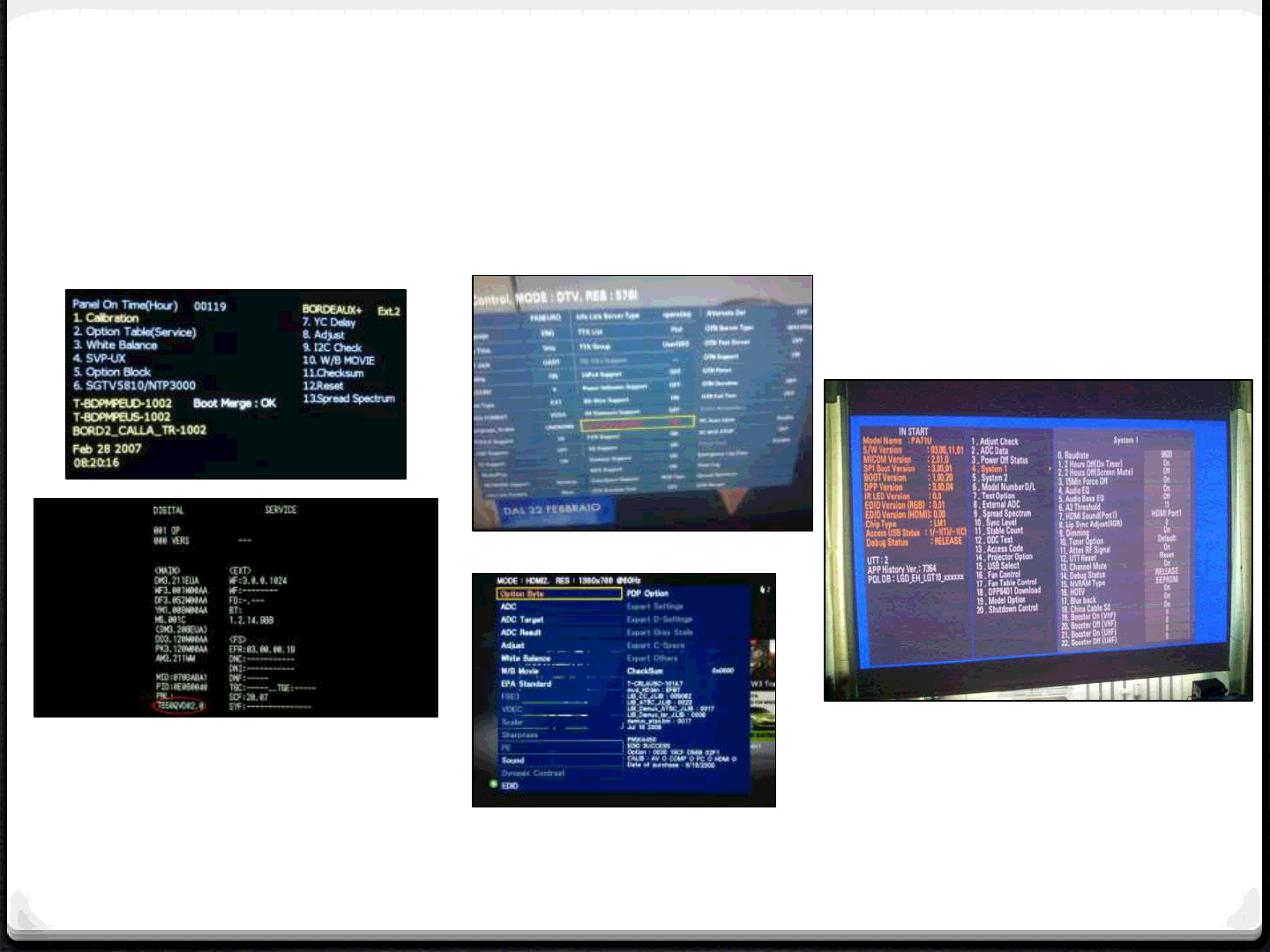
Reset: Service Menu
33
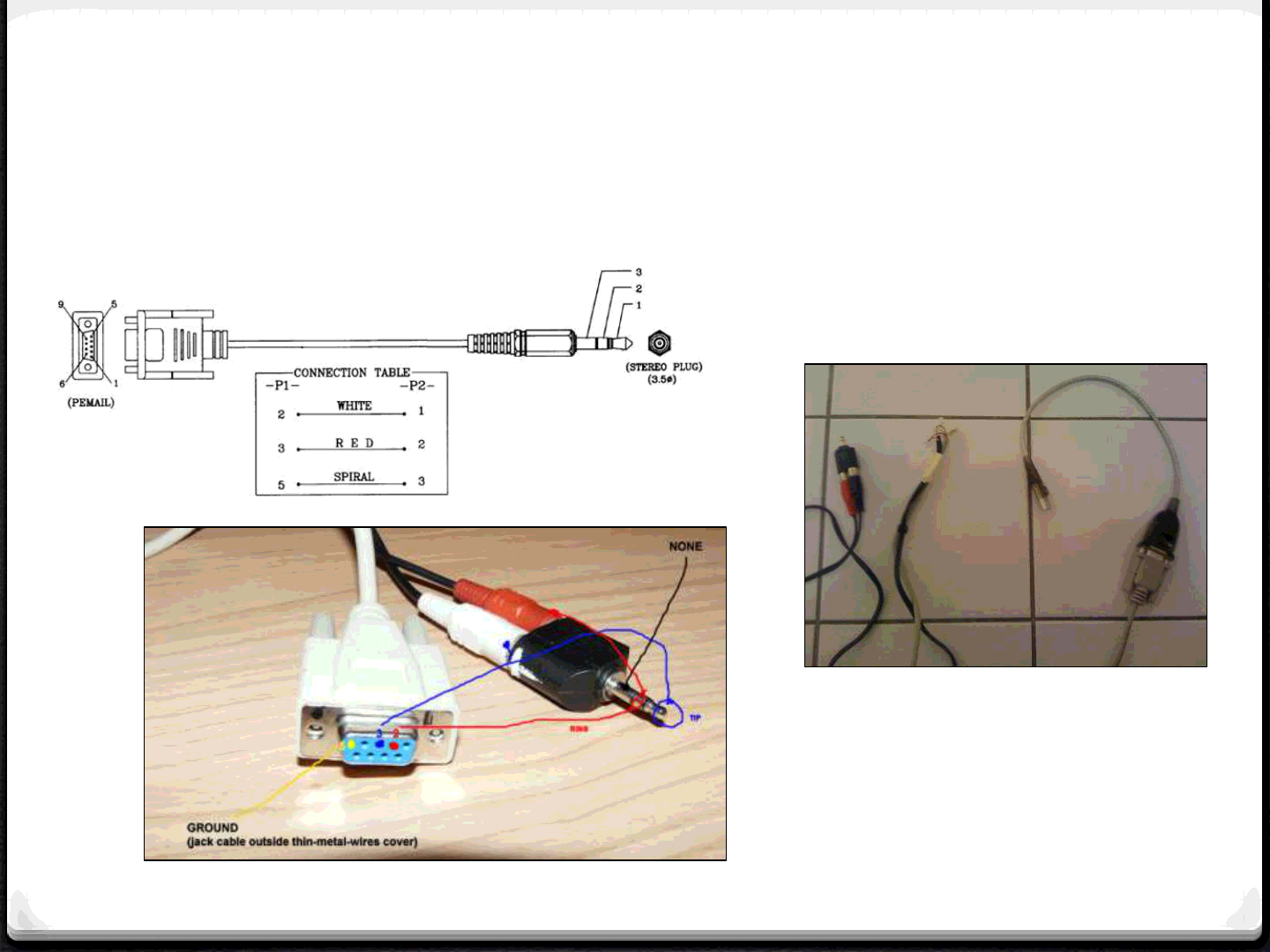
Debug: Serial Cable
34
Samsung
LG
Philips

Attack Surface
0As you might have guessed there are a lot of different ways
to attack a SmartTV
0To get a better understanding let’s take a look at a real
world device
0We will just focus on a subset of the device attack surface
0To do that we take in consideration the following schema
related to a Philips SmartTV…
35
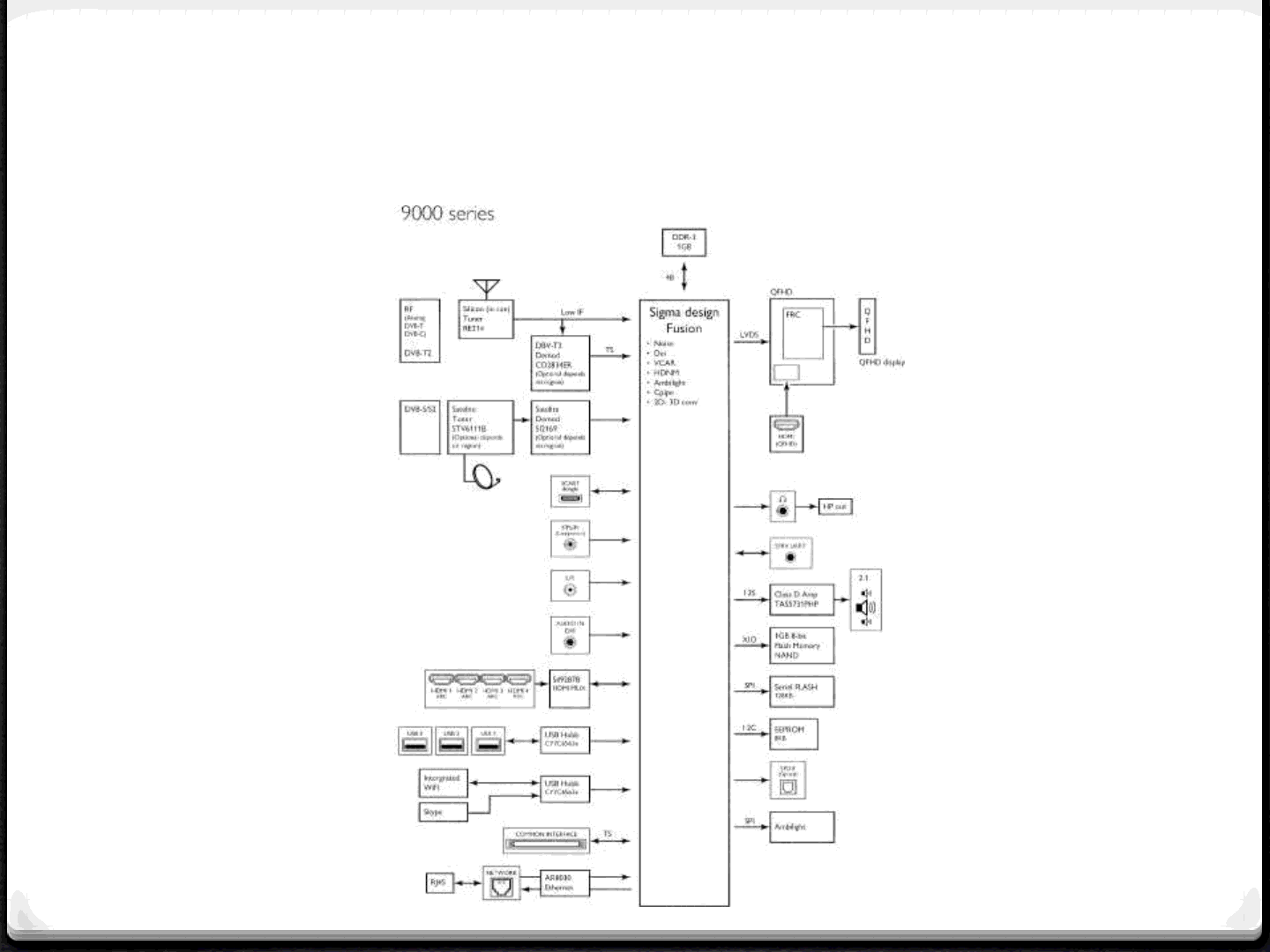
Attack Surface example
from Philips manual
36
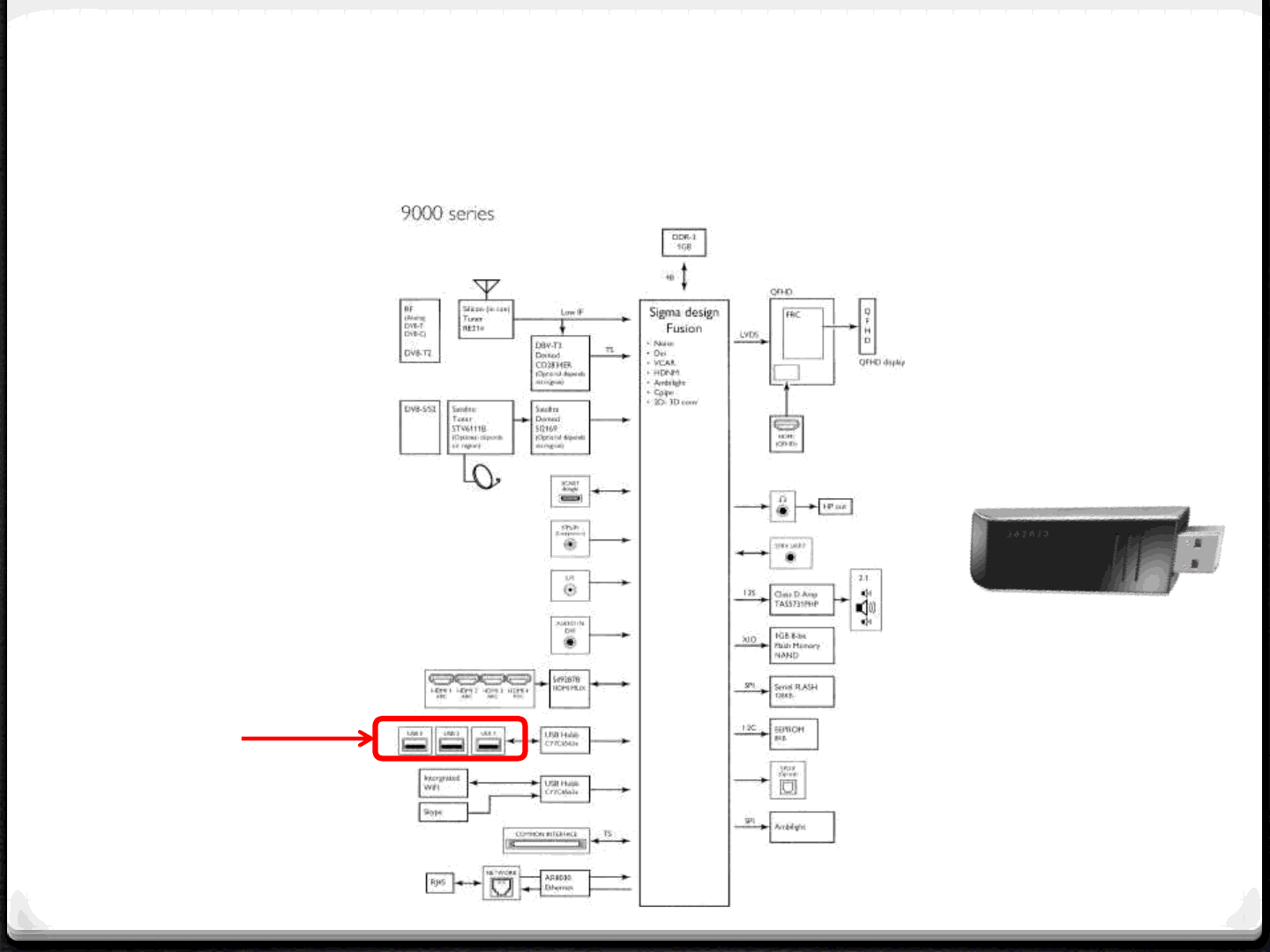
Attack Surface - USB
37
USB
Malicious USB stick containing
malformed data i.e.:
•Video and Audio codecs
•Filesystem
•USB stack
•Auto executed files
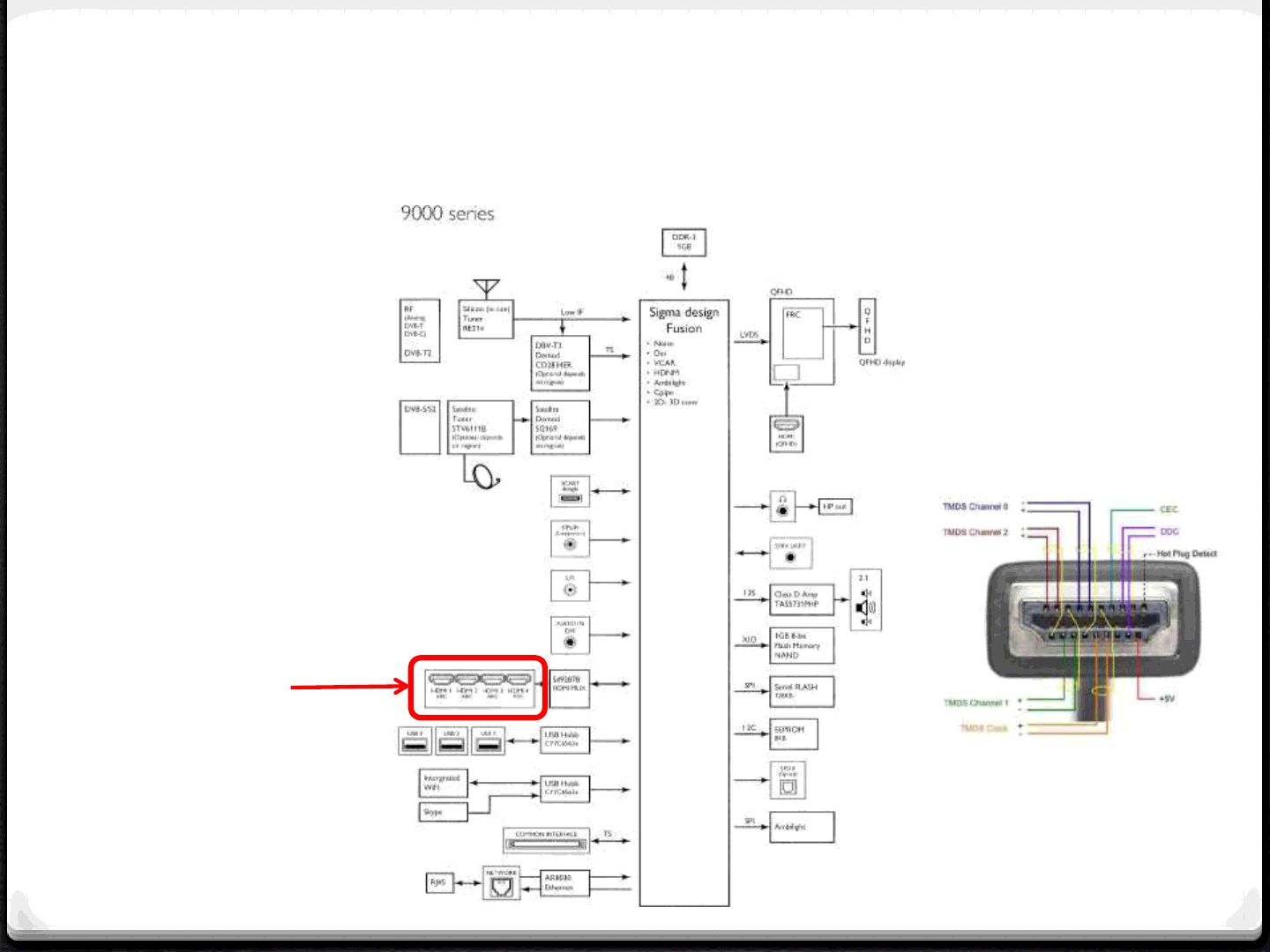
Attack Surface - HDMI
38
HDMI
Communication protocols:
•CEC
•HEC*
for device interoperability
Rogue hardware via
Ethernet connection (HEC)
*HEC is not that popular, not clear how many devices are using this standard..
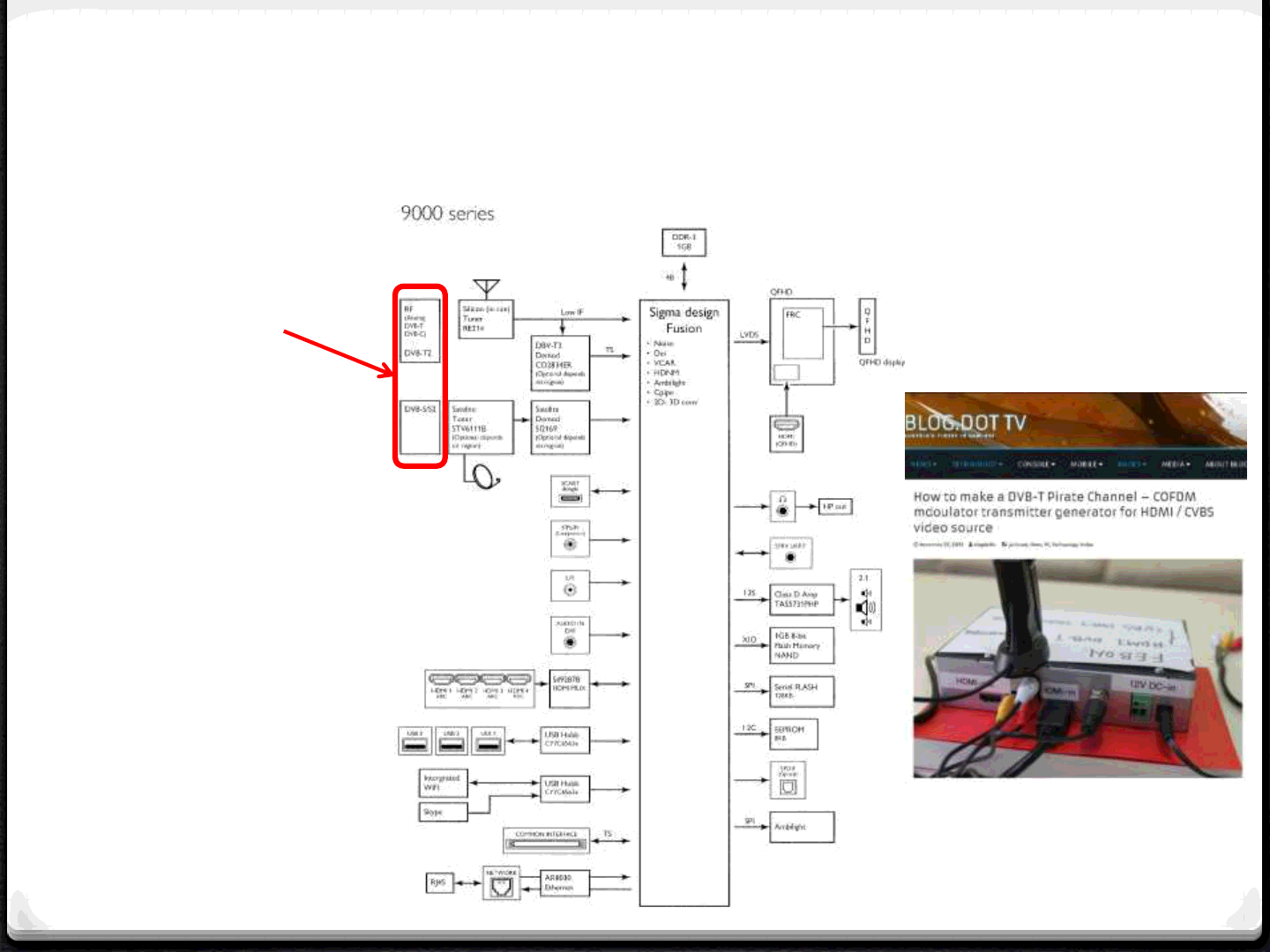
Attack Surface - DVB
39
DVB
Radio signal to the TV
DVB != Analog
It’s a protocol, which allows
using different codecs to decode
the video/audio streams
Different standards:
•DVB-T (terrestrial)
•DVB-C (cable)
•DVB-S (satellite) Homemade DVB transmitter

Wait! Before we forget..
0The DVB audio/video streams are a possible fuzzing
target:
0HEVC, H.262, H.264, AVS, MP2, MP3, AC-3, AAC, HE-AAC
0But the embedded interactive content is the best way
to attack the TV:
0HbbTV
0CE-HTML
0MHEG
40
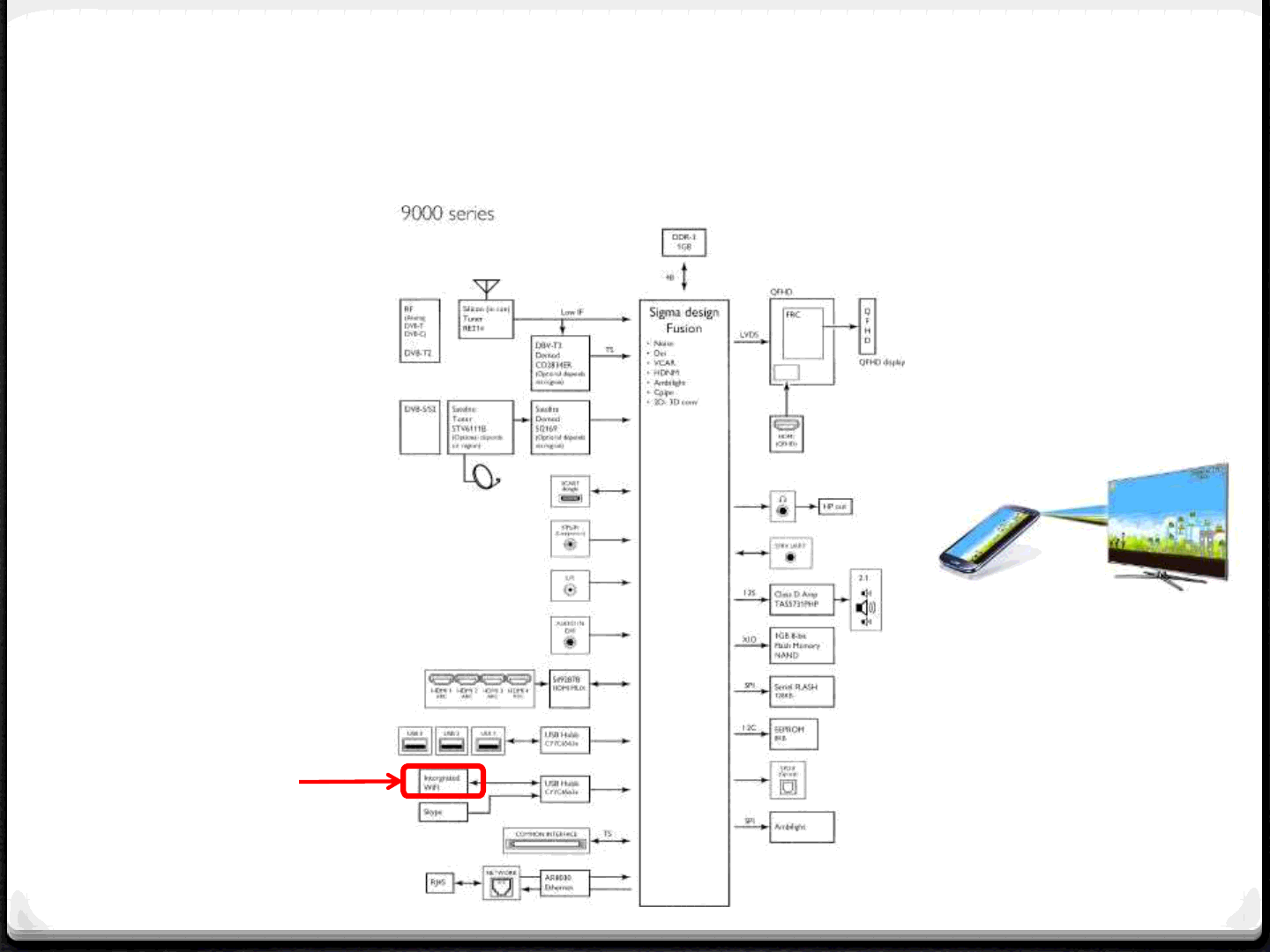
Attack Surface - WiFi
41
WiFi
WiFi adapter of the TV acting as
access-point listening for WiFi
connections.
The Miracast protocol
is composed by out-of-band
WiFi packets, protocols
and codecs
A vulnerability in
Miracast allows the
attacker to access
the TV from
outside your house
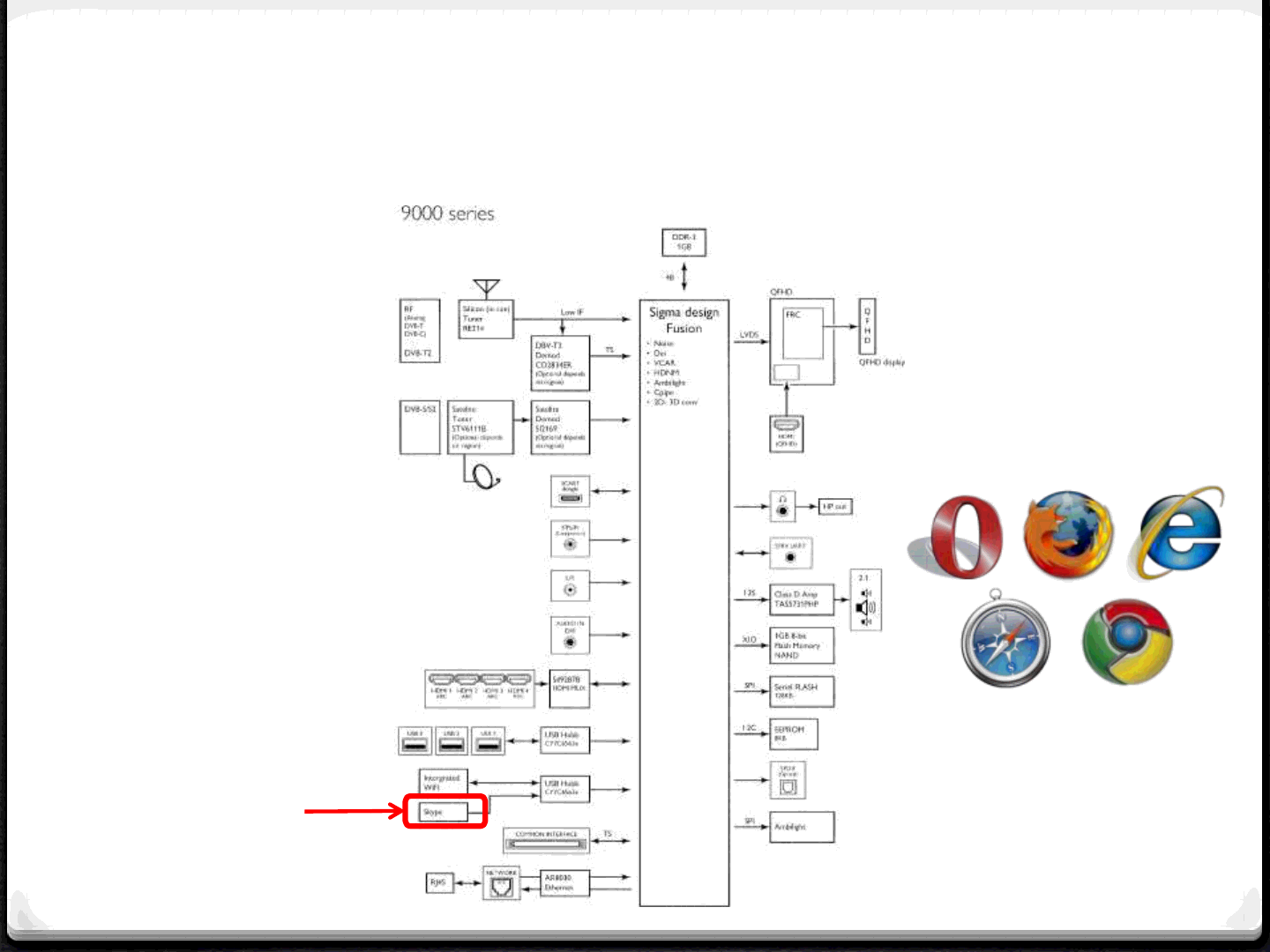
Attack Surface - Apps
42
Apps
Vulnerabilities affecting Apps on
the TV:
•Skype
•Web browser
•Malicious Apps

Attack Surface - LAN
0Most of the SmartTV issues are related to services exposed via LAN:
0UPNP
0Video/Audio service (like DirectFB)
0Various HTTP/HTTPS servers
0Network remote controller
0Media sharing
0Status and information
0First thing to try on your SmartTV is using NMAP:
0You will see a number of different TCP and UDP ports open
0Some of them awaiting for you to connect :]
0If you try to send some junk data to these ports you might get some easy way to
crash/reboot the TV, a starting point to investigate
0The TV also scans the LAN, an attacker can passively exploit vulnerabilities
43

Real World Issues
44
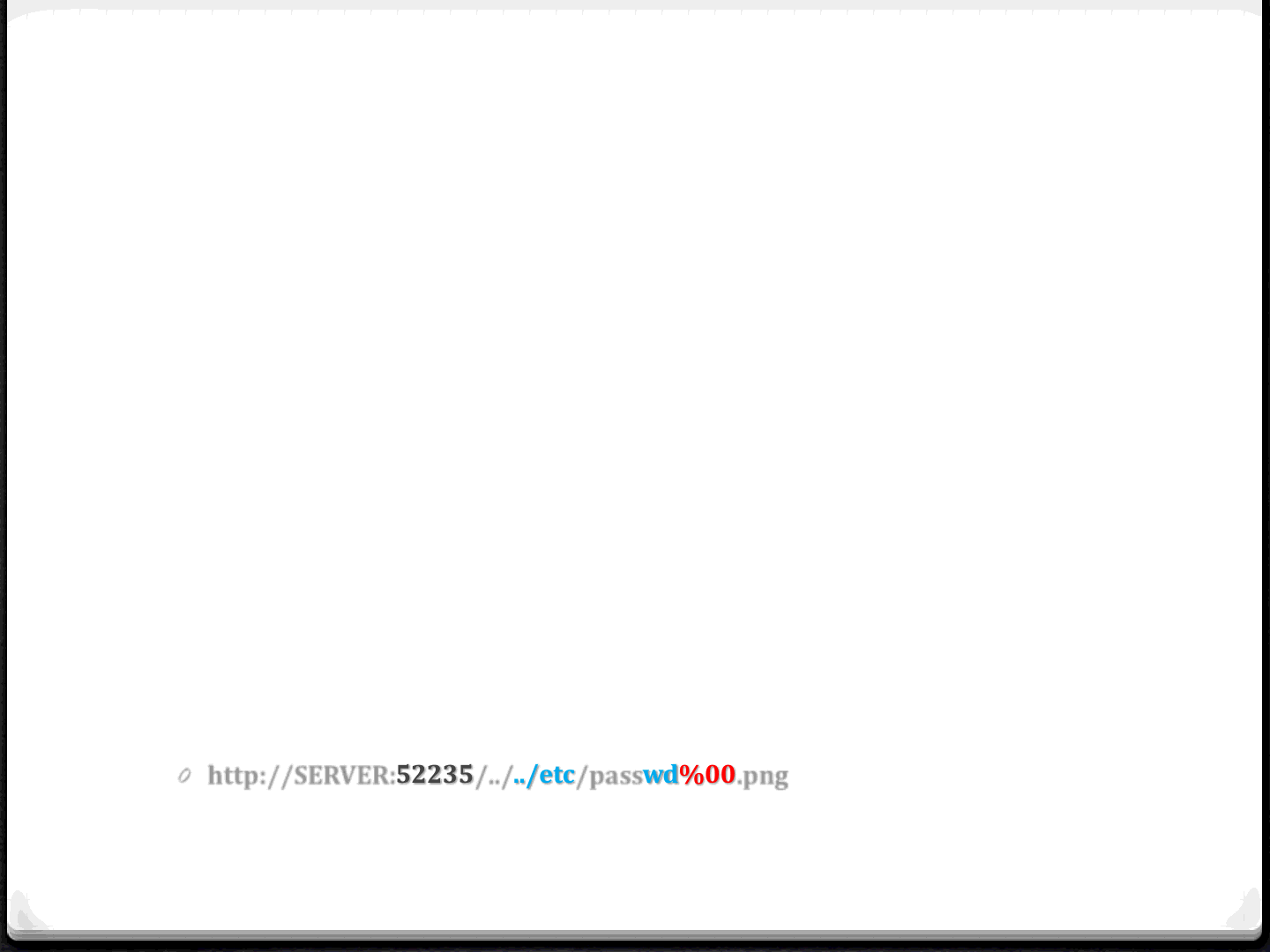
Samsung #1 (1)
0Date: 2012
0Tested device: Samsung SmartTV D6000
0Affected Service/Protocol: DMRND, an HTTP server listening on ports
52253 and 52396
0Vulnerability: Directory Traversal, which allows to download any file
available on the device except special files like those in /proc
0Details: The server has a security check to allow people to download files
having only whitelisted file extensions (jpg, png, ..). To bypass the check the
attacker needs to append a NULL byte followed by the whitelisted extension:
0http://SERVER:52235/../../etc/passwd%00.png
45
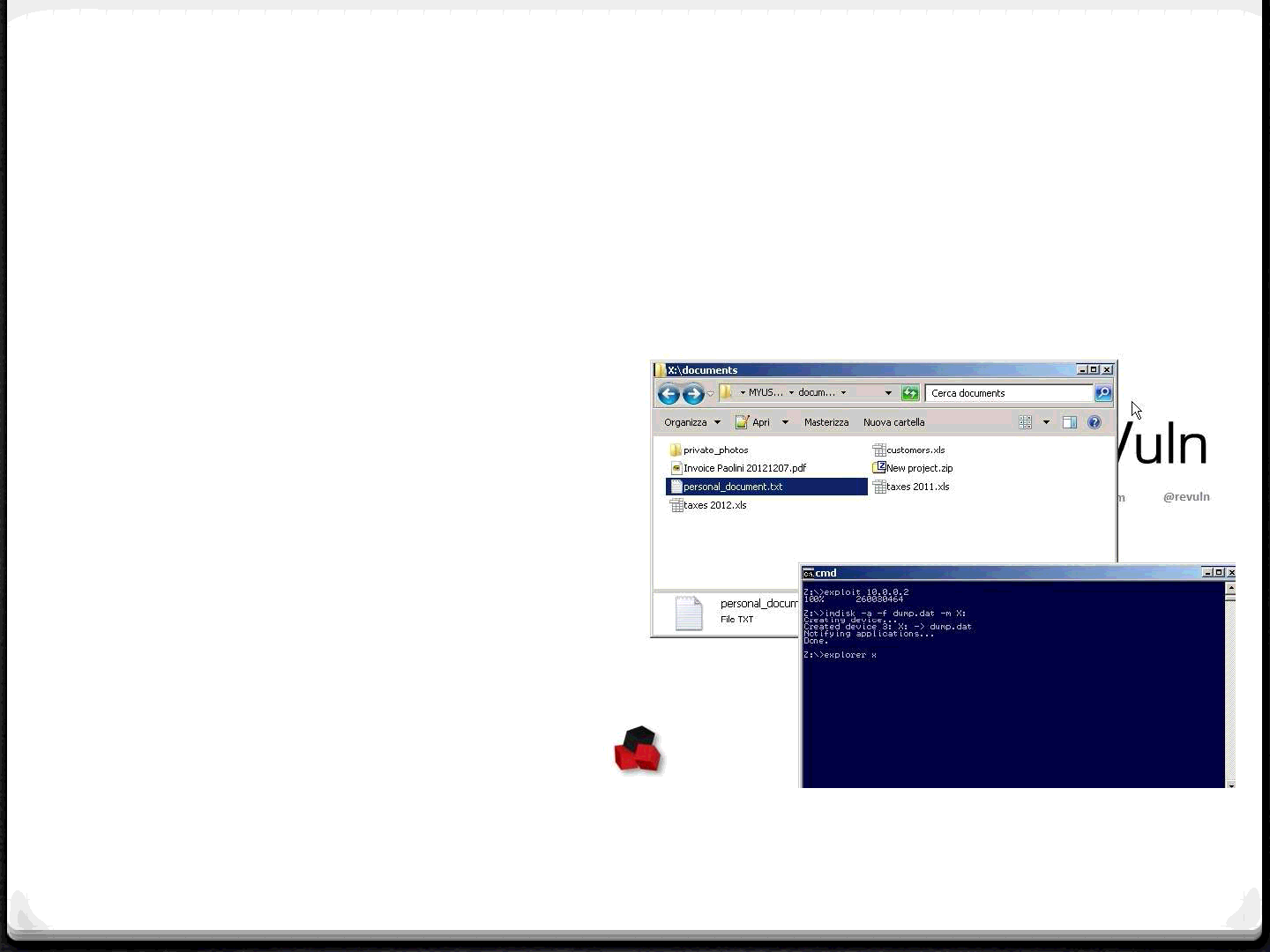
Samsung #1 (2)
46
0Download all the
filesystems from the
remote TV
0Download the
filesystems related to all
the connected USB
devices
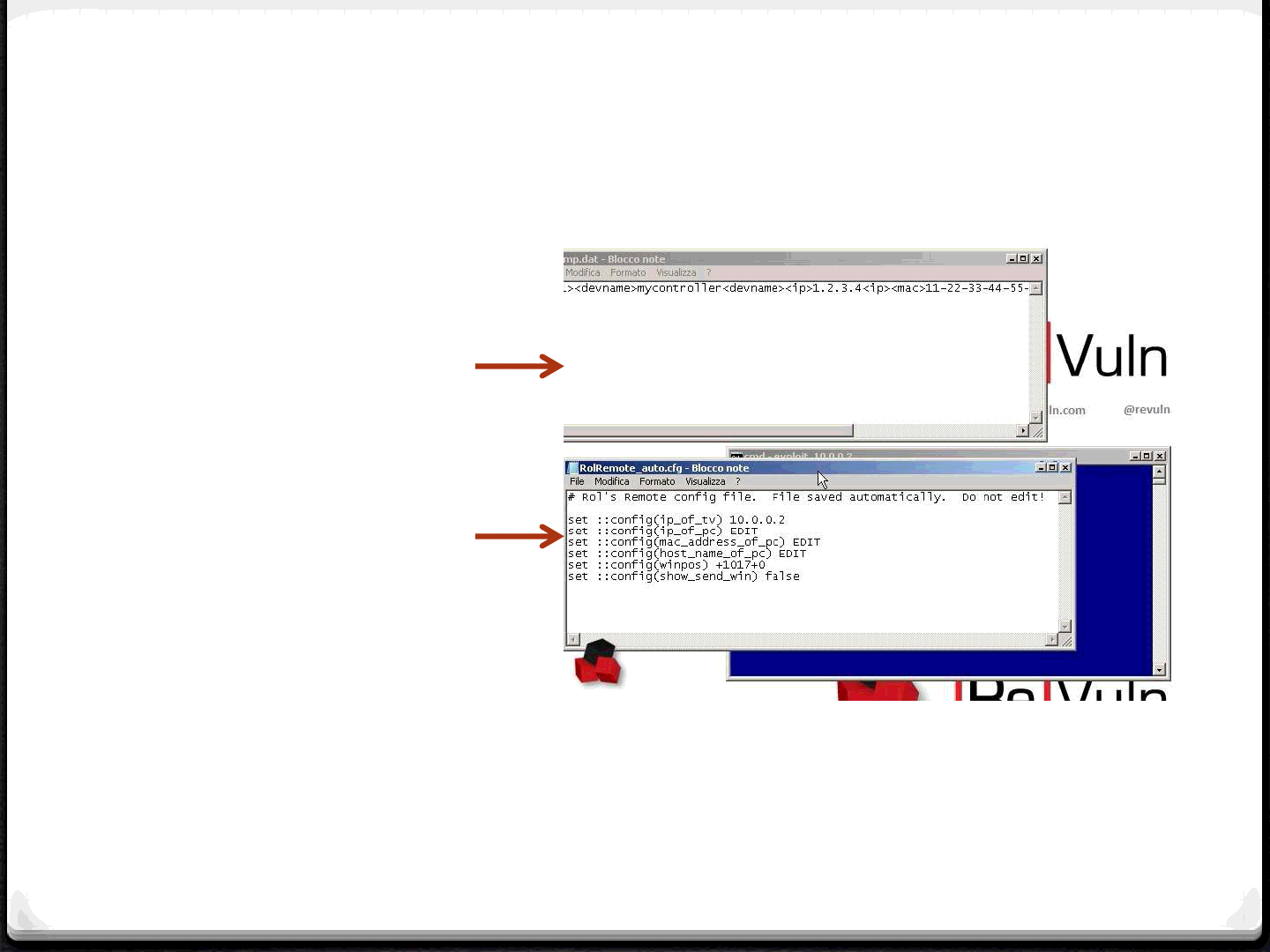
TV controller configuration file, it
contains the parameters used by the
whitelisted remote controller
Configuration file used by
the our PC program, we
need only to copy the above
parameters here
Samsung #1 (3)
47
These fields are not part of the Ethernet packets, but are defined inside the protocol itself so it’s
possible to spoof the IP, MAC address and hostname to allow an attacker in the network to
impersonate the whitelisted TV controller
Samsung #1 (4)
48
0Now we can control the TV
when the victim is not
watching
0The attacker can install
arbitrary malicious Apps on
the TV using the “develop”
account
Samsung #2 (1)
0Date: 2012
0Tested device: Samsung SmartTV D6000
0Affected Service/Protocol: DLNA client
0Vulnerability: Buffer overflow exploitable as soon as the device tries to
download the icon image associated to a DLNA host
49
1- NOTIFY UDP Packet –new DLNA host is available
2- Connect to host
3- XML data containing the icon image
Samsung #2 (2)
50
1 - NOTIFY UDP Packet –new DLNA host is available
NOTIFY * HTTP/1.1
Host: 239.255.255.250:1900
Location: http://192.168.0.3:56923/test.xml
NTS: ssdp:alive
Cache-Control: max-age=1800
Server: UPnP/1.0 DLNADOC/1.50 Platinum/0.6.8.0-bb
USN: uuid:00000000-0000-0000-0000-
000000000000::urn:schemas-upnp-org:device:MediaServer:1
NT: urn:schemas-upnp-org:device:MediaServer:1
Samsung #2 (3)
51
<iconList>
<icon>
<mimetype>image/png</mimetype>
<width>48</width>
<height>48</height>
<depth>32</depth>
<url>/images/aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa
aaaaaaaaaaaaaaaaaaaaaaaaa [...]
1- NOTIFY UDP Packet –new DLNA host is available
2- Connect to host
3 - XML data containing the icon image

Samsung #3
0Date: 2012
0Tested device: Samsung SmartTV D6000
0Vulnerability: Persistent Endless Loop
0Details: The controller packet contains a string, which is used to identify the
controller itself. A malformed string will trigger an endless loop. The only way to
fix this issue is to access the device service mode before the reboot.
52
\n\n\n\t\t\t\tHACKED!\n\n\n\n\n
2–Allow/Deny controller
3–Endless Loop

Philips Miracast (1)
0Found in 2014
0ALL the Philips TV 2013 models are affected
0Silently exploitable probably from Summer 2013
0No PIN
0No authorization request
0Hardcoded fixed password… “Miracast”
0Full access to the TV services just like in LAN
0Exploiting of directory traversal in JointSpace
0Abuse of the available services
0Let’s check what we can do…
53
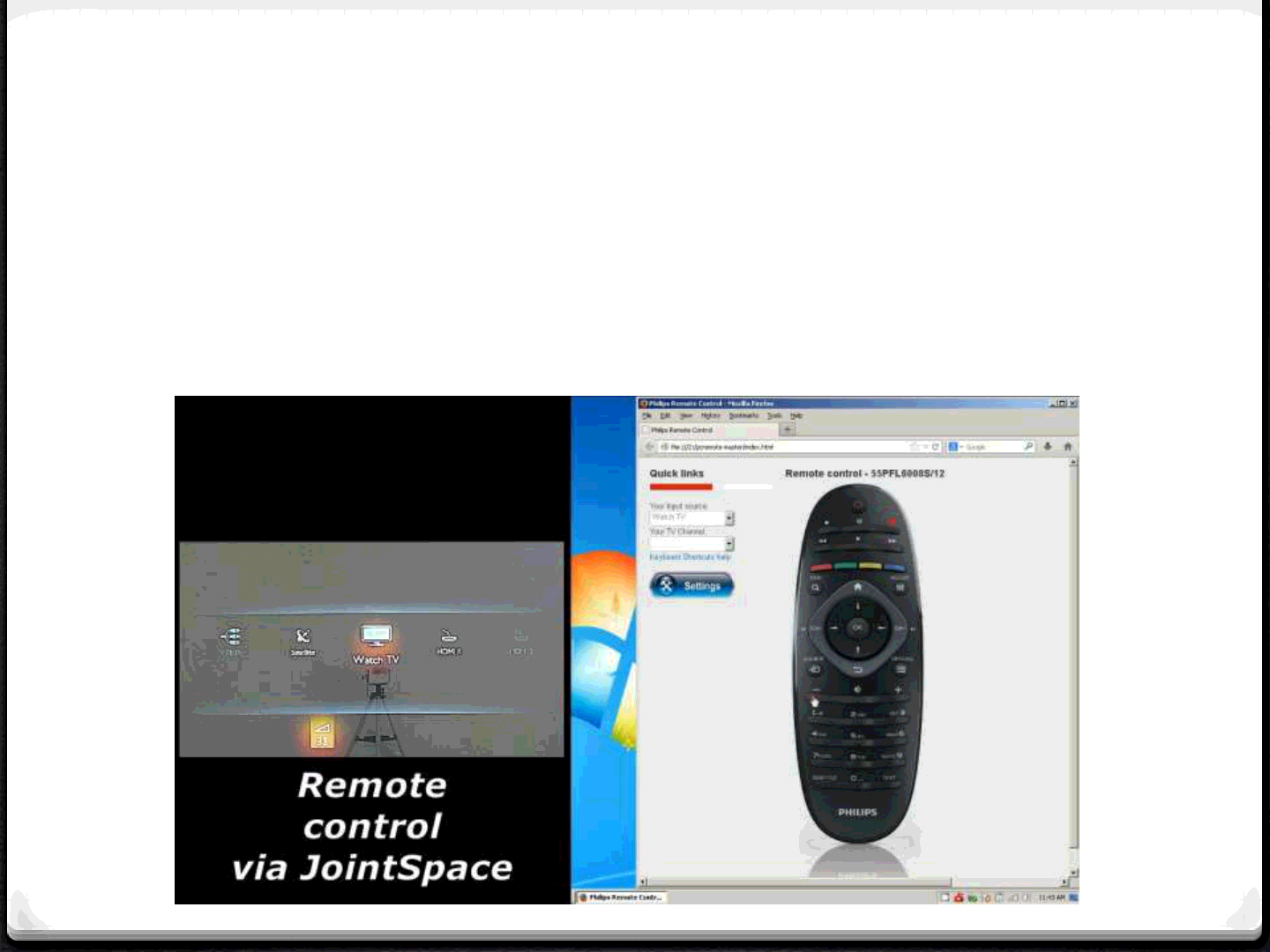
Philips Miracast (2)
0Controlling the TV from remote
54
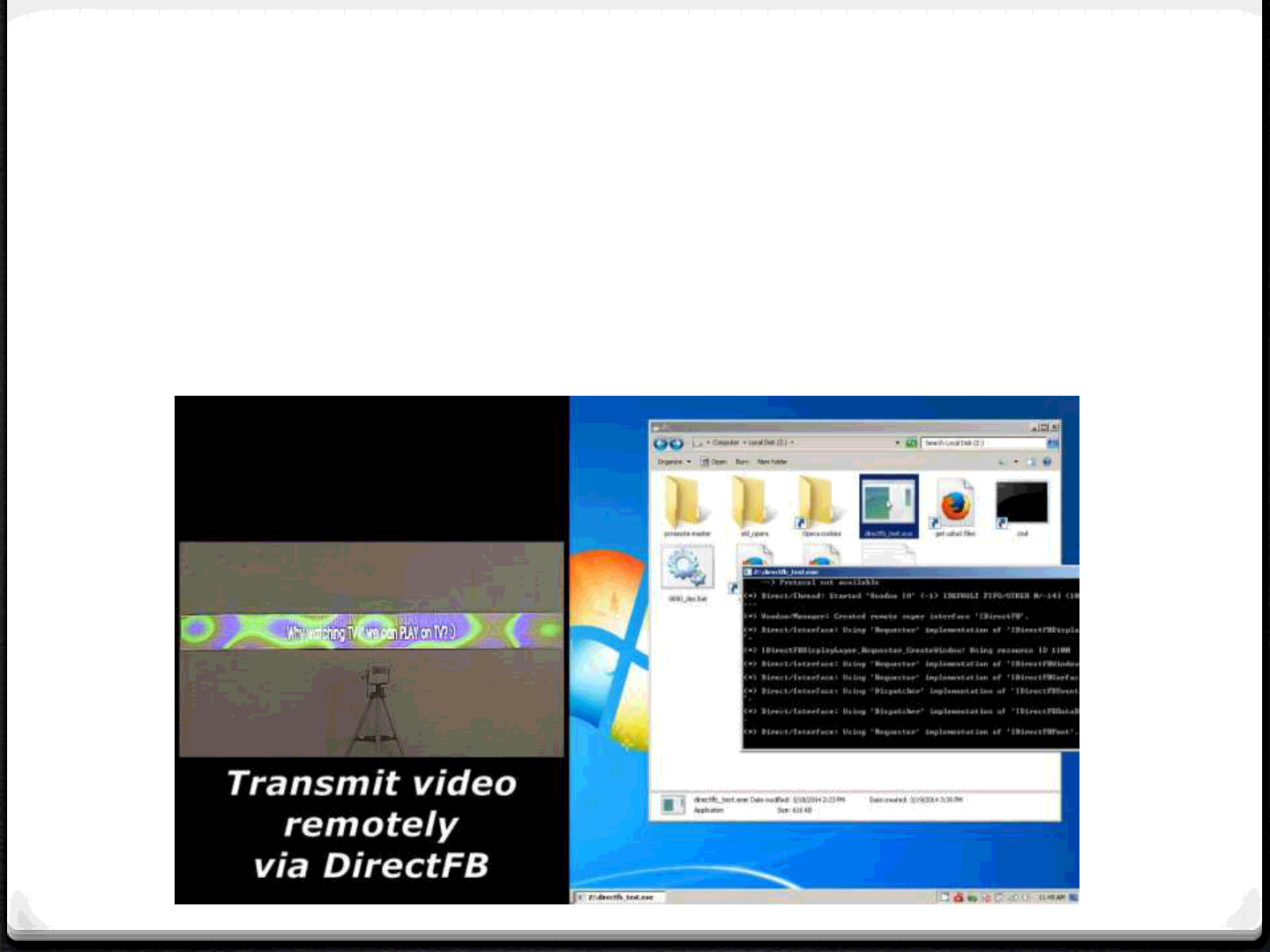
Philips Miracast (3)
0Sending audio and video to the TV… the TV is talking
to you!
55
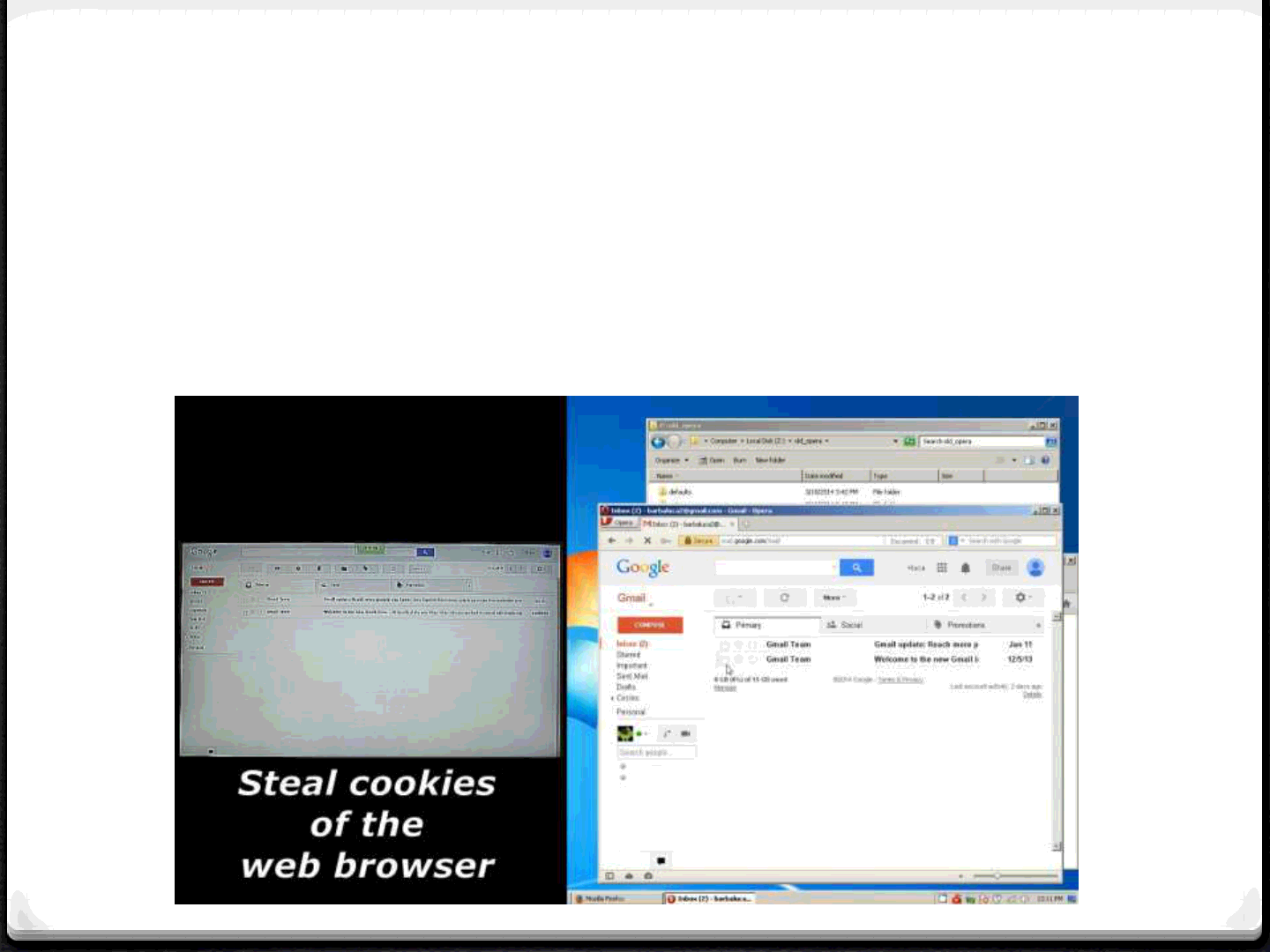
Philips Miracast (4)
0Stealing configuration files and cookies via a directory
traversal public from September 2013 but unfixed
56
What’s next?
0Android will be adopted on the upcoming SmartTV
models:
0One platform makes exploit development easier
0Same vulnerable App will be used across different Vendors..
0Less customized software means less vulnerabilities
57

Conclusion
0SmartTV are insecure
0SmartTV are a perfect target for “monitoring” a specific
target: a person or even a company (TVs are everywhere)
0Exploiting them usually requires to be in the LAN or some
user interaction
0Currently it’s difficult to have a vulnerability for owning
many models of TV, so you must focuse on the one of your
target
58
Thanks!
revuln.com
info@revuln.com
twitter.com/revuln
59
