
OWNING RENDER FARMS
VIA NVIDIA MENTAL RAY
Luigi Auriemma1and Donato Ferrante2
ReVuln
http://revuln.com
info@revuln.com
http://twitter.com/revuln
10 December 2013
Abstract This paper details a vulnerability affecting NVIDIA mental ray,
which allows an attacker to take control over a mental ray based render
farm.
1 INTRODUCTION
NVIDIA mental ray3"is a feature rich, high performance 3D rendering software that
creates images of outstanding quality and unsurpassed realism based on advanced
ray tracing techniques. It enables artists to create any imaginable visual effect
by combining advanced global illumination with full programmability. Used by
industry professionals for over 25 years, mental ray has become a standard for
photorealistic rendering across the film, visual effects, and design industries."
Figure 1: NVIDIA mental ray applications
NVIDIA mental ray is used in several contexts, including but not limited to:
•Visual Effects
•Feature Animation
•Game Creation
•Architectural Design
•Product Prototyping and Design
•CAD visualization
1http://twitter.com/luigi_auriemma
2http://twitter.com/dntbug
3http://www.nvidia-arc.com/mentalray.html
ReVuln - http://revuln.com page 1 of 8
NVIDIA mental ray has been used in the moviemaker industry for several titles,
including:
•Hulk
•The Matrix Reloaded
•The Matrix Revolutions
•Star Wars Episode II: Attack of the Clones
•The Day After Tomorrow
•Poseidon
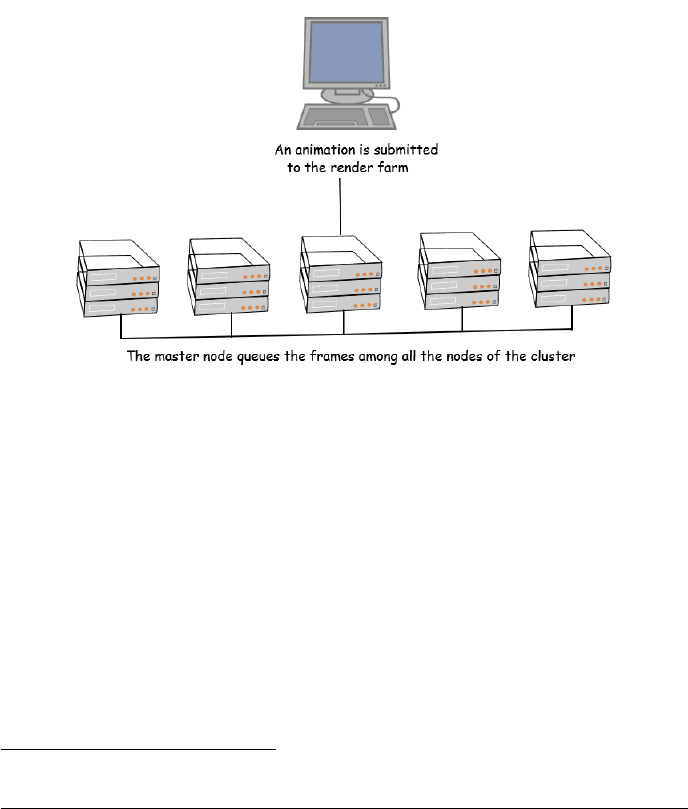
2 WHAT IS A RENDER FARM?
A render farm is a group of networked computers (slaves) devoted to rendering
images, used typically in the production of computer-animated films.
Figure 2: An example of render farm
To get a better idea on how powerful render farms are, a nice description can
be found on Tom’s Hardware4: "render farms [..]are banks of machines with
the express purpose of rendering finished frames. In addition to the systems that
animators use, render farms simultaneously use many dedicated processors for
rendering. For instance, Industrial Light and Magic had a render farm with 5,700
processor cores (and 2,000 cores in their artists’ machines) when Transformers 2
was produced. Even a small facility with only a dozen animators is likely to have
more than a hundred processor cores at their disposal".
4http://www.tomshardware.com/reviews/render-farm-node,2340.html
ReVuln - http://revuln.com page 2 of 8
3 NVIDIA MENTAL RAY
From the official page5: "NVIDIA mental ray is embedded into several content cre-
ation applications widely used in the media entertainment and design industries.
It is also available as a standalone product for rendering on a render farm, and
as a library for integration into custom applications". NVIDIA mental ray supports
several platforms including: Windows, Linux and MacOS. Some of the applications
using mental ray, include:
•AutoDesk 3ds Max
•AutoDesk Maya
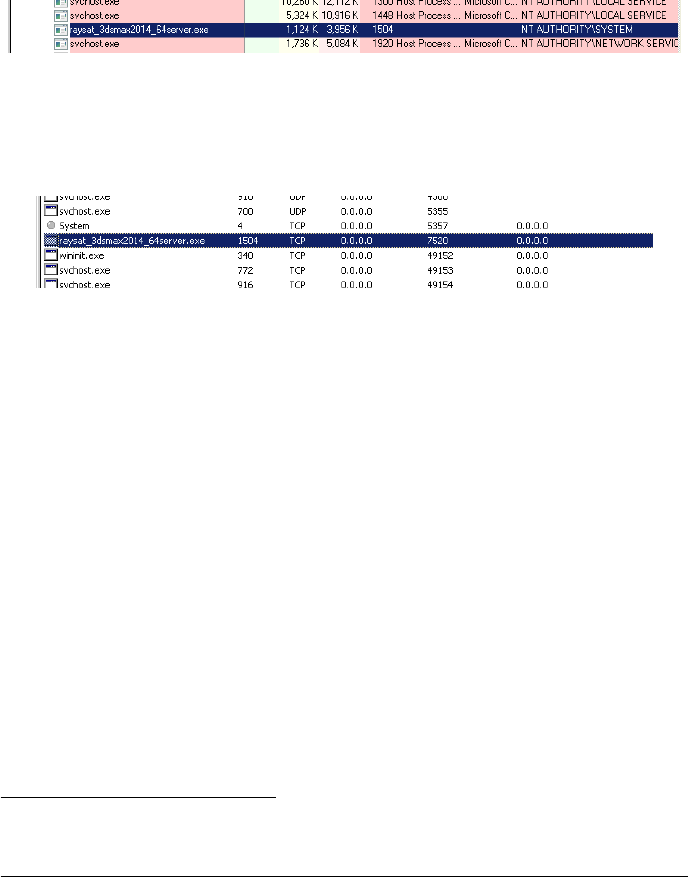
The NVIDIA mental ray component is a system service, which runs on Windows
based systems with SYSTEM privileges6:
Figure 3: NVIDIA mental ray service privileges
The service waits for incoming connections on the TCP port: 7520 (this port
might be different for older versions of the software):
Figure 4: NVIDIA mental ray service port
5http://www.nvidia-arc.com/mentalray.html
6http://en.wikipedia.org/wiki/Privilege_(computing)
ReVuln - http://revuln.com page 3 of 8
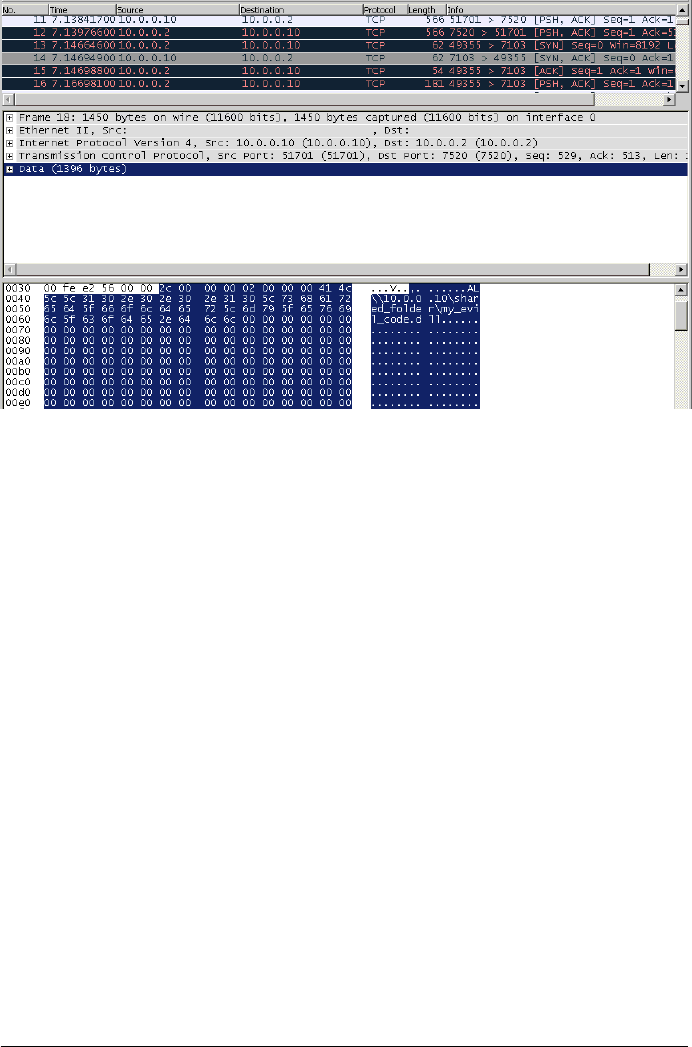
4 VULNERABILITY
There is a vulnerability affecting NVIDIA mental ray (raysat) version 3.11.1.10,
which allows a malicious user to load arbitrary DLLs on a victim system, thus an
attacker can take control over a whole render farm by simply injecting a malicious
remote library. To trigger the remote vulnerability an attacker needs to send a
malicious packet to the affected host (slave).
Figure 5: The malicious packet
As a side note, we noticed that the service spawns a new process for each
new connection, which means that an attacker has potentially infinite chances to
achieve a successful exploitation.
ReVuln - http://revuln.com page 4 of 8
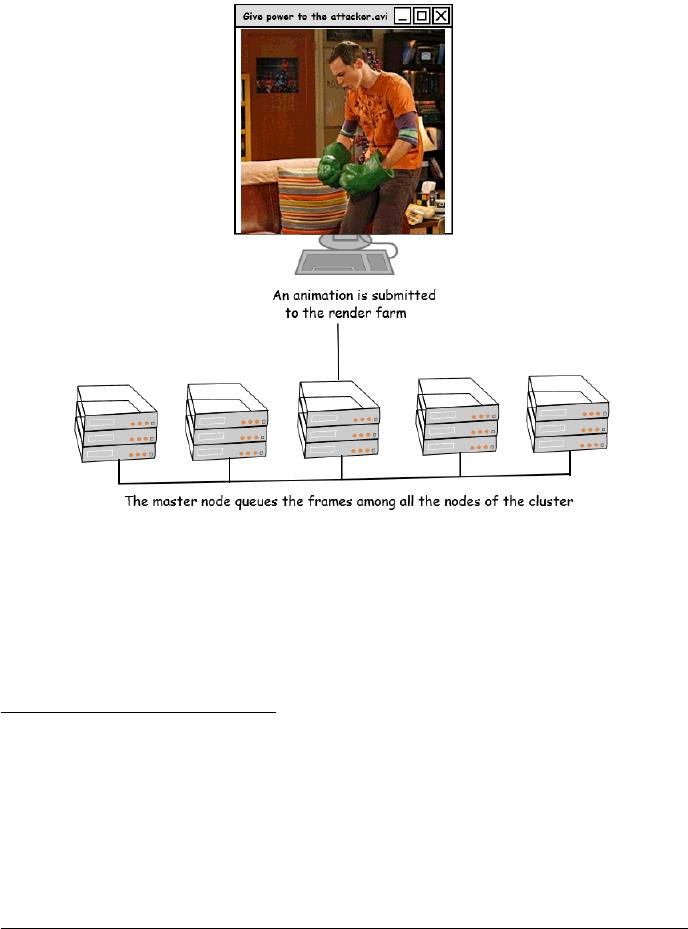
5 POST-EXPLOITATION
An interesting aspect of this technology is that it’s used on render farms7. A render
farm is composed of a computer cluster using very powerful hardware, which usu-
ally includes powerful GPUs8such as the ones based on the TESLA family9.
One of the possible scenarios to exploit this computational power is to reuse
such farms to perform password cracking. If you are not familiar with password
cracking, this strategy10 "is the process of recovering passwords from data that have
been stored in or transmitted by a computer system. A common approach (brute-
force attack) is to repeatedly try guesses for the password".
Figure 6: Owning a render farm
Since password cracking can be optimized on GPUs 11 12 13, what about using
a render farm to play with Rainbow tables14 or mining some Bitcoin15 ?
7http://en.wikipedia.org/wiki/Render_farm
8http://en.wikipedia.org/wiki/Graphics_processing_unit
9http://www.nvidia.com/object/tesla-supercomputing-solutions.html
10http://en.wikipedia.org/wiki/Password_cracking
11http://security.stackexchange.com/questions/32816/why-are-gpus-so-good-at-cracking-passwords
12http://blog.erratasec.com/2011/06/password-cracking-mining-and-gpus.html
13http://www.tomshardware.com/reviews/password-recovery-gpu,2945.html
14http://en.wikipedia.org/wiki/Rainbow_table
15http://www.tomshardware.com/reviews/bitcoin-mining-make-money,3514.html
ReVuln - http://revuln.com page 5 of 8
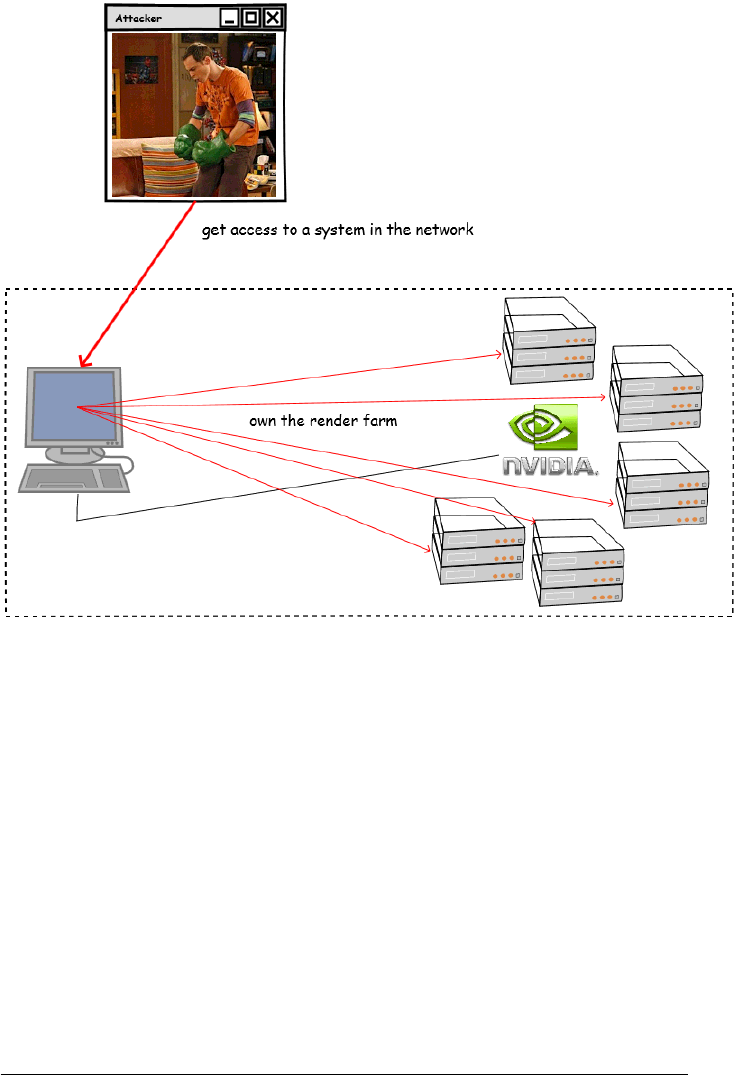
6 A POSSIBLE ATTACK SCENARIO
The following image shows one of the possible attack scenarios, in which an at-
tacker initially gets access to one of the systems available into the victim network,
and then the attacker exploits the vulnerability affecting NVIDIA mental ray to get
control over the render farm.
Figure 7: Possible attack scenario
ReVuln - http://revuln.com page 6 of 8

7 FAQ
Q1. Did you report the issue to the Vendor?
- No.
Q2. Are the previous versions of the software affected by the same issue?
- Yes.
Q3. Are the 32-bit and 64-bit version of the software both affected by the same
issue?
- Yes.
Q4. Is there any other scenario in which an attacker can use the issue?
- Yes, for example in a privilege escalation scenario.
Q5. Is this the only issue affecting this software?
- No, there are other issues, including a stack-based buffer overflow trig-
gered via sscanf16, in detail: sscanf(input, "%05d %05d %05d %05d
%05d %05d %05d %s", ...). This issue is unlikely to be exploitable as
there is not only DEP and ASLR, but also a limitation on the packet size.
16http://www.cplusplus.com/reference/cstdio/sscanf/
ReVuln - http://revuln.com page 7 of 8

