
{
Securing ICS Applications When
Vendors Refuse Or Are Slow To
Produce a Security Patch
ReVuln Ltd. – revuln.com
SCADA Security Scientific Symposium – S4 2014
Miami 15 Jan 2014

Luigi Auriemma
twitter.com/luigi_auriemma
Donato Ferrante
twitter.com/dntbug
Who?

Vulnerability Feeds
0-day
1-day
SCADA defense
SCADA-shield
Penetration Testing
Consulting
About ReVuln
revuln.com
info@revuln.com
twitter.com/revuln

Security Vulnerabilities
Uncovering new vulnerabilities
Final considerations
Agenda

Security Vulnerabilities
Problems
Possible solutions
Some numbers
Uncovering new vulnerabilities
Final considerations
Agenda

Security Vulnerabilities

Downtime
Information stealing
Bridge-attack/SmartGrid
Remote control/pwn
Problems

Possible Solutions

Vendor Patches
Take time
Reactive
May NOT fix the security issue
NO information = NO patch
Possible Solutions - I

Unofficial Patches
Require knowledge of the security issues
Sometimes it’s not easy/quick to fix an issue
It may affect checksums
NO information = NO patch
Possible Solutions - II

Signatures-based defenses (IPS/IDS)
Require knowledge of the security issues
NO information = NO signatures
Work ONLY on few exploit “patterns”
Exploit mutation usually breaks these detections
Possible Solutions - III

SCADA shield
Pro-Active solution
Combine information from internal
vulnerability feeds, and exploit prevention
techniques to provide a shield to most of the
pre-existent HMI/SCADA solutions
Possible Solutions - IV

Tries to prevent classes of vulnerabilities, i.e.:
Directory traversal
File Inclusion/Overwriting
Stack and Heap Overflow
Use-After-Free
Commands Injection
DEMO’ed during S4 2013
SCADA Shield - I

Allows to perform Hot-Patching
In-memory patch
No need to restart/interrupt the system
Vendor’s products warranty NOT voided
SCADA Shield - II

We wanted more..
In the current release we are testing a custom
detection engine
Our idea is to be able to integrate our feeds with
SCADA shield signatures
Our SCADA customers will be able to import
SCADA shield signatures on-the-fly to protect
their systems
SCADA Shield - III
Some Numbers

Raw data..
Advisory Name: Released: Fixed*:
realwin_1 15 oct 2010 -> 08 nov 2010
inbatch_1 07 dec 2010 -> 02 mar 2011
integraxor_1 21 dec 2010 -> 12 jan 2011
winlog_1 12 jan 2011 -> 13 jan 2011
realwin_2/8 21 mar 2011 -> 20 apr 2011
igss_1/8 21 mar 2011 -> 06 may 2011*
genesis_1/13 21 mar 2011 -> 18 apr 2011
factorylink_1/6 21 mar 2011 -> 05 apr 2011
bwocxrun_1 02 sep 2011 -> 17 feb 2012
twincat_1 13 sep 2011 -> 06 oct 2011
scadapro_1 13 sep 2011 -> 20 sep 2011
rslogix_1 13 sep 2011 -> 06 oct 2011
movicon_* 13 sep 2011 -> 21 oct 2011
daqfactory_1 13 sep 2011 -> 21 sep 2011
pcvue_1 27 sep 2011 -> 06 dec 2011
opcnet_1 10 oct 2011 -> 25 jan 2012
webmi2ads_1 10 oct 2011 -> 17 jan 2012
11 apr 2012
promotic_1 13 oct 2011 -> 23 jan 2012
promotic_2 30 oct 2011 -> 11 apr 2012
ifix_1 06 feb 2011 -> 07 nov 2011
optimalog_1 13 nov 2011 -> 27 sep 2012
winccflex_1 28 nov 2011 -> 18 apr 2012
indusoft_* 27 apr 2011 -> 16 nov 2011
almsrvx_1 28 nov 2011 -> 26 dec 2011*
codesys_1 29 nov 2011 -> 06 jan 2012
14 nov 2012
kingview_1 09 nov 2011 -> 22 dec 2011
rnadiagreceiver_1 17 jan 2012 -> 06 apr 2012
abb_1 10 oct 2011 -> 22 feb 2012
xarrow_1 02 mar 2012 -> 24 may 2012
rtip_1 17 oct 2011 -> 22 aug 2012
ifix_2 17 oct 2011 -> 03 aug 2012
suitelink_1 11 may 2012 -> 19 jun 2012
proservrex_1 13 may 2012 -> 27 jun 2012
winlog_2 26 jun 2012 -> 31 jul 2012
specview_1 29 jun 2012 -> 12 jan 2012
We consider only
remote vulnerabilities..
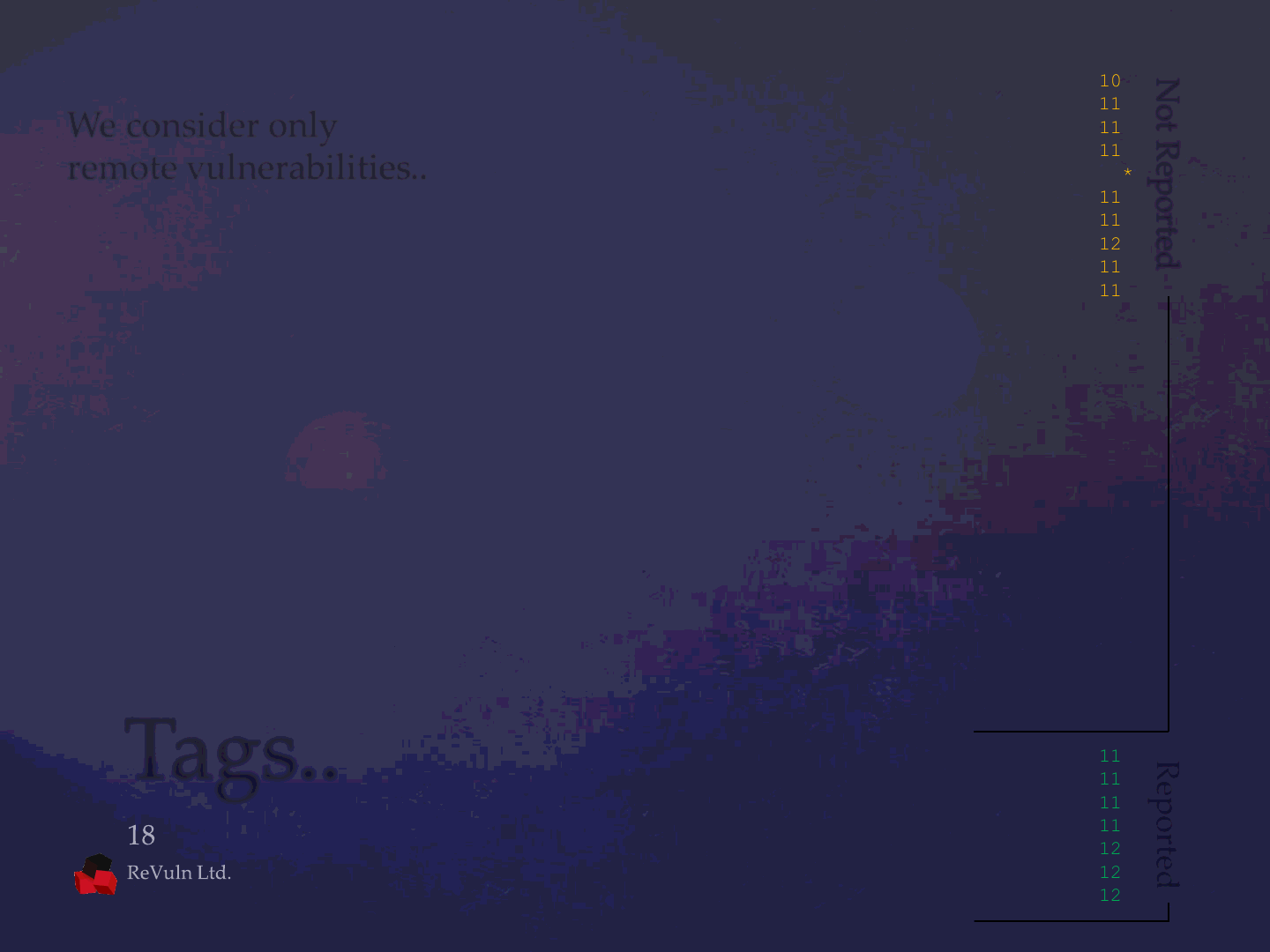
Tags..
Advisory Name: Released: Fixed*:
realwin_1 15 oct 2010 -> 08 nov 2010
inbatch_1 07 dec 2010 -> 02 mar 2011
integraxor_1 21 dec 2010 -> 12 jan 2011
realwin_2/8 21 mar 2011 -> 20 apr 2011
igss_1/8 21 mar 2011 -> 06 may 2011*
genesis_1/13 21 mar 2011 -> 18 apr 2011
factorylink_1/6 21 mar 2011 -> 05 apr 2011
bwocxrun_1 02 sep 2011 -> 17 feb 2012
twincat_1 13 sep 2011 -> 06 oct 2011
scadapro_1 13 sep 2011 -> 20 sep 2011
rslogix_1 13 sep 2011 -> 06 oct 2011
movicon_* 13 sep 2011 -> 21 oct 2011
daqfactory_1 13 sep 2011 -> 21 sep 2011
pcvue_1 27 sep 2011 -> 06 dec 2011
opcnet_1 10 oct 2011 -> 25 jan 2012
webmi2ads_1 10 oct 2011 -> 17 jan 2012
11 apr 2012
promotic_1 13 oct 2011 -> 23 jan 2012
promotic_2 30 oct 2011 -> 11 apr 2012
almsrvx_1 28 nov 2011 -> 26 dec 2011*
codesys_1 29 nov 2011 -> 06 jan 2012
14 nov 2012
rnadiagreceiver_1 17 jan 2012 -> 06 apr 2012
xarrow_1 02 mar 2012 -> 24 may 2012
suitelink_1 11 may 2012 -> 19 jun 2012
proservrex_1 13 may 2012 -> 27 jun 2012
winlog_2 26 jun 2012 -> 31 jul 2012
specview_1 29 jun 2012 -> 12 jan 2012
winlog_1 12 jan 2011 -> 13 jan 2011
ifix_1 06 feb 2011 -> 07 nov 2011
indusoft_* 27 apr 2011 -> 16 nov 2011
kingview_1 09 nov 2011 -> 22 dec 2011
abb_1 10 oct 2011 -> 22 feb 2012
rtip_1 17 oct 2011 -> 22 aug 2012
ifix_2 17 oct 2011 -> 03 aug 2012
Reported
Not Reported
We consider only
remote vulnerabilities..
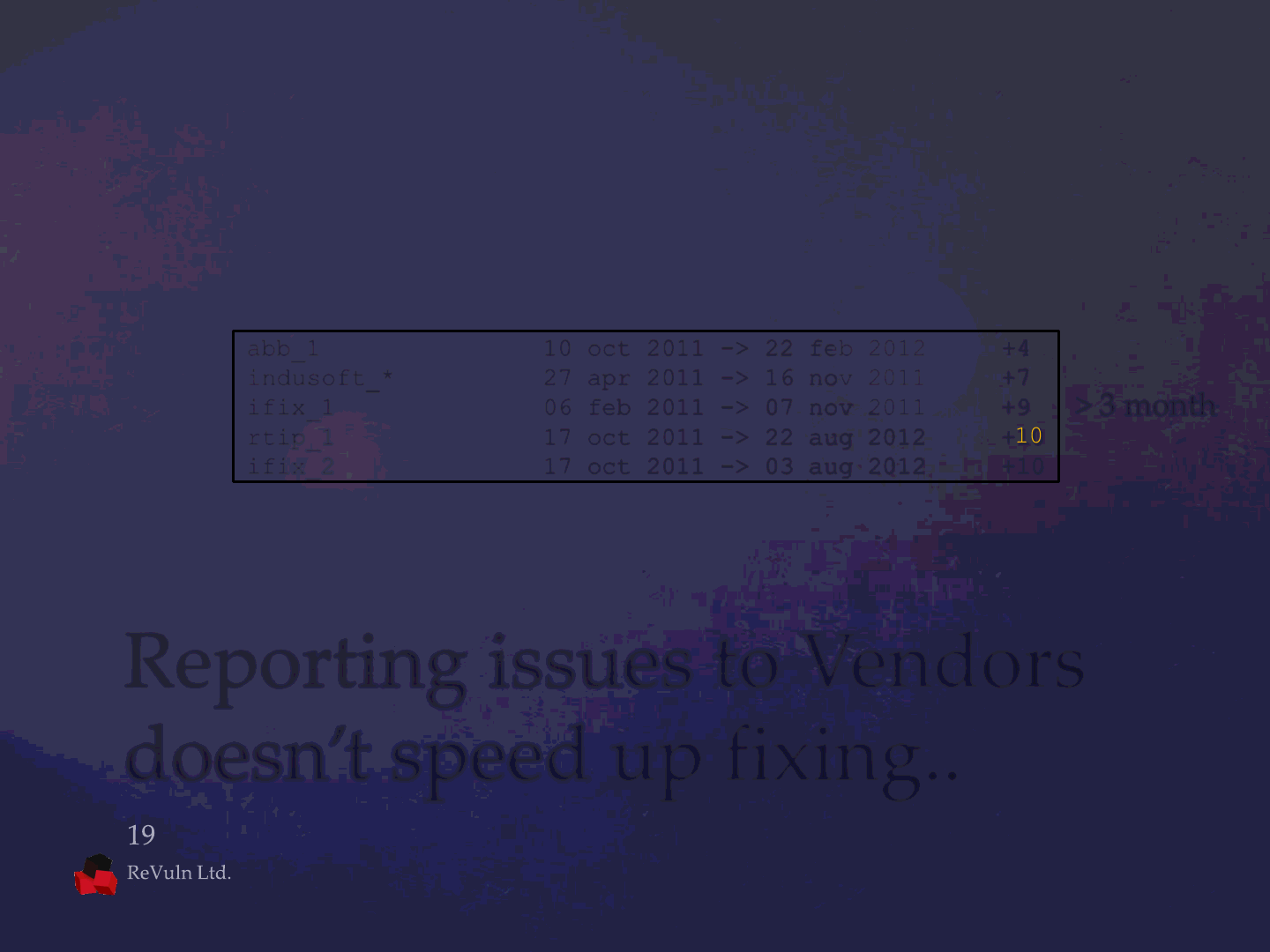
Reporting issues to Vendors
doesn’t speed up fixing..
Advisory Name: Released: Fixed*:
winlog_1 12 jan 2011 -> 13 jan 2011 +0
kingview_1 09 nov 2011 -> 22 dec 2011 +1
abb_1 10 oct 2011 -> 22 feb 2012 +4
indusoft_* 27 apr 2011 -> 16 nov 2011 +7
ifix_1 06 feb 2011 -> 07 nov 2011 +9
rtip_1 17 oct 2011 -> 22 aug 2012 +10
ifix_2 17 oct 2011 -> 03 aug 2012 +10
> 3 month
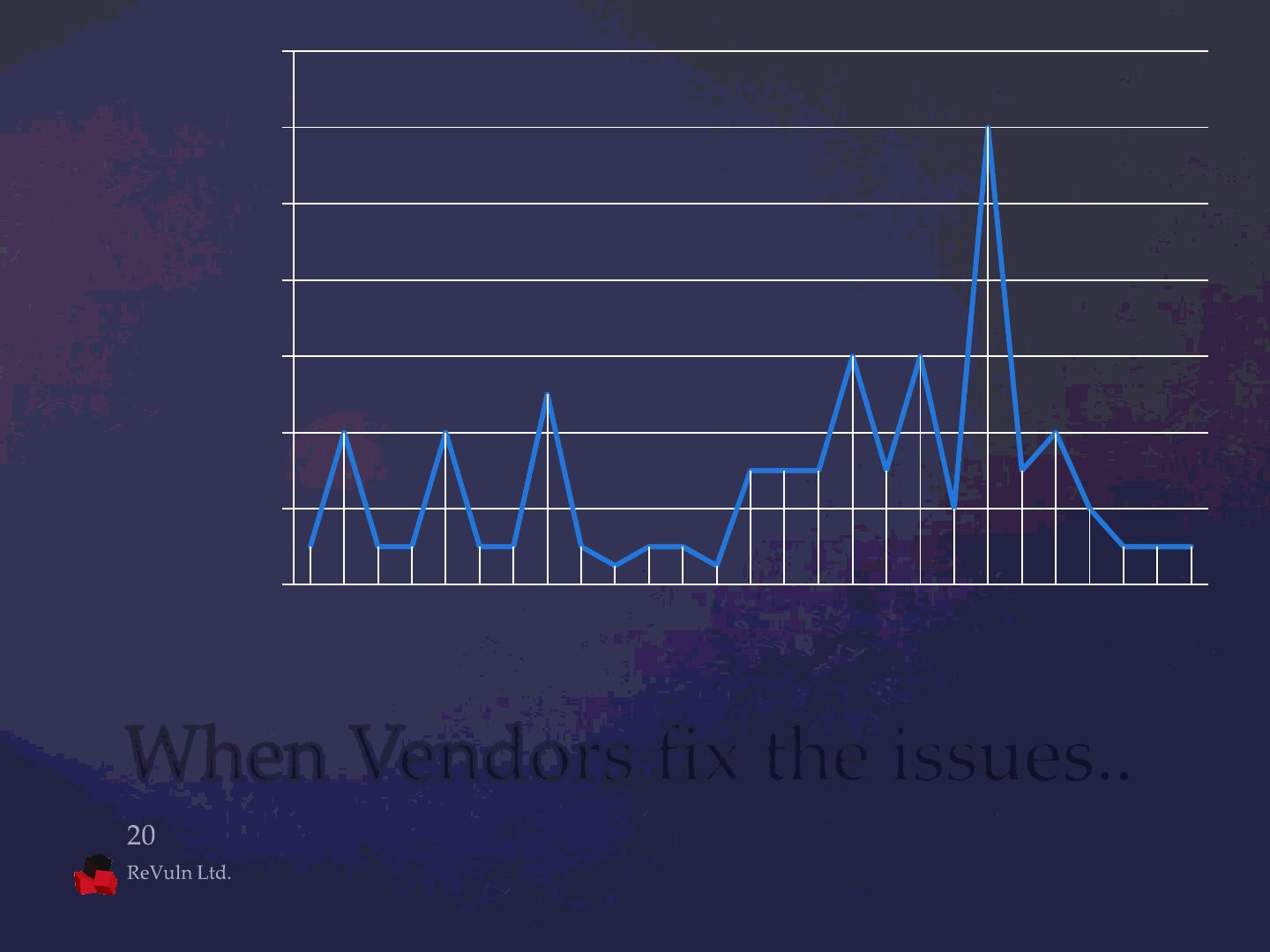
0
2
4
6
8
10
12
14
Months to Fix
Advisory Published (2010-2012)
When Vendors fix the issues..
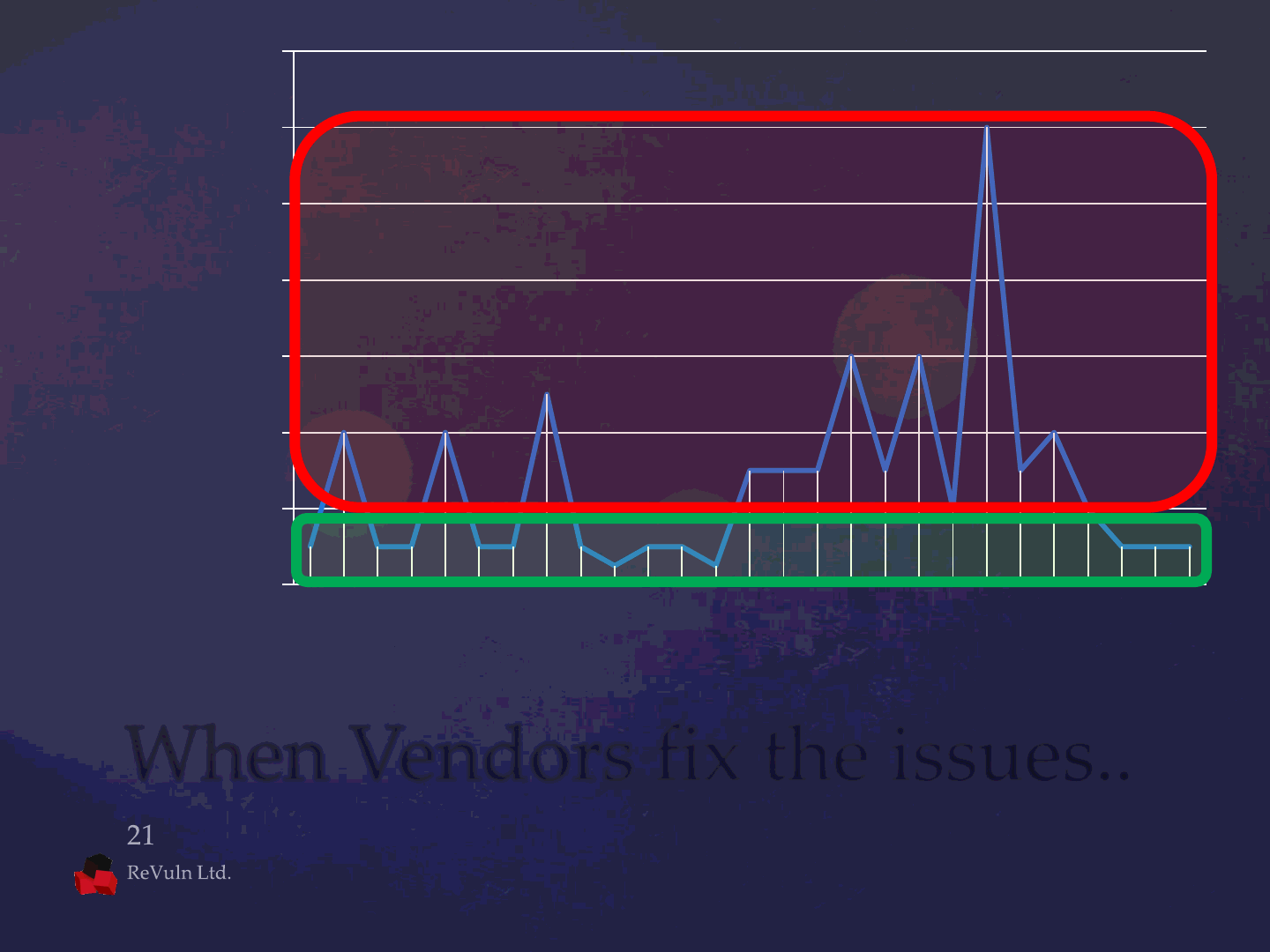
0
2
4
6
8
10
12
14
Months to Fix
Advisory Published (2010-2012)
When Vendors fix the issues..
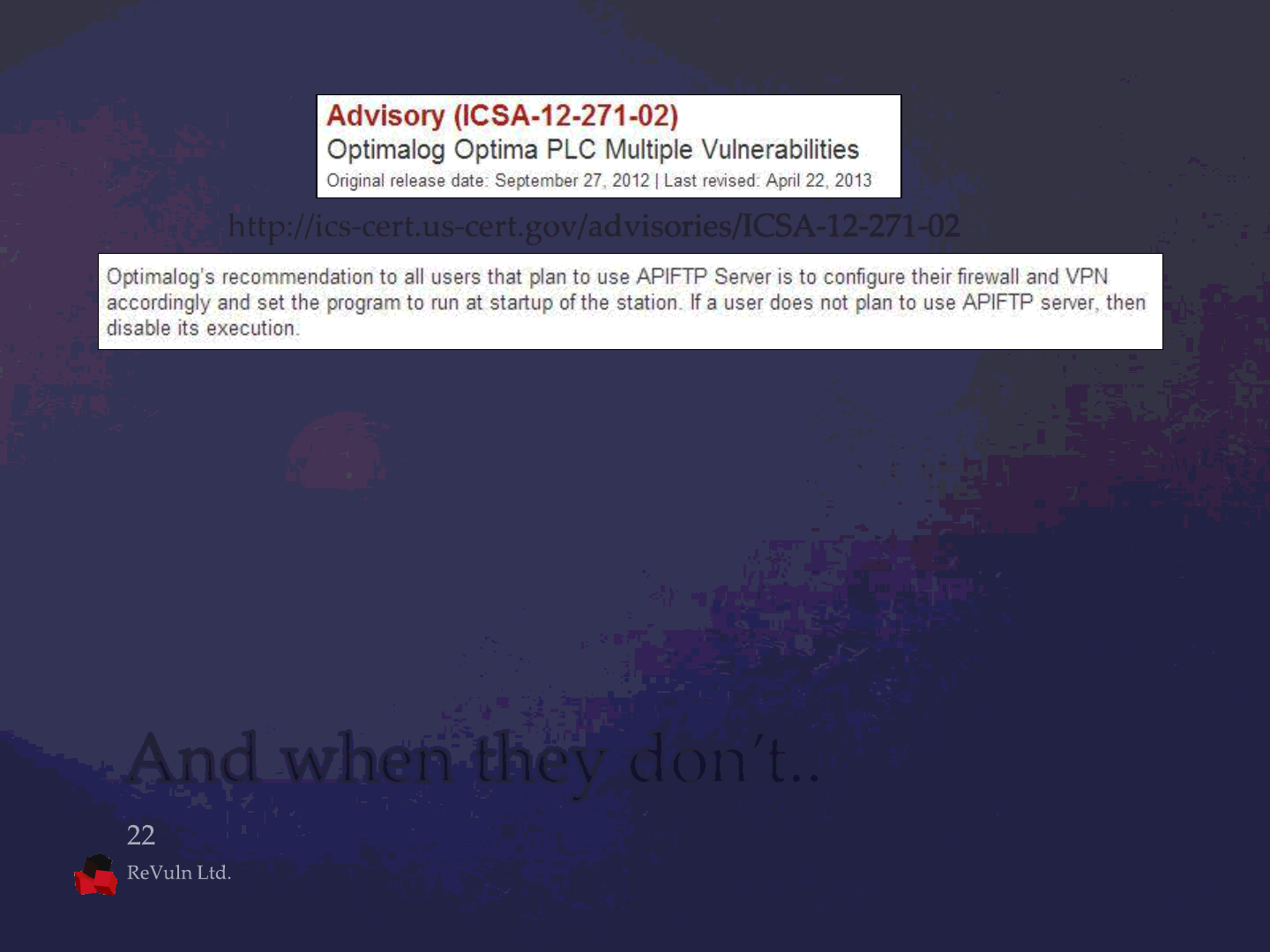
And when they don’t..
Fixed? No. But the users will get a
RECOMMENDATION instead…
http://ics-cert.us-cert.gov/advisories/ICSA-12-271-02
Advisory Name: Released: Fixed*:
optimalog_1 13 nov 2011 -> 27 sep 2012
winccflex_1 28 nov 2011 -> 18 apr 2012

Security Vulnerabilities
Problems
Possible solutions
Some numbers
Uncovering new vulnerabilities
Final considerations
Agenda

Uncovering new vulnerabilities
General Electric
Siemens
ABB
Rockwell
Invensys
Schneider
InduSoft
CoDeSys
…
Vendors

Product: IntegraXor
http://www.integraxor.com
Tested versions <= 4.1.4380
Default port: 7131 TCP
Protocol: HTTP
Status: 0-day
IntegraXor SCADA is a pure Webserver that developed based on
W3C standard compliant technologies. No additional web server
is needed so installation is very simple and yet cost effective. This
also means no additional client program nor plug-in needed
except a modern browser for viewing/accessing the mimic
screen. So this is a Browser/ Server system rather than ordinary
Client/Server system.
The Product
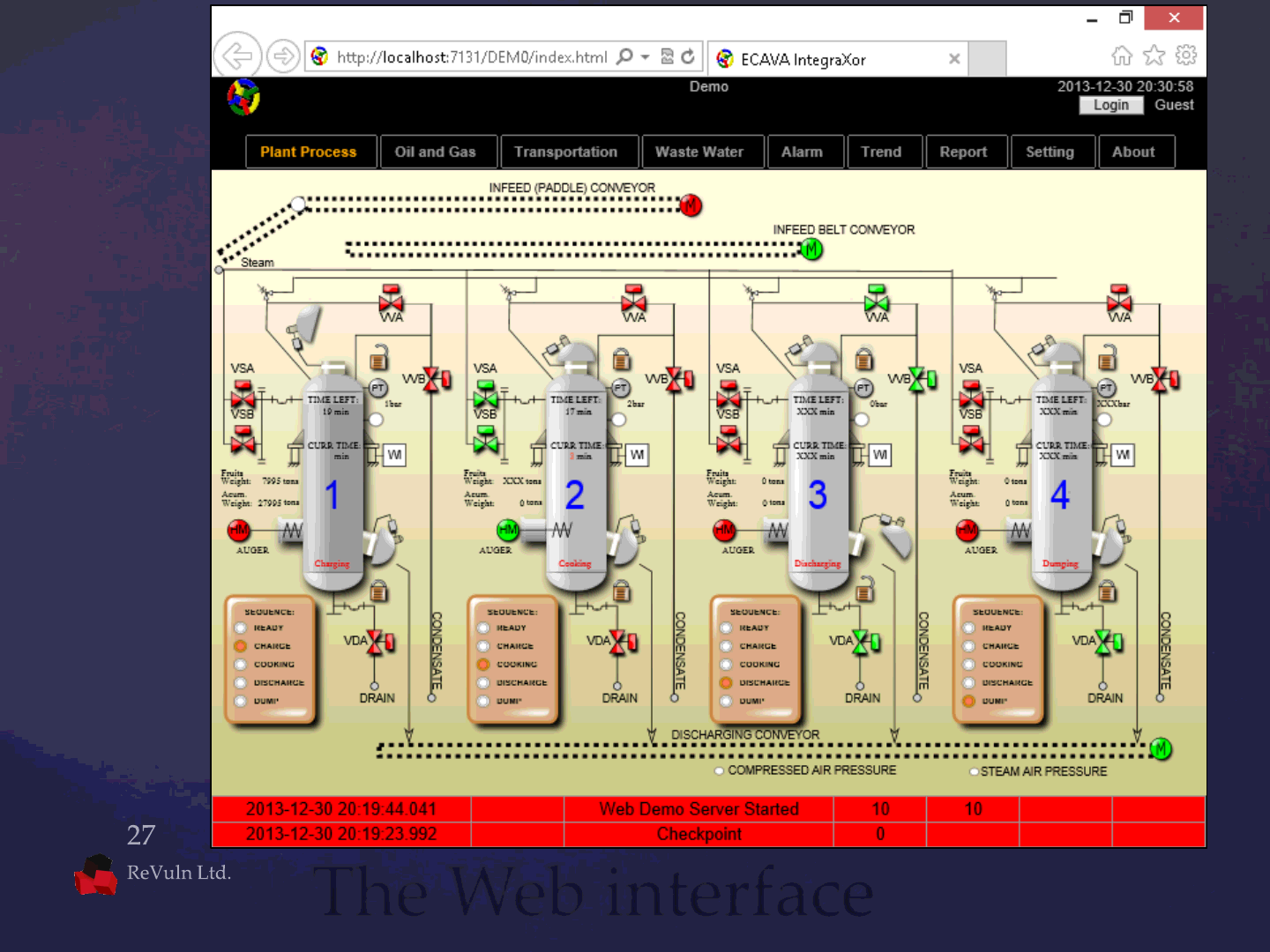
The Web interface
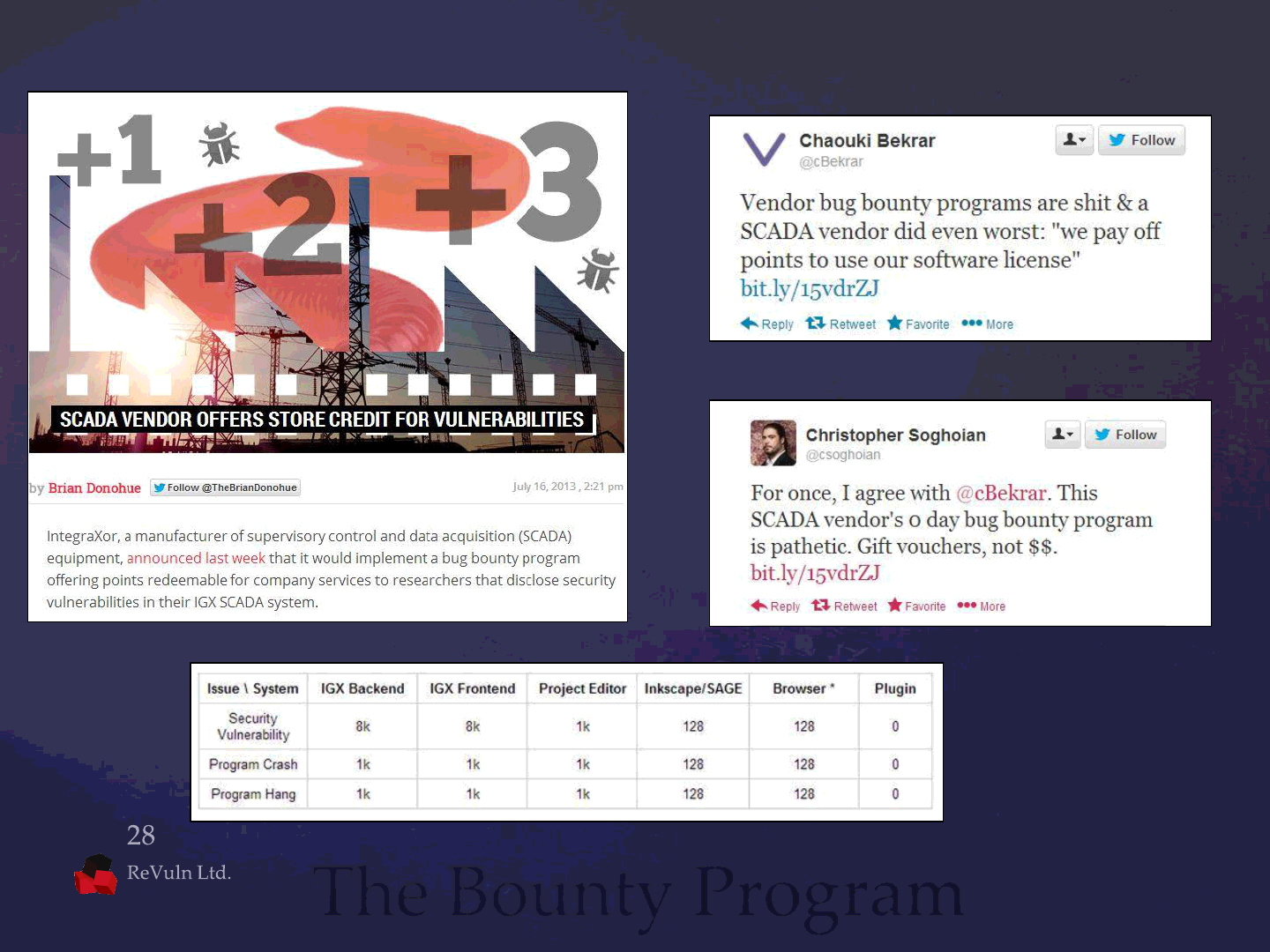
The Bounty Program
https://twitter.com/csoghoian/status/356560591801942016
http://threatpost.com/scada-vendor-offers-store-credit-for-vulnerabilities
https://twitter.com/cBekrar/status/356550864212725760
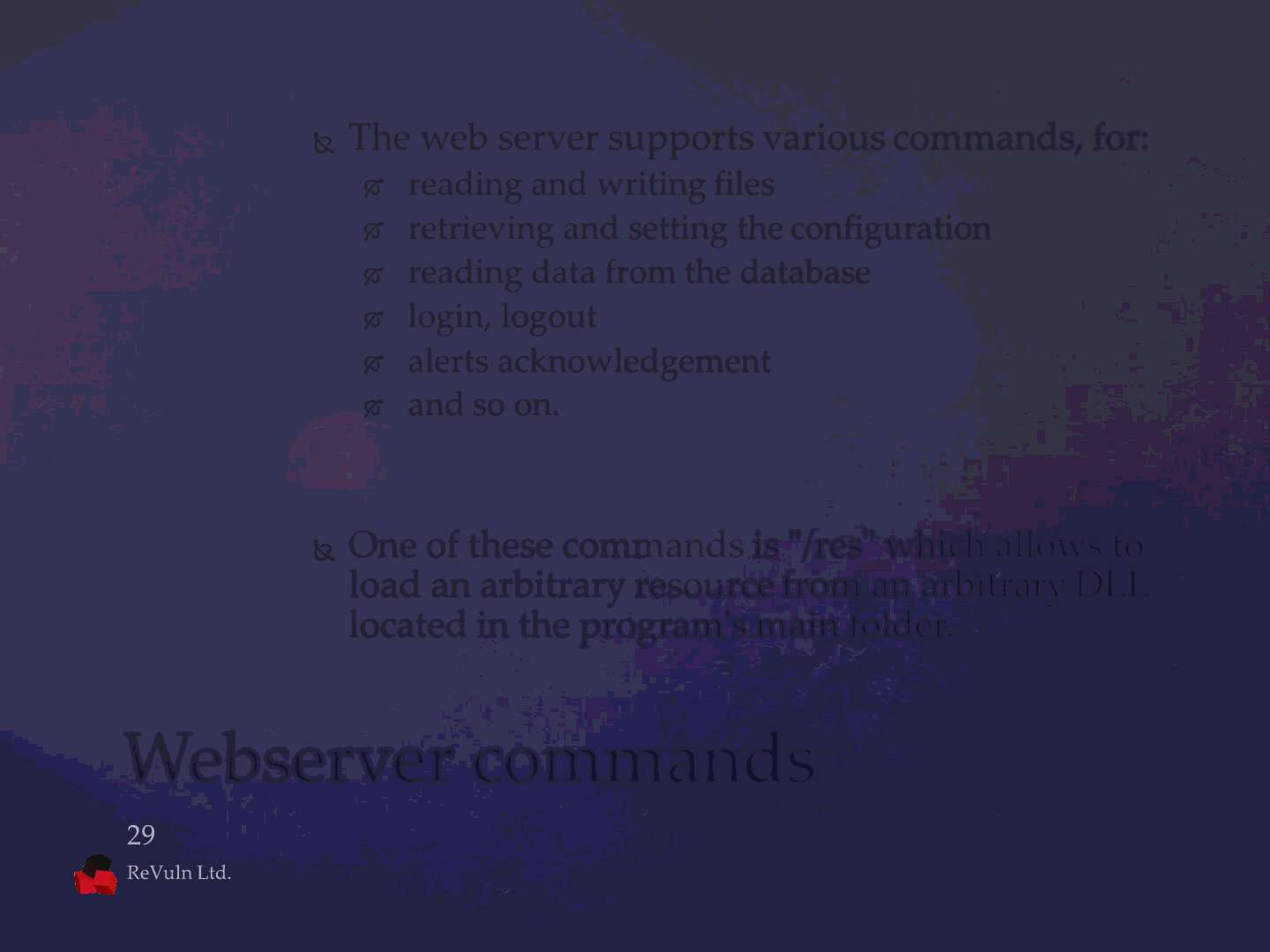
The web server supports various commands, for:
reading and writing files
retrieving and setting the configuration
reading data from the database
login, logout
alerts acknowledgement
and so on.
One of these commands is "/res" which allows to
load an arbitrary resource from an arbitrary DLL
located in the program's main folder.
Webserver commands
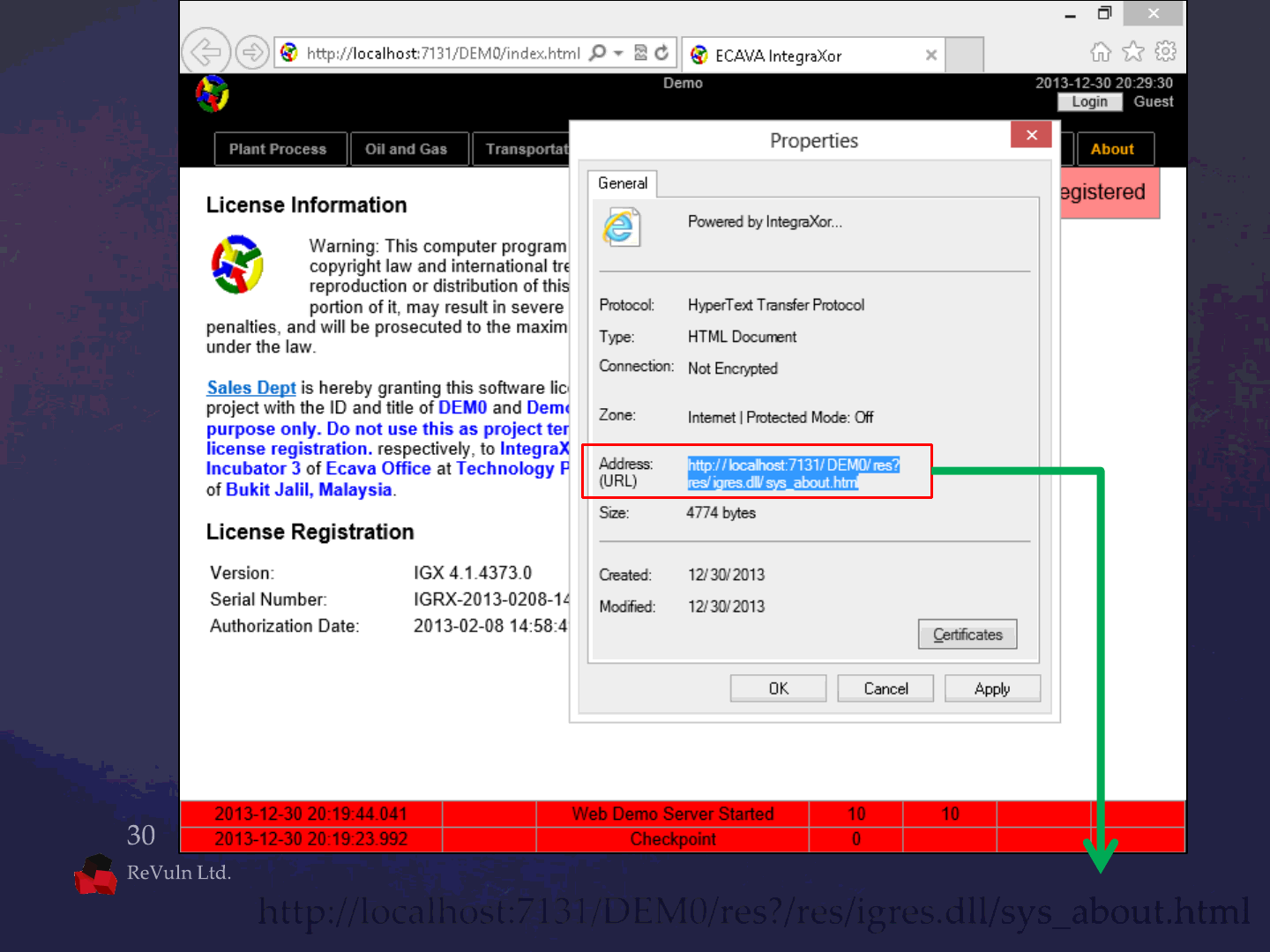
http://localhost:7131/DEM0/res?/res/igres.dll/sys_about.html

The syntax of the /res command is:
/PROJECT_NAME /res?
DLL_NAME
/RESOURCE_NAME
A stack buffer of 260 characters is used as
destination for containing RESOURCE_NAME
with the result of a stack based buffer-overflow
The /res command syntax
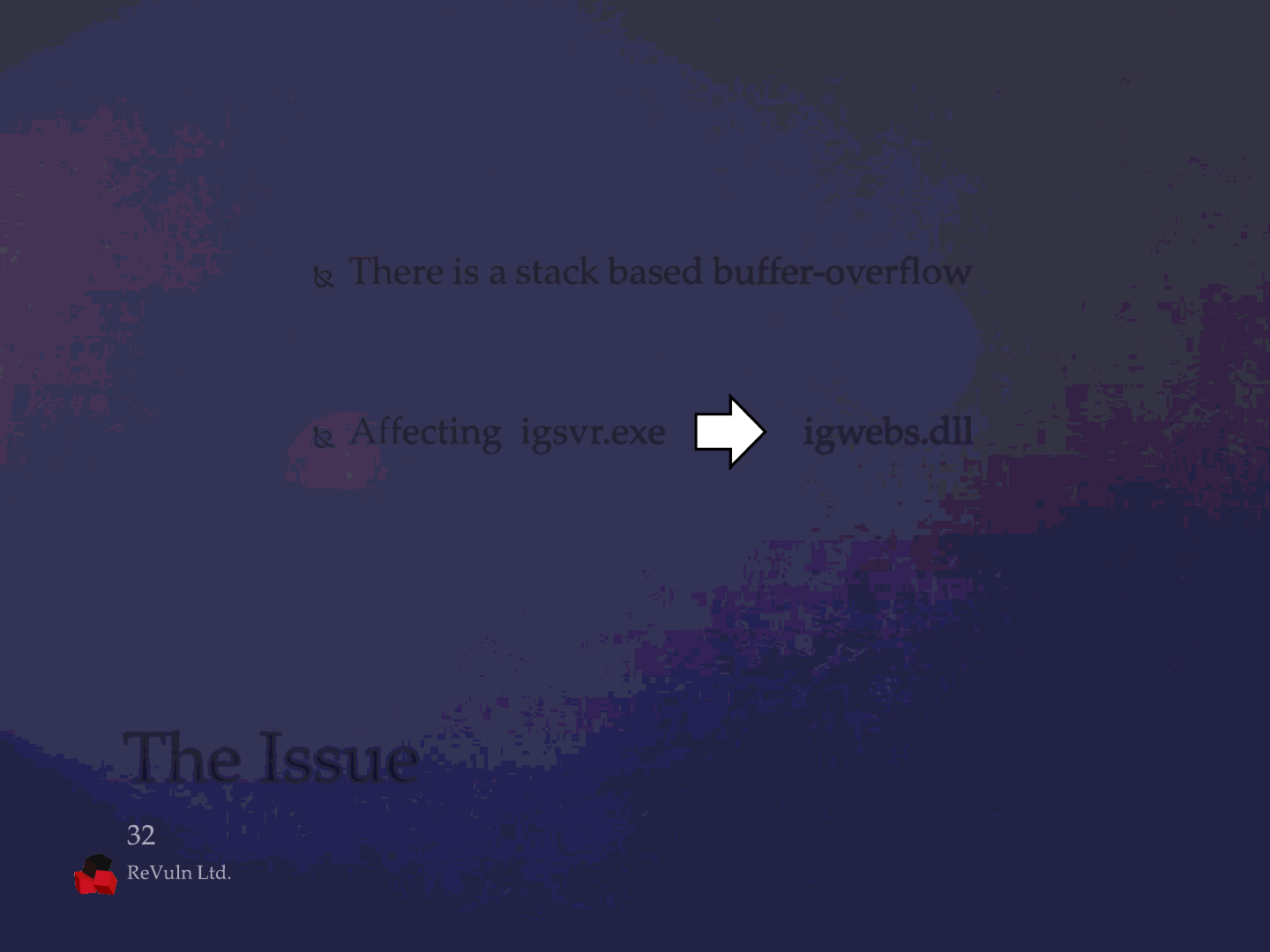
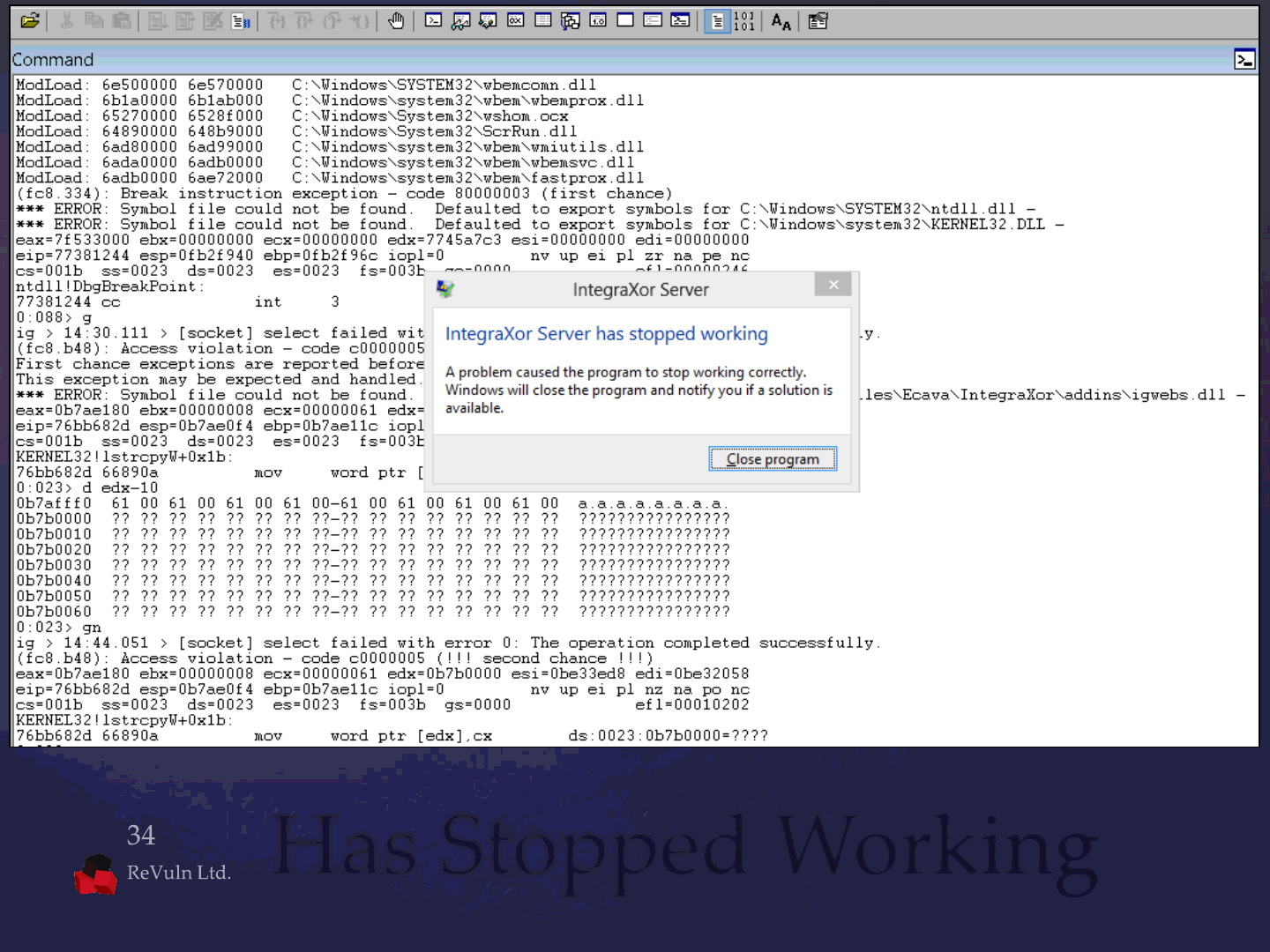
There is a stack based buffer-overflow
Affecting igsvr.exe igwebs.dll
The Issue

The pseudo-code of the /res handler is:
wchar_t buffer[260]; // MAX_PATH
...
buffer[0] = 0;
lstrcpyW(buffer, source); // vulnerability
SplitPath(buffer);
The /res handler (pseudo-code)
Has Stopped Working
DEMO TIME

There are several ways to fix this issue
Using an IPS/IDS
Binary Patch
In-Memory patch
Fixing the issue
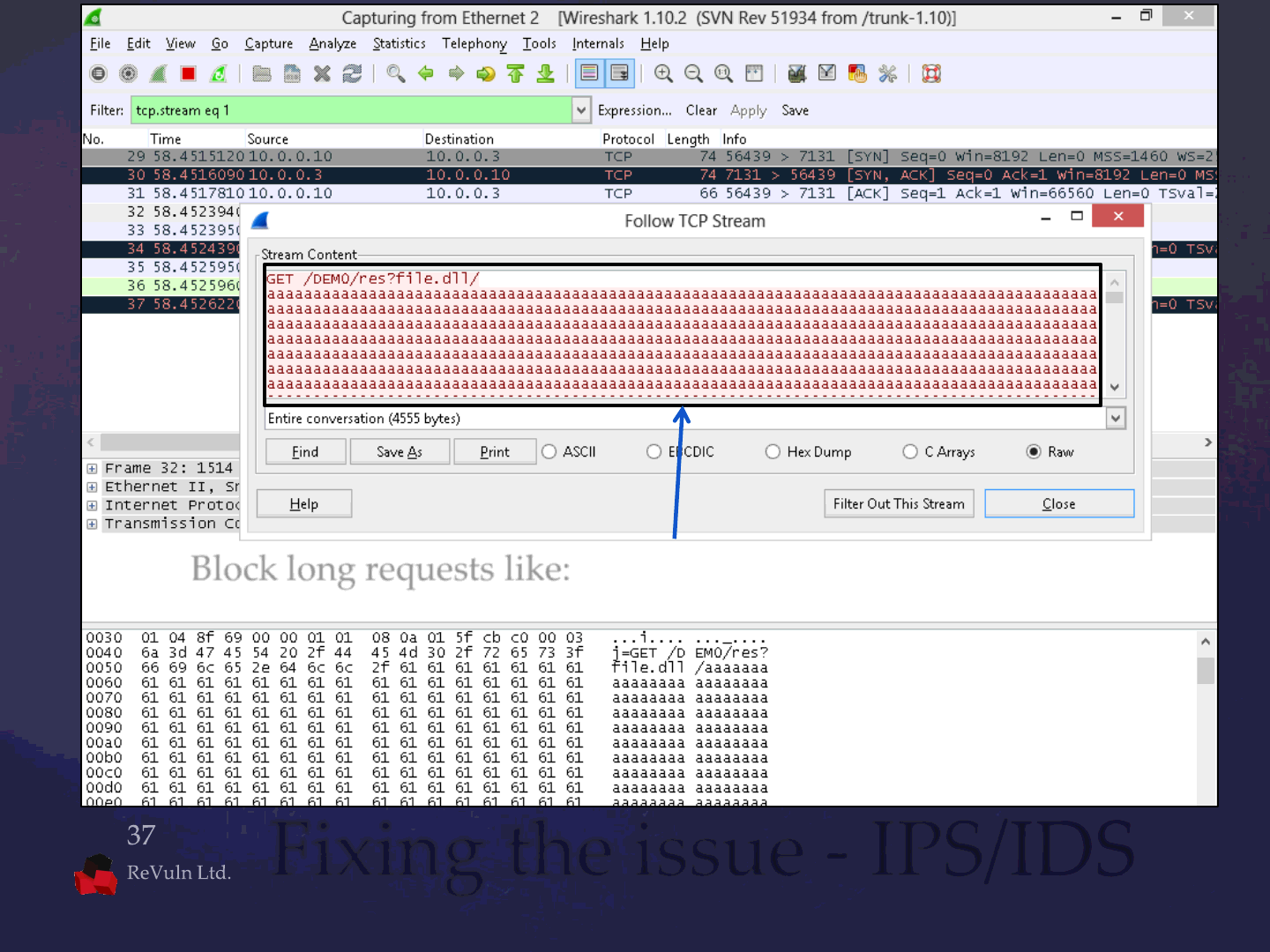
Fixing the issue - IPS/IDS
Block long requests like: /res?<some_dll>/<very_long_string>

There are multiple ways, for example:
replace lstrcpyW with StringCchCopyW
hook the vulnerable function
Fixing the issue - Binary Patch

Security Vulnerabilities
Uncovering new vulnerabilities
Final considerations
Agenda

Final Considerations - I
There are a lot of vulnerabilities affecting
SCADA/HMI solutions unknown to their
users/vendors (as shown in the previous slides)
Vendors usually need a long timeframe to fix the
issues, once these are reported to them
(sometimes over a year, even if the issues have
been reported to them)
Vendors may not fix the issues at all, and instead
provide their users with some recommendations
Final Considerations - II
There are only a few SCADA/HMI solutions
having an auto-update subsystem
99% of the cases an admin has to shutdown the
system, install the patch, and restart the system
This is NOT acceptable
The only way to circumvent this limitation is to
rely on solutions like the one we tested (DEMO’ed
during S4 2013) and included in SCADA shield:
Hot Patching
Issues fixed without downtime

Final Considerations - III
There is the need for users to explore and invest in
new defensive solutions such as SCADA shield
Solutions that don’t rely directly on the Vendors
Waiting days for a security patch can be acceptable
for Vendors, but can’t be acceptable for
SCADA/HMI users
revuln.com
info@revuln.com
twitter.com/revuln
Thanks
“Invincibility lies in the defense, the possibility of victory in the attack.”
ReVuln Ltd.
